A wireless ad hoc network (WANET) or mobile ad hoc network (MANET) is a type of wireless network that is decentralized. Since it doesn’t rely on a pre-existing infrastructure, like routers in wired networks or access points in wireless networks, the network is ad hoc. Instead, each node takes part in routing by sending data to other nodes, therefore the choice of which nodes provide data is made dynamically based on the connectedness of the network and the routing algorithm being used. Ad hoc is a communication mode (setting) in the Windows operating system that allows machines to interact directly without using a router.
What is Mobile Ad hoc Network (MANET)?
MANET is an acronym for Mobile Adhoc Network, also known as a wireless Adhoc network or Adhoc wireless network, which is a routable networking environment built on top of a Link Layer ad hoc network. They are made up of a collection of mobile nodes that are wirelessly connected in a self-configuring, self-healing network with no fixed infrastructure. Because the network architecture changes regularly, MANET nodes are allowed to move at random. Each node acts as a router, forwarding traffic to other nodes in the network.
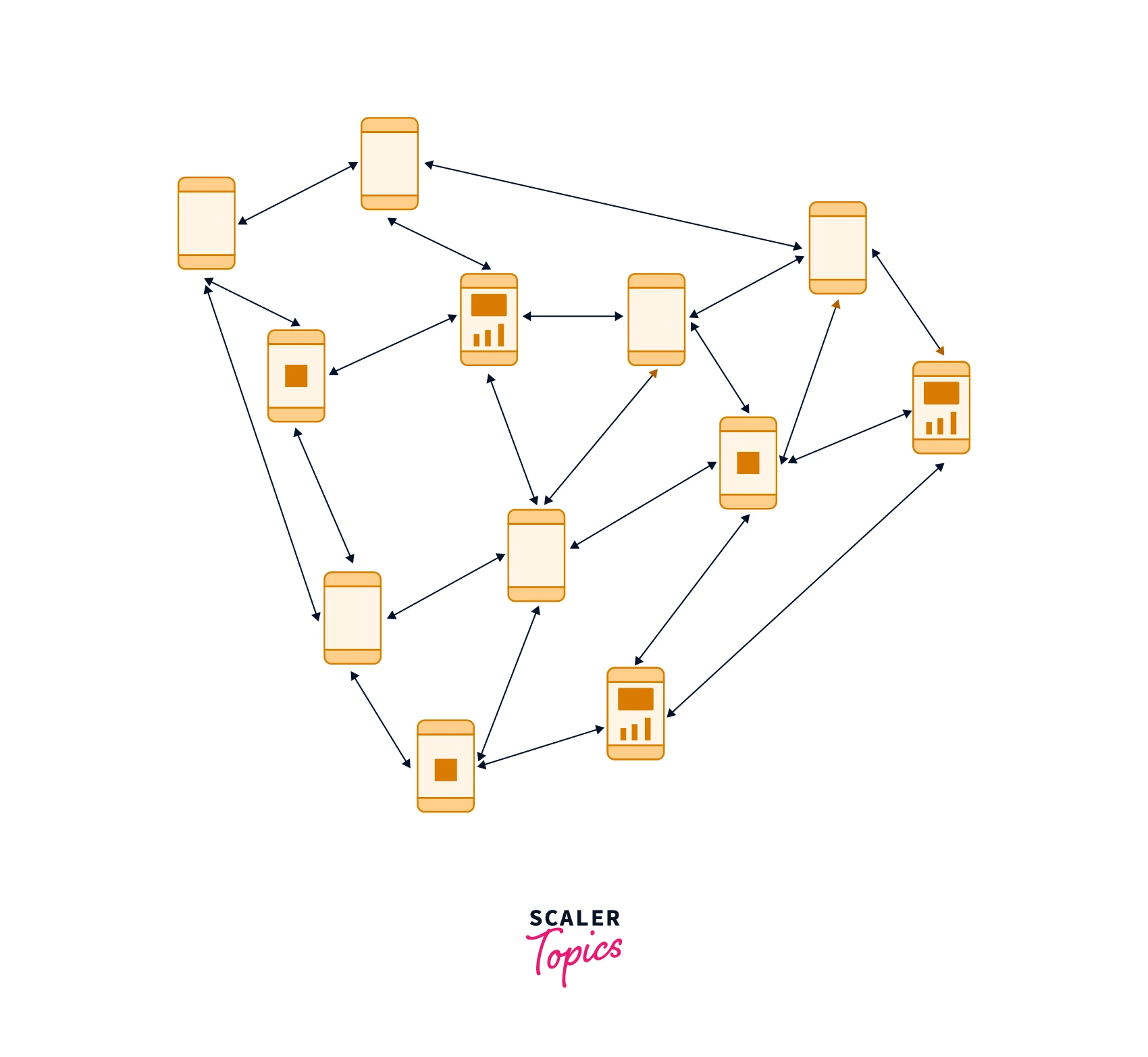
MANETs can function alone or as part of a broader internet. With the inclusion of one or more distinct transceivers between nodes, they establish a highly dynamic autonomous topology. The fundamental difficulty for the MANET is to equip each device with the necessary information to route traffic correctly. MANETs are peer-to-peer, self-forming, self-healing networks that typically connect at radio frequencies (30MHz-5GHz). This can be employed in road safety in various ways, including sensors for the environment, the house, health, disaster relief operations, air/land/navy defense, weaponry, robotics, and so on.
Ad hoc is a communication mode (setting) in the Windows operating system that allows machines to interact directly without using a router. Wireless MANETs (mobile ad hoc networks) are self-configuring, dynamic networks with free-moving nodes.
History on Packet Radio
Now let’s have a look at the detailed history of packet radio.
- The first wireless data network, known as PRNET, was financed by the
DARPA (Defense Advanced Research Projects Agency)in the early1970s. Beranek, Bolt, and Newman Inc. (BBN)andSRI International created, manufactured, and tested these early systems.Robert Kahn,Jerry Burchfiel, andRay Tomlinsonwere among the experimenters.- Similar research with the
x25 protocolwas conducted in the amateur radio community. These early packet radio services predated the Internet and were a driving force for developing the original Internet Protocol suite. - The
Survivable Radio Network (SURAN)project, which took place in the 1980s, was a later DARPA experiment. The Near-term digital radio, a successor to these systems, was introduced in the mid-1990s for the US Army and other nations. - The third wave of academic and research activity began with the introduction of
low-cost 802.11radio cards for personal computers in themid-1990s. Current wireless ad hoc networks are primarily intended for military use. The following issues affect packet radios:- Bulky elements
- Sluggish data rates
- Inability to maintain links when mobility is high.
- The idea stalled until the early 1990s when wireless ad hoc networks were developed.
MANETs Features
Some of the significant features of the MANETs network are given below:
- No hardware or physical infrastructure is involved; the mobile devices engaged communicate and send data to each other autonomously.
- It is self-repairing.
- It can be configured automatically.
- These networks are also known as
WANET (Wireless Ad-hoc Network)on fly networks or spontaneous networks. - Data packets are transferred to another device or node by each device acting as a router.
How Do MANETs (Mobile Ad hoc Network) Work?
The working of MANETs is explained below:
- Work exclusively as an individual or in a group within a vast network, such as the Internet.
- Hardware and access points are absent.
- Direct and independent interaction between mobile devices
- The devices begin to look for one another and start communicating.
- When a node is far away, the nodes between the source and destination nodes serve as routers and send data one at a time until it reaches the destination node.
- Devices can dynamically add or remove nodes at any moment, allowing them to join or leave the network.
- As they do for power, the devices have their energy reserves.
Early Work on MANET
Let’s look at the early works done in the mobile ad hoc networks field.
- Since the middle of the
1990s, the popularity of laptops and802.11 (Wi-Fi)wireless networking has madeMANETs (Mobile Ad hoc Networks)a widely researched topic. - In many academic papers, protocols, and their capabilities are assessed under the assumption of varying degrees of mobility within a confined space, typically with all nodes located within a short hop of one another. The effectiveness of various protocols is then assessed using metrics like:
- Packet drop rate
- Network speed
- End-to-end delay in packets
- Routing protocol overhead
- Scaling capability and so on.
Chai Keong Tohof Cambridge University andCharles Perkinsof SUN Microsystems USA started working independently in the early1990son a new Internet, one that was a wireless ad hoc network.- Perkins was working on the dynamic, addressing challenges. Toh worked on a new routing protocol called
associativity-based routing (ABR). Perkins eventually proposedDSDV (Destination Sequence Distance Vector routing), which is based on distributed distance vector routing. - Toh’s solution was based on on-demand routing, which means that routes are discovered in real time as needed.
ABRwas submitted to theInternet Engineering Task Forceas RFCs. - Associativity-based routing was successfully integrated into the Linux operating system on the
Lucent WaveLAN 802.11a enabled laptops, and a viable ad hoc mobile network was demonstrated in1999. Following that, another routing system,AODV, was devised, proved, and implemented in2005. - In 2007,
Dynamic Source Routing(DSR)was proposed byDavid JohnsonandDave Maltz.
Applications of MANET
Industrial and commercial applications, including cooperative, and mobile data interchange, are some particular uses of ad hoc networks. Military networking requirements for reliable, IP-compliant data services within mobile wireless communication networks are numerous today and in the future, and many of these networks are made up of highly dynamic autonomous topological segments. Mobile ad hoc networks’ advanced capabilities, such as data rates appropriate for multimedia applications, global roaming, and coordination with other network architectures, are opening up new possibilities for applications.
- Wireless mesh networks:- A
wireless mesh network (WMN)is a mesh network formed by connectingwireless access point (WAP)nodes put at each network user’s location. The networking infrastructure is decentralized and streamlined because each node needs to send as far as the next node. Wireless Mesh Network may or may not be connected to the internet. Wireless mesh networks, which can alternatively be classified as a type ofwireless ad hoc network (WANET), are frequently used for the following purposes:- Connecting sensors, security systems, smart appliances, and monitoring systems to the
Internet of Things (IoT). - Access to public Wi-Fi supplied by cities and municipalities.
- Establishing networks in developing communities when there is no internet wiring infrastructure.
- Wi-Fi networks in the home.
- Wi-Fi and networking in mobile environments, such as construction sites.
- Connecting sensors, security systems, smart appliances, and monitoring systems to the
- Wireless Sensor Network:- Sensors are helpful devices that collect data about specific parameters, such as noise, temperature, humidity, pressure, etc. Sensors are increasingly being wirelessly connected to allow for large-scale sensor data collection. We can use analytics processing to make sense of a significant sensor data sample. Wireless sensor network connectivity is based on the concepts of wireless ad hoc networks, as sensors may now be deployed without fixed radio towers and establish networks on the fly. One of the early initiatives at
UC Berkeleywas “Smart Dust,” in which small radios were used to connect smart dust.Mobile wireless sensor networks (MWSNs)have lately gained academic attention. - Military applications:- Ad hoc/sensor networks are ideal for battlefield management since many military applications require an on-the-fly communications setup.
- Telemedicine:- When assisting a car accident victim in a remote area, a paramedic must access medical records (such as X-rays) and may require video conference support from a surgeon for an emergency intervention. In fact, the paramedic might need to send the victim’s X-rays and results of another diagnostic test straight from the accident scene to the hospital.
- Disaster management applications:- These can happen, for instance, when there is a natural disaster and the entire communication infrastructure is in chaos. Communication needs to be restored as soon as possible.
- Tele-geoprocessing application:- A new class of application known as tele-geo processing is made possible by the integration of GPS,
GIS (Geographical Information Devices), and high-capacity wireless mobile systems. - Education via the Internet:- Educational opportunities are available on the Internet or in remote places due to the practical impossibility of providing pricey last-mile wireline internet access to all users in these areas.
- Virtual Navigation:- A big metropolis’ physical properties, including its buildings, streets, and other physical features, are graphically represented in a remote database. Additionally, they might be able to “virtually” view a building’s interior layout, including a strategy for an emergency evacuation, or locate potential places of interest.
- Vehicular area network(VANETs):- This is a growing and precious ad-hoc network application for providing emergency services and other information. This works equally well in both urban and rural settings. The fundamental and necessary data interchange in a specific circumstance.
Characteristics of MANET
Let’s have a look at some of the characteristics of MANET:
- Dynamic topologies:- As nodes are free to move in any direction, the network topology can alter at any time and is mainly composed of bidirectional links. A unidirectional link may sometimes exist when the transmission power of two nodes differs.
- Bandwidth-constrained and variable capacity links:- Wireless links continue to have much lesser capacity than infrastructure networks.
- Energy-constrained operation:- Batteries or other non-renewable sources may power some or all of the nodes in a
MANET. Energy conservation may be the most essential system design optimization requirement for these nodes or devices. - Limited physical security:-
MANETsare generally more vulnerable to physical security threats than wireline networks. The increased risk of eavesdropping, spoofing, anddenial of service (DoS)attacks should be carefully examined. Many existing link security solutions are frequently used within wireless networks to reduce security concerns. - Less Human Intervention:- They require minimal human involvement to configure the network, hence they are dynamically autonomous.
Advantages of MANETs
- Each node can act as both a router and a host, demonstrating its autonomous nature.
- Separation from the central network administration.
- Highly expandable and suitable for the addition of new network hubs.
- Nodes that self-configure and self-heal do not require human involvement.
- In
MANETsinfrastructure is not required because it is a decentralized network. - Due to the multi-hop approach in which information is conveyed, decentralized networks are often more robust than centralized networks. In a cellular network, for example, if a base station fails, coverage is lost; however, the likelihood of a single point of failure in a
MANETis greatly decreased because data can travel via several paths. - Other advantages of
MANETsover fixed-topology networks include flexibility (mobile devices can be used to form an ad hoc network anywhere), scalability (you can quickly add more nodes to the network), and cheaper management expenses (no need to build infrastructure first).
Disadvantages of MANETs
- There are no authorization facilities.
- Resources are limited due to various constraints such as noise, interference situations, and so on.
- High latency means data is transferred between two sleeping nodes with a significant delay.
- Due to inadequate physical security, they are more vulnerable to attacks.
Conclusion
- The Mobile Ad hoc Network is made up of a collection of mobile nodes that are wirelessly connected in a self-configuring, self-healing network with no fixed infrastructure.
- Each node in a Mobile Ad hoc Network, takes part in routing by sending data to other nodes, therefore the choice of which nodes provide data is made dynamically based on the connectedness of the network and the routing algorithm being used.
- Each node in a MANET acts as a router, forwarding traffic to other nodes in the network.
- The first wireless data network, known as PRNET, was financed by the
DARPA (Defense Advanced Research Projects Agency)in the early1970s. - Mobile ad hoc networks’ advanced capabilities, such as data rates appropriate for multimedia applications, global roaming, and coordination with other network architectures, are opening up new possibilities for applications. Some of the popular applications are:
- Wireless mesh networks
- Wireless Sensor Network
- Military applications
- Telemedicine
- Disaster management applications
- Virtual Navigation
- Some important characteristics of MANET are:
- Dynamic topologies.
- Bandwidth-constrained and variable capacity links.
- Energy-constrained operation.
- Limited physical security.
- Less Human Intervention
