Top Kali Linux tools For 2023
Overview
Kali Linux, a Debian-based Linux distribution, is maintained by Offensive Security. Mati Aharoni and Devon Kearns created it. Kali Linux is a specifically developed operating system for network analysts, penetration testers, or individuals who engage in cybersecurity and analysis.
Kali Linux is a popular operating system that is specifically crafted for the purposes of penetration testing and digital forensics. It comes bundled with powerful tools, making it an indispensable resource for security professionals, hackers, and enthusiasts.
Kali Linux is a popular Linux distribution created primarily for penetration testing, digital forensics, and ethical hacking. It comes pre-installed with a vast collection of powerful tools that enable security professionals to assess and secure computer systems. In this article, we will provide an overview of the Linux tools available in Kali Linux, highlighting their significance and applicability in cybersecurity.
Cheatsheet for Top Kali Linux Tools
Kali Linux offers various tools organized into different categories, catering to various aspects of penetration testing, vulnerability assessment, network analysis, forensics, and more.
This article will explore a comprehensive cheat sheet of important Kali Linux tools, their descriptions, and how to utilize them in various scenarios effectively.
-
Nmap:
Nmap (Network Mapper) is a powerful and versatile scanning tool for exploration and security auditing. It lets users discover hosts, services, and open ports and perform vulnerability scanning. You can use ping to find the IP address of a webpage. To scan a target use: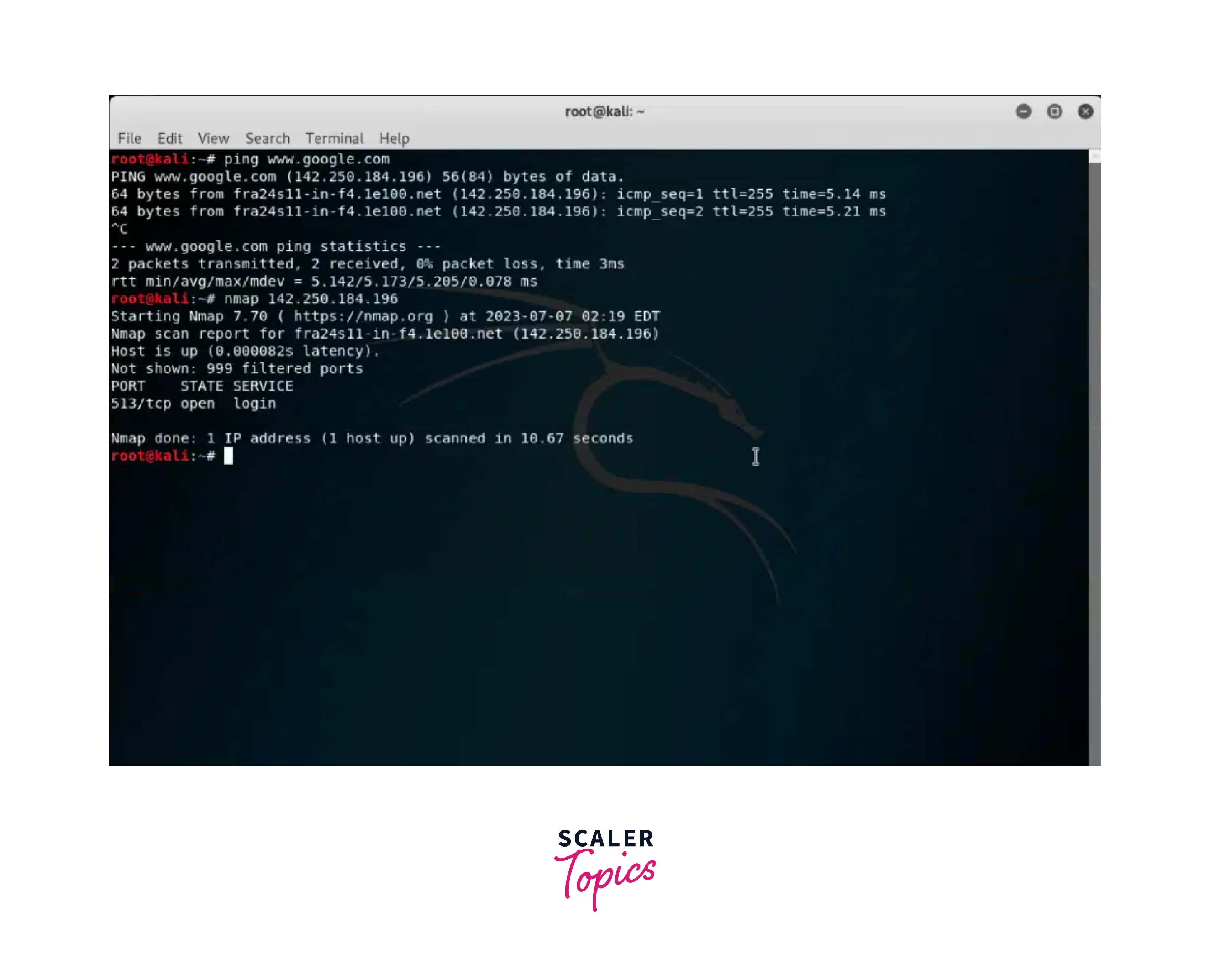
-
Metasploit Framework:
It is a broadly used penetration testing tool that provides many exploits, payloads, and auxiliary modules. The tool enables security experts to discover and capitalize on weaknesses within target systems. Launch the Metasploit console using the following command: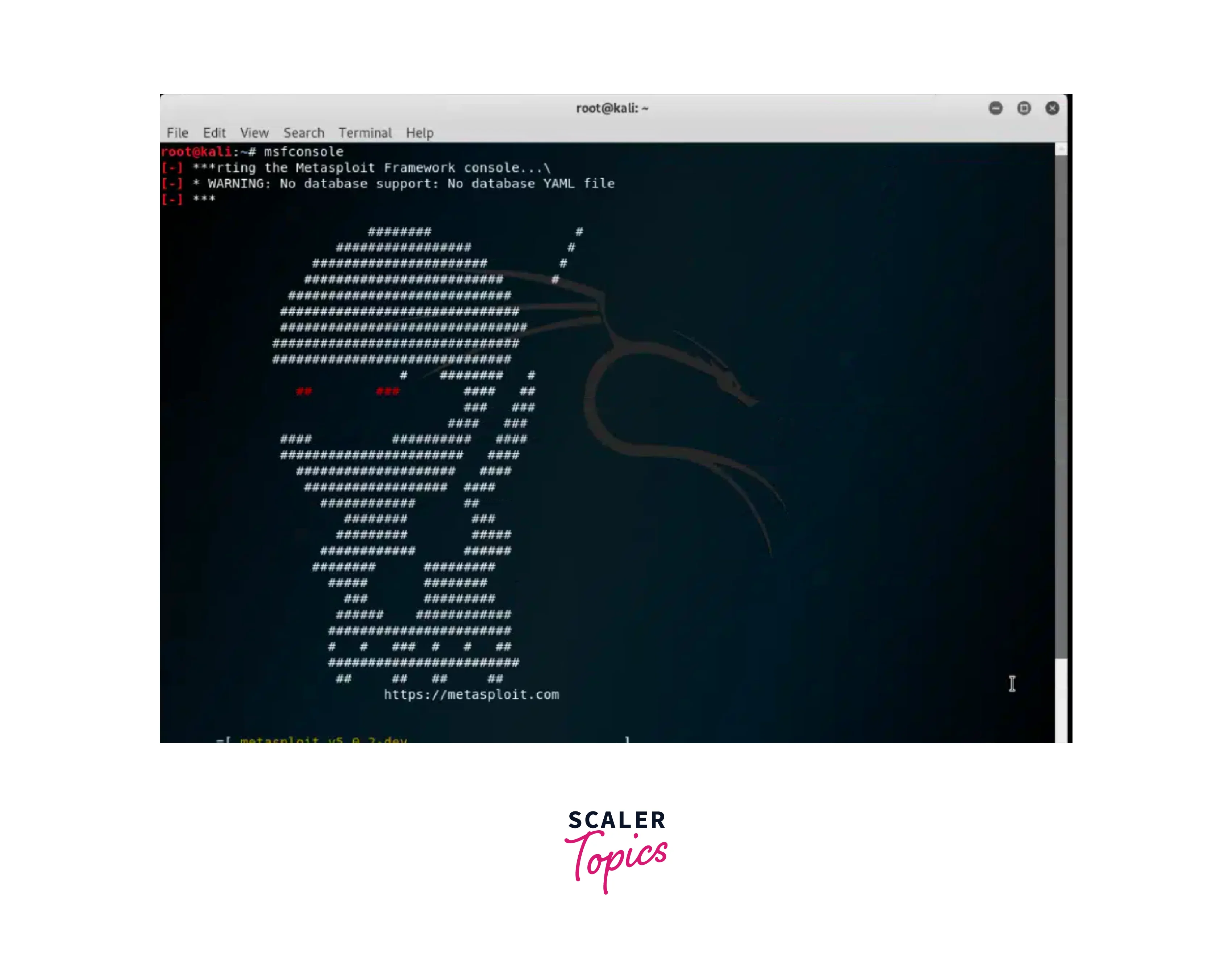
-
Wireshark:
Wireshark is a network protocol analyzer that allows for real-time capture and analysis of network data. It helps troubleshoot network issues, examine packets, and detect potential security threats. Launch Wireshark with root privileges using: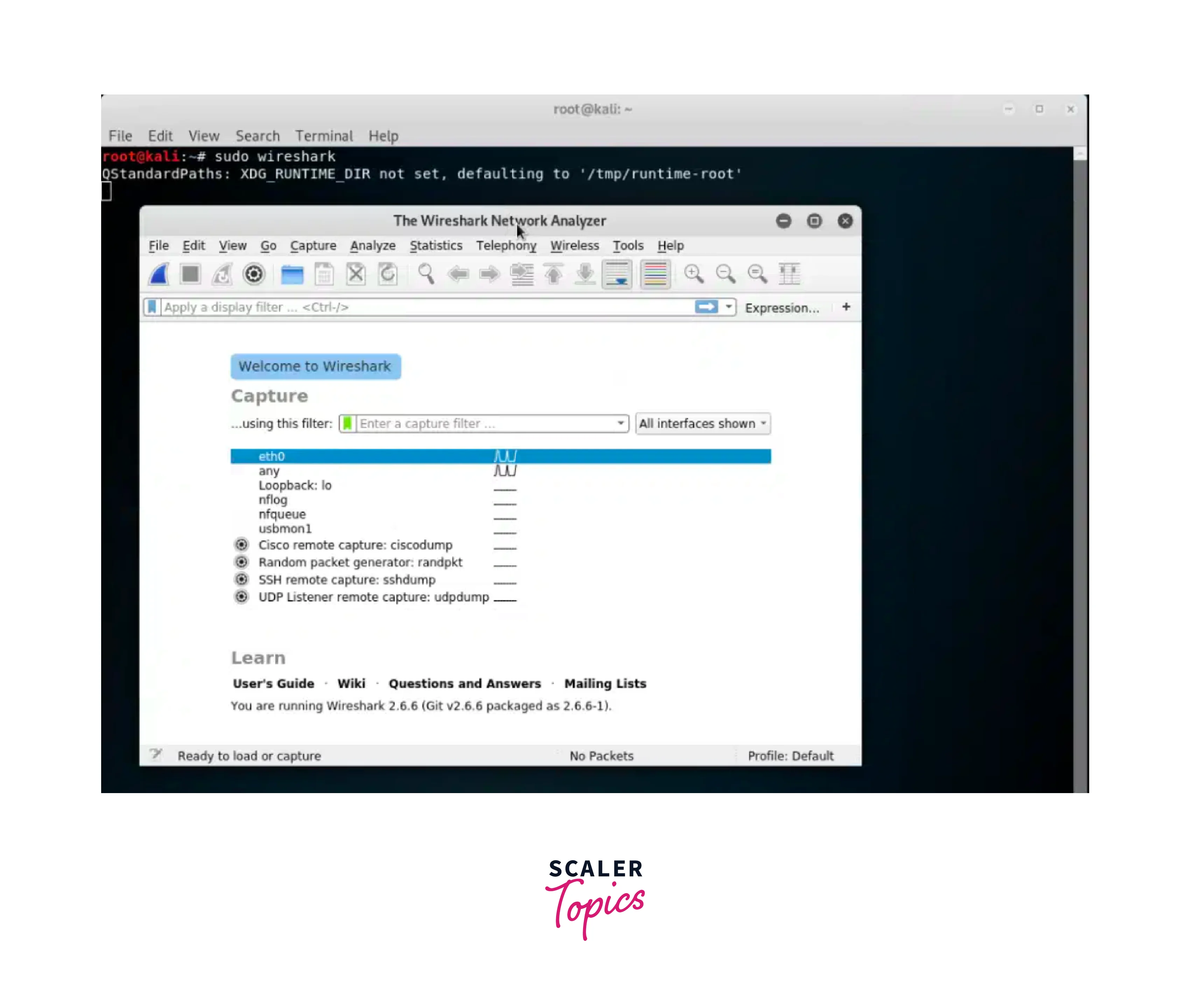
-
Aircrack-ng:
Aircrack-ng is a powerful suite of tools used for wireless network auditing and penetration testing. It allows for capturing and analyzing wireless packets, cracking WEP and WPA/WPA2-PSK keys, and conducting various wireless attacks. Use the following command to use aircrack:
-
Burp Suite:
Burp Suite is a comprehensive web application security testing platform. It includes a proxy server, scanner, intruder, repeater, and other modules for various security testing tasks. Launch Burp Suite using the following command: -
John the Ripper:
John the Ripper is a robust password-cracking tool that detects weak passwords. It supports various hash types and offers various cracking modes, such as dictionary attack, brute force, and hybrid attack. To start using John the Ripper, use the following command: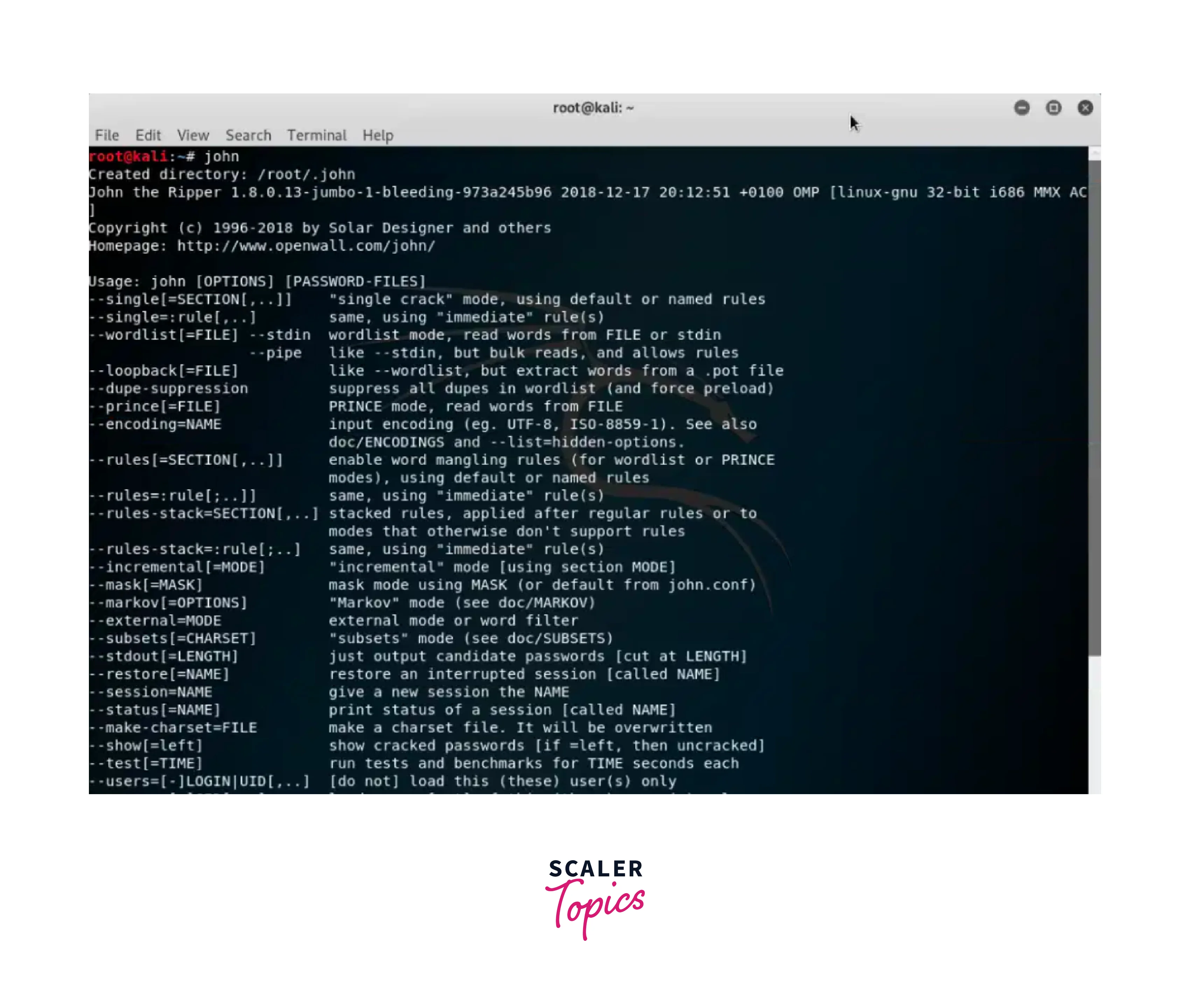
-
Nikto:
Nikto is an open-source web server scanner to detect potential vulnerabilities and misconfigurations. It performs comprehensive tests against web servers, highlighting security flaws and providing recommendations for remediation. Execute Nikto scans using the following command: -
Hydra:
Hydra is a powerful online password-cracking tool that supports various protocols, including HTTP, FTP, SSH, and more. It allows users to automate password-guessing attacks, helping identify weak credentials. Use the following command to execute a basic password-cracking attempt: -
SQLmap:
SQLmap is a popular automated SQL injection and database takeover tool. It assists in detecting and exploiting SQL injection vulnerabilities, enabling attackers to gain unauthorized access to databases. Use the following command to initiate a SQL injection attack: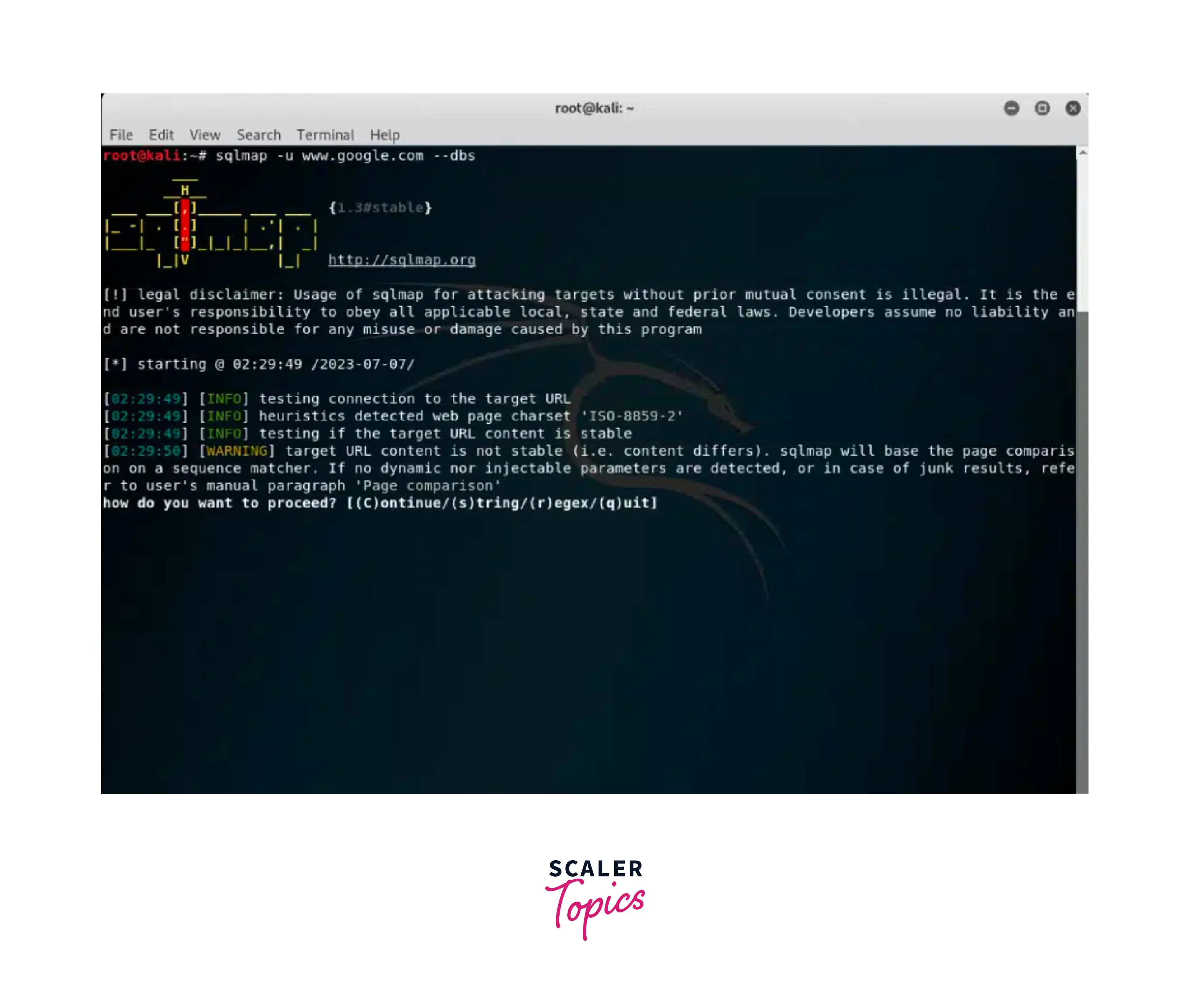
-
OpenVAS:
OpenVAS (Open Vulnerability Assessment System) is a powerful vulnerability scanner that helps identify security flaws in target systems. It scans for known vulnerabilities, misconfigurations, and potential security risks. Launch OpenVAS using the following command: -
Hashcat:
Hashcat is a high-speed password recovery tool for cracking password hashes. It supports various hash types and provides various attack modes, including dictionary, brute force, and mask attacks. To crack password hashes, use the following command: -
Maltego:
Maltego is a powerful intelligence and forensics tool for gathering and analyzing information about individuals, organizations, and networks. It visualizes relationships and dependencies between entities, aiding in identifying potential threats. Launch Maltego using the following command: -
BeEF:
BeEF (Browser Exploitation Framework) is a penetration testing tool focusing on web browser vulnerabilities. It allows security professionals to assess the security posture of web applications by exploiting client-side vulnerabilities. Start BeEF using the following command: -
Social Engineering Toolkit (SET):
The Social Engineering Toolkit (SET) is a comprehensive toolkit for social engineering attacks. It provides a range of attack vectors, including spear-phishing emails, malicious websites, and more. Launch SET using the following command: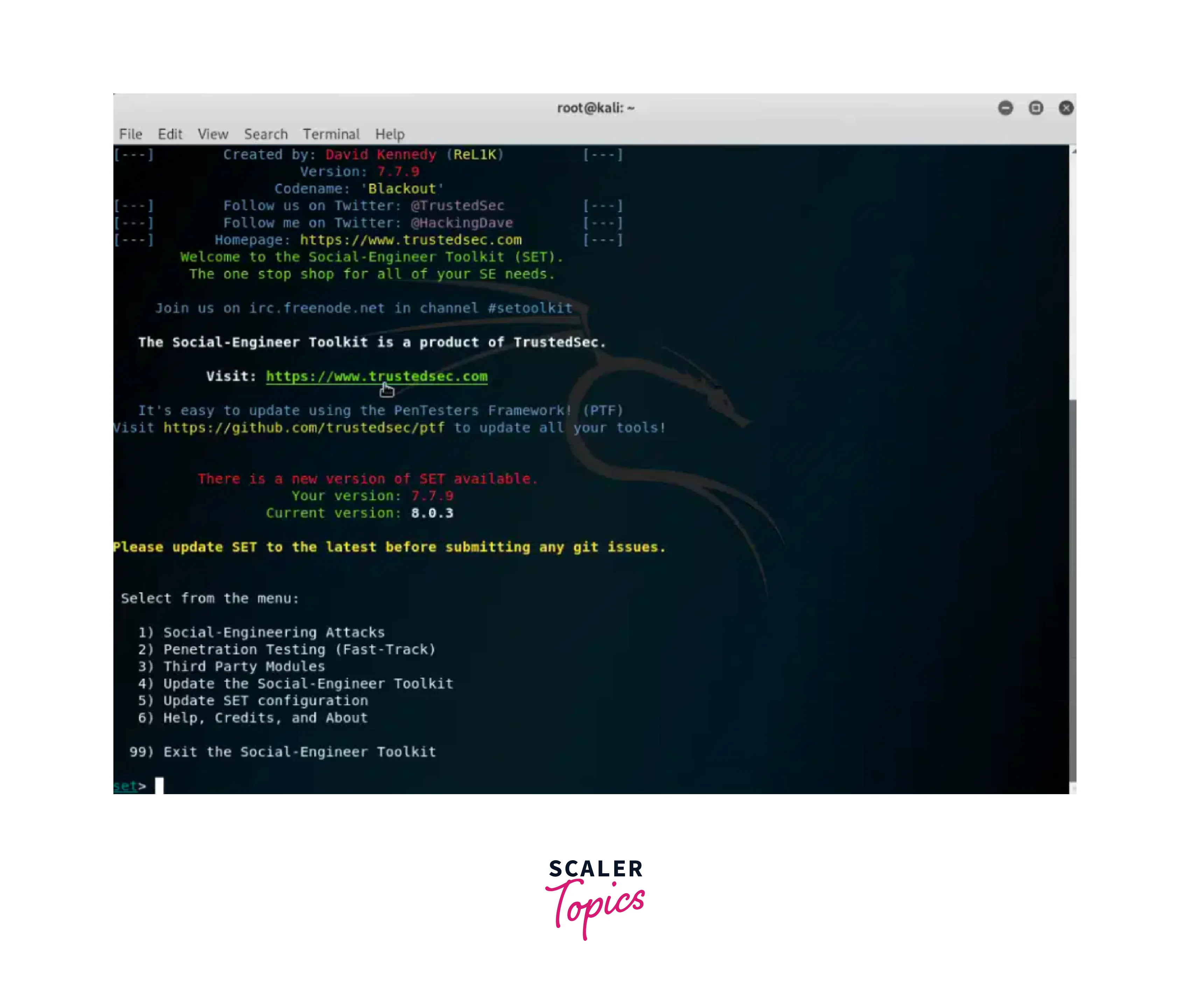
-
Autopsy:
Autopsy is a digital forensics tool for gathering information from forensics. In other words, this program is used to study files or logs to determine what was done to the system. Additionally, it can be utilized for the recovery of files from a memory card or a USB flash drive. Use the following command to use autospy: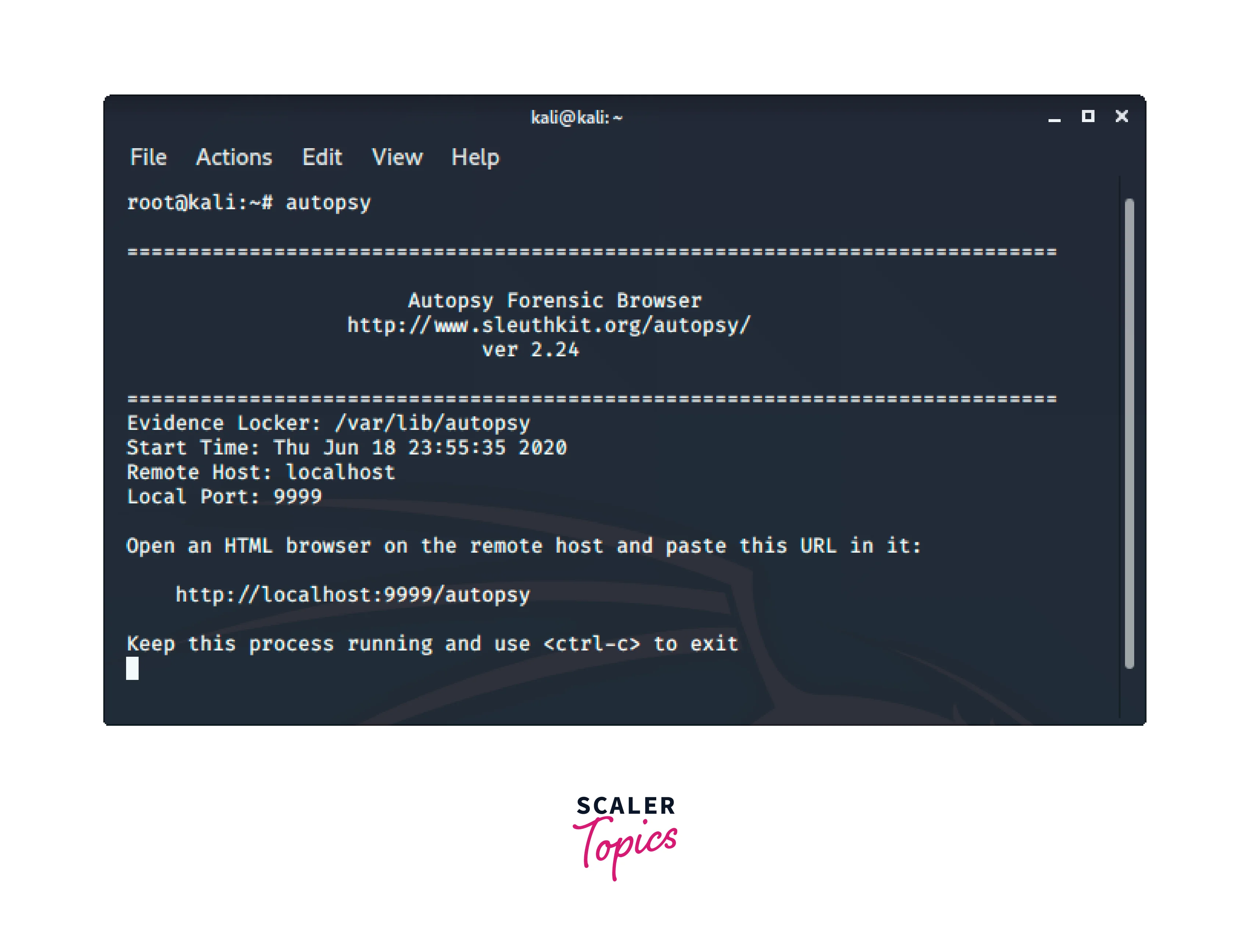 Now visit http://localhost:9999/autopsy to use the tool.
Now visit http://localhost:9999/autopsy to use the tool.
-
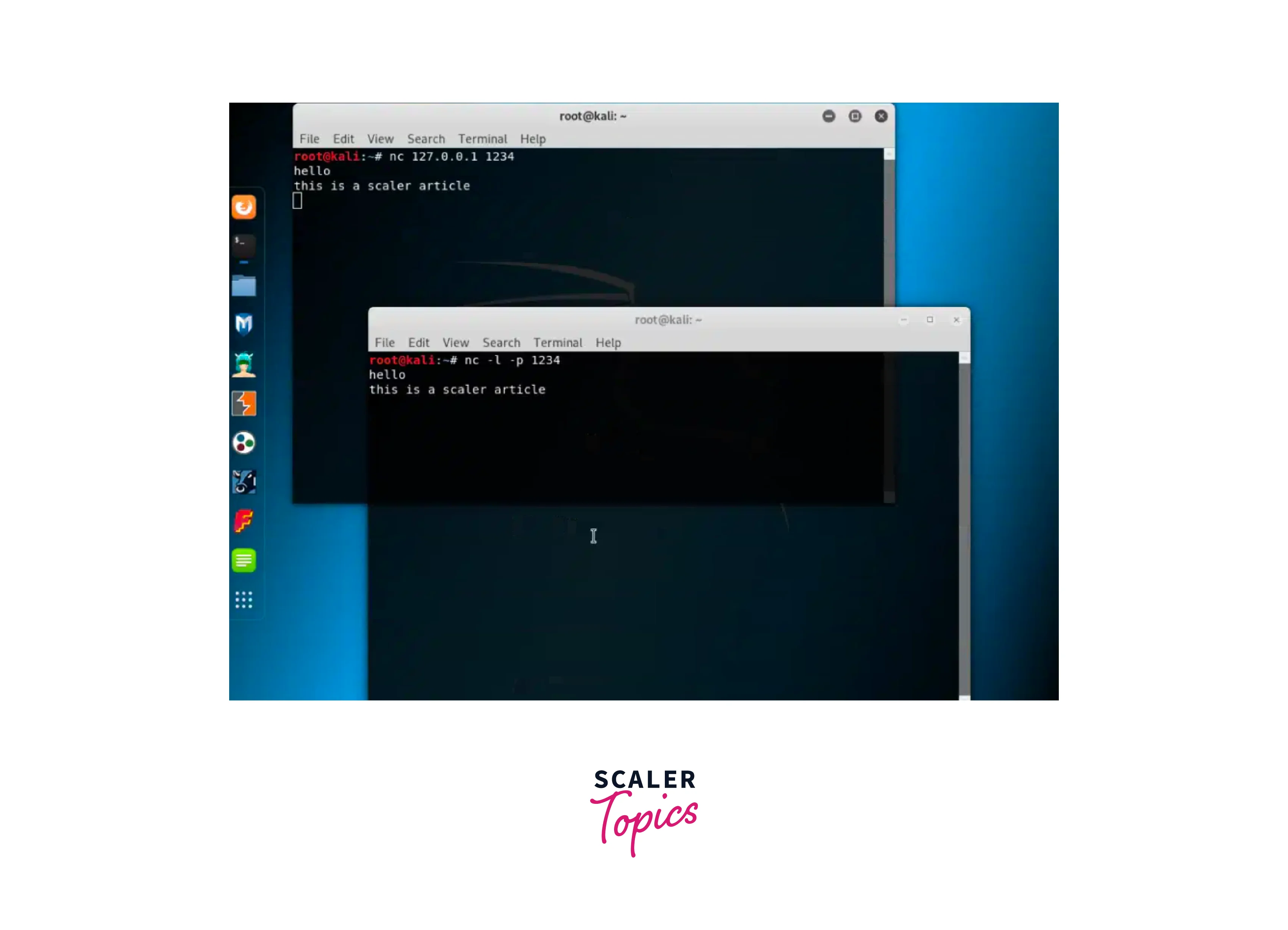
Netcat:
Netcat is a networking utility that may be used to interact with ports and perform tasks such as port scanning, port listening, and port redirection. This command serves multiple purposes in network debugging and network daemon testing. It is often referred to as the networking equivalent of a versatile tool, similar to a Swiss army knife. It has the capability to perform various operations such as TCP, UDP, or UNIX-domain socket operations, as well as establishing remote connections, among other functionalities. To use netcat, follow these steps:- To use netcat, simply type nc or netcat into the terminal.
- Type the following commands in two distinct terminals to do port listening.
-
THC-Hydra:
THC-Hydra is a powerful online password-cracking tool that supports numerous protocols, including email, FTP, SSH, and more. It automates the process of password guessing by conducting brute force and dictionary attacks. Use the following command to launch a password-cracking attempt: -
Fluxion:
Wi-Fi is becoming more widespread by the year, making it a more appealing target for hackers. As a result, pen testers must be able to test Wi-Fi networks for security flaws. Fluxion is a wireless network analyzer that specializes in MITM WPA attacks and allows you to scan wireless networks. Fluxion is used by pen testers to look for security holes in business and personal networks. Fluxion, on the other hand, does not launch time-consuming brute force cracking efforts like other Wi-Fi cracking tools. Fluxion instead initiates an MDK3 procedure that drives all users on the targeted network to lose or deauthenticate their credentials. After that, the user is requested to join a bogus access point, which necessitates inputting the Wi-Fi password. The application then reports the password to the pen tester in order to get access.
Kali Linux is renowned for its extensive collection of tools tailored for penetration testing and security assessments. In this cheat sheet, we explored several essential Kali Linux tools, providing descriptions and instructions on how to use them effectively. These tools empower security professionals and enthusiasts to identify vulnerabilities, assess network security, and strengthen defenses against potential threats. Remember to use these tools responsibly and legally within ethical hacking and security testing contexts.
Conclusion
- Tools like `top, htop, and sar`` provide insights into system performance, resource usage, and process monitoring.
- Network monitoring tools such as ifconfig, netstat, and ip help analyze network interfaces, connections, and traffic.
- Nano is a user-friendly text editor suitable for beginners or those who prefer a simpler interface.
- Nmap, a powerful network scanning tool, helps in network exploration and security auditing.
- Wireshark is a versatile network protocol analyzer for capturing and analyzing network traffic.
- Aircrack-ng, Burp Suite, and Metasploit Framework are essential tools for wireless network auditing, web application security testing, and penetration testing, respectively.
- OpenVAS is a robust vulnerability scanner that helps identify security flaws in target systems.
