Whenever a sender and receiver have a radical link to transmit data/information packets, the data link management is enough to handle the channel. Assume there is no committed path to communicate the data between 2 devices. In this case, with multiple access protocols, the channel at the same time transmits the information over the channel. It is going to produce concussion and cross-talk. Therefore, multiple access protocols are needed to scale back the collision and avoid disturbance within the channels.
:::
:::section{.main}
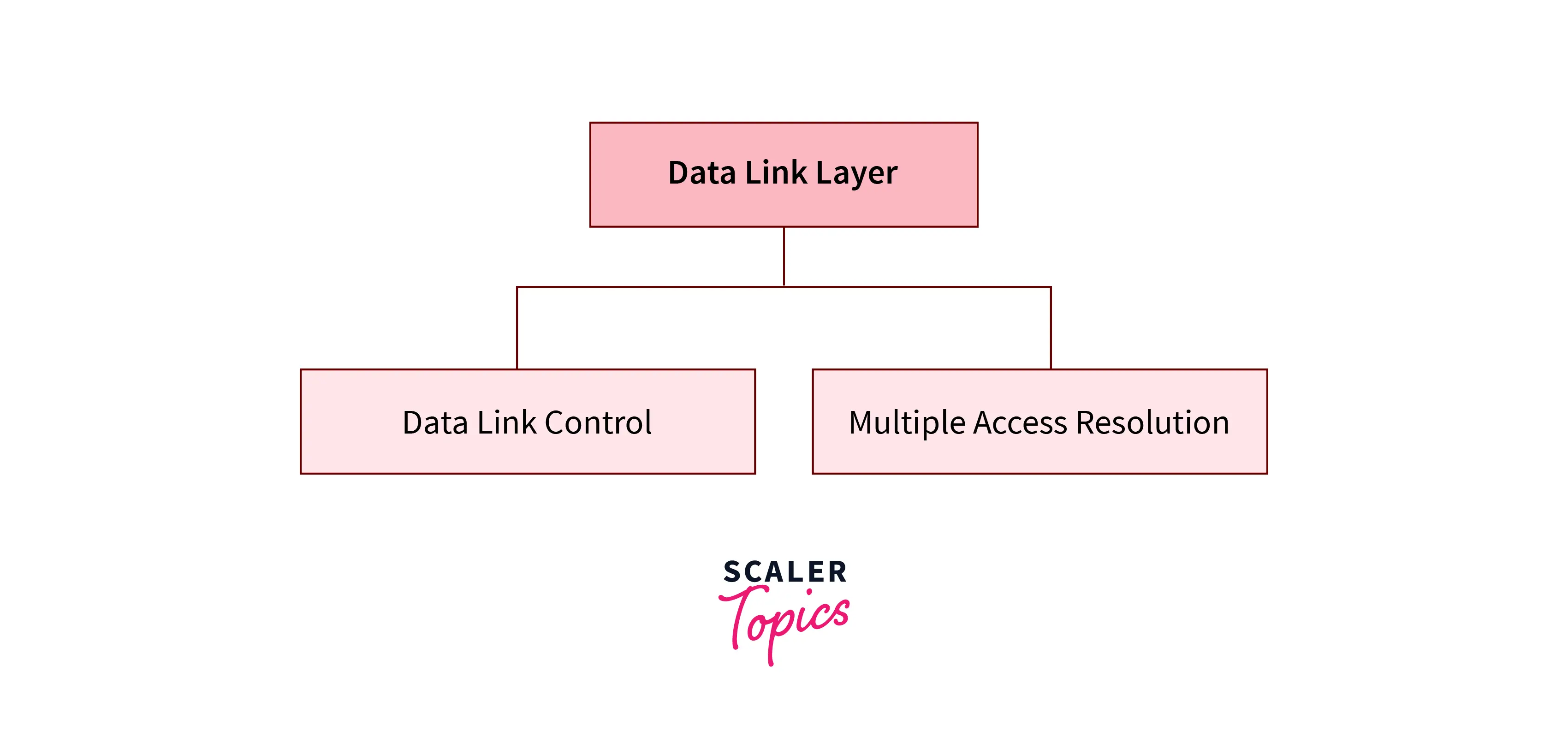
Introduction to Data Link Layer
The data link layer is manipulated in a computer network to transmit the information between 2 devices or nodes. It divides the layer into components like data link control and multiple access protocols. The upper layer is responsible for flow management and error management in the data link layer; thus, it is known as logical data link control. At the same time, the bottom layer is manipulated to handle and scale back the collision or multiple access on a channel. Thus it is termed media access control or multiple access resolutions.
:::
:::section{.main}
What are Multiple Access Protocols?
The fair of multiple access protocols are optimization of global time, depreciation of collisions, and run away from give-and-take.
Let’s assume, that there is a classroom filled with children. Once an educator asks an issue, all the children (small channels) within the classroom begin to respond to the question at an identical time (transferring the information concurrently). All the children respond at identical times thanks to that data/information overlapping or data being lost. So it is the responsibility of an educator (multiple access protocols) to lead the students and build them one answer.
:::
:::section{.main}
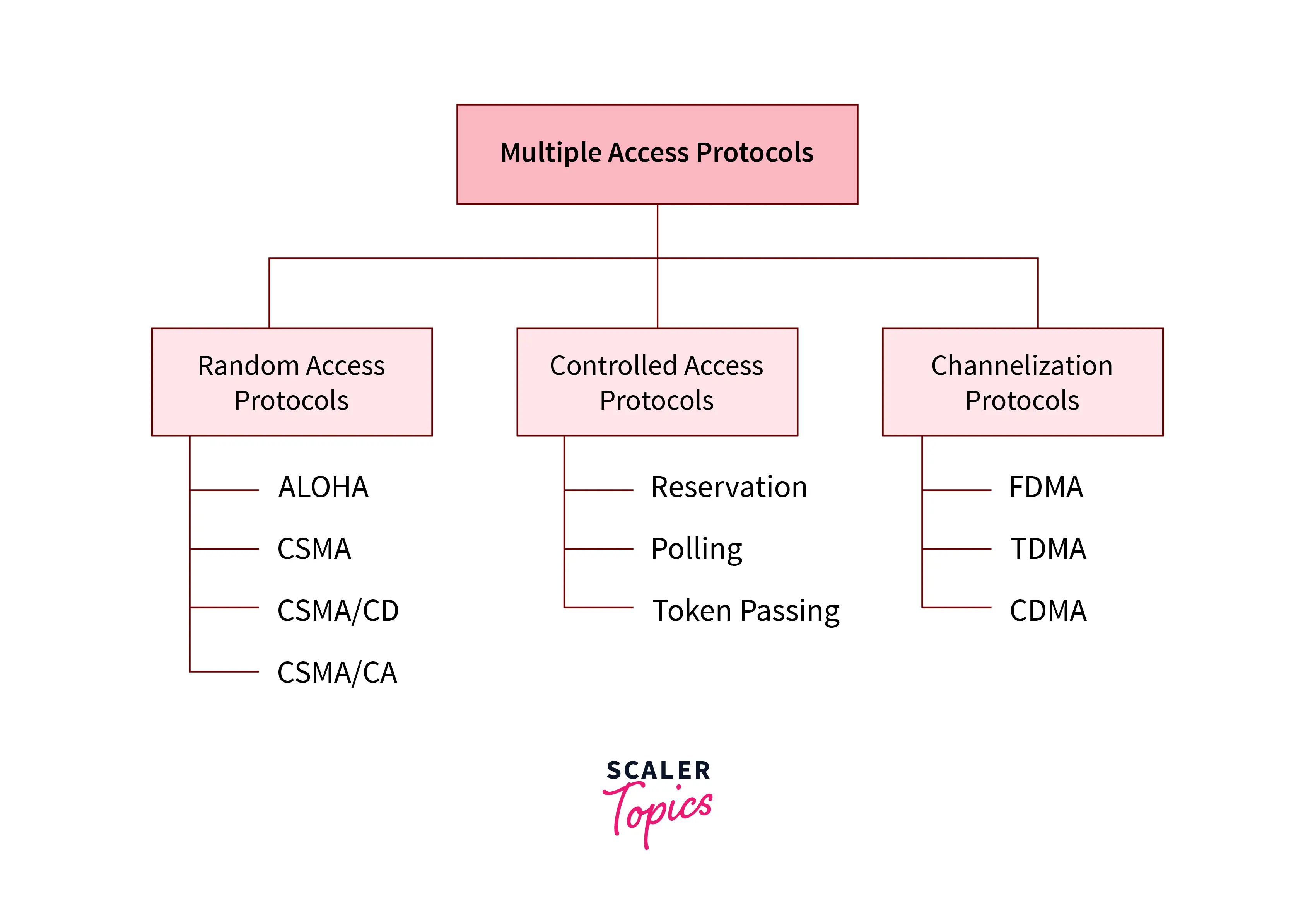
Types of Multiple Access Protocols
Following are the types of Multiple Access Protocols, which are separated into many different processes, are listed below.
Random Access Protocols
Let’s use the instance of a telephone conversation. Whenever you give a call to someone, a link between you and the wanted person is confirmed, additionally, anyone will make the call to anyone. Thus here we have all the users at a similar priority, wherever any station will send data/information providing on the medium’s state whether or not it is idle or busy, meaning that if your friend is chatting to somebody else through the telephone, then its standing is busy and you are not able to build a connection/link and since all the users are allotted equal precedence you can not disconnect your friend’s current call and establish yours.
The random access protocols carry with them the subsequent characteristics:
1 First of all, There is no time restriction for transmitting the data/information with your friends with no time restriction.
- There is a set of sequences of stations that are communicating the data or the information.
The Random access protocol is further subdivided into 4 different categories which are listed below:
- ALOHA
- CSMA
- CSMA/CD
- CSMA/CA
Let’s discuss each one of them.
ALOHA
The ALOHA protocol or conjointly referred to as the ALOHA methodology could be an easy communication medium during which each transmittal station or supply in an exceeding network can send the data or the information whenever a frame is accessible for transmission. If we tend to succeed and therefore the frame reaches its destination, then the successive frame is lined up for transmission. however keep in mind, that if the data or the information frame isn’t received by the receiver which may be due to the collision then the frame is shipped once more till it reaches the receiver’s end successfully.
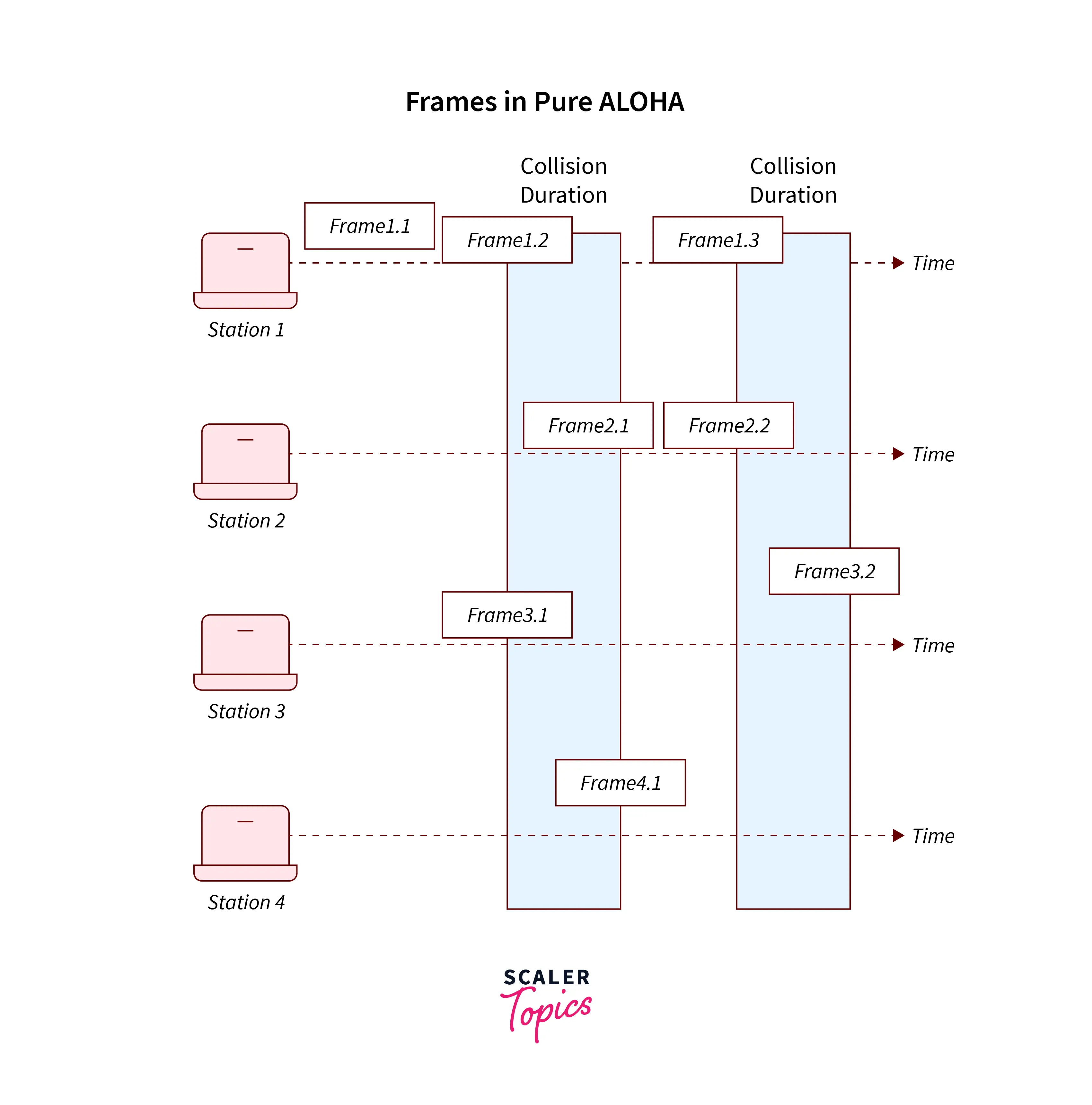
- Pure Aloha
The Data Transmission in Pure Aloha can transmit the data randomly which is any number of stations that can transmit the data at any given time.
The timestamp in Pure Aloha is continuous and basically, it is globally synchronized with any other number of stations.
The maximum efficiency of Pure Aloha is 18.4%.
The Collision status of Pure Aloha is that it does not reduce the total number to half.
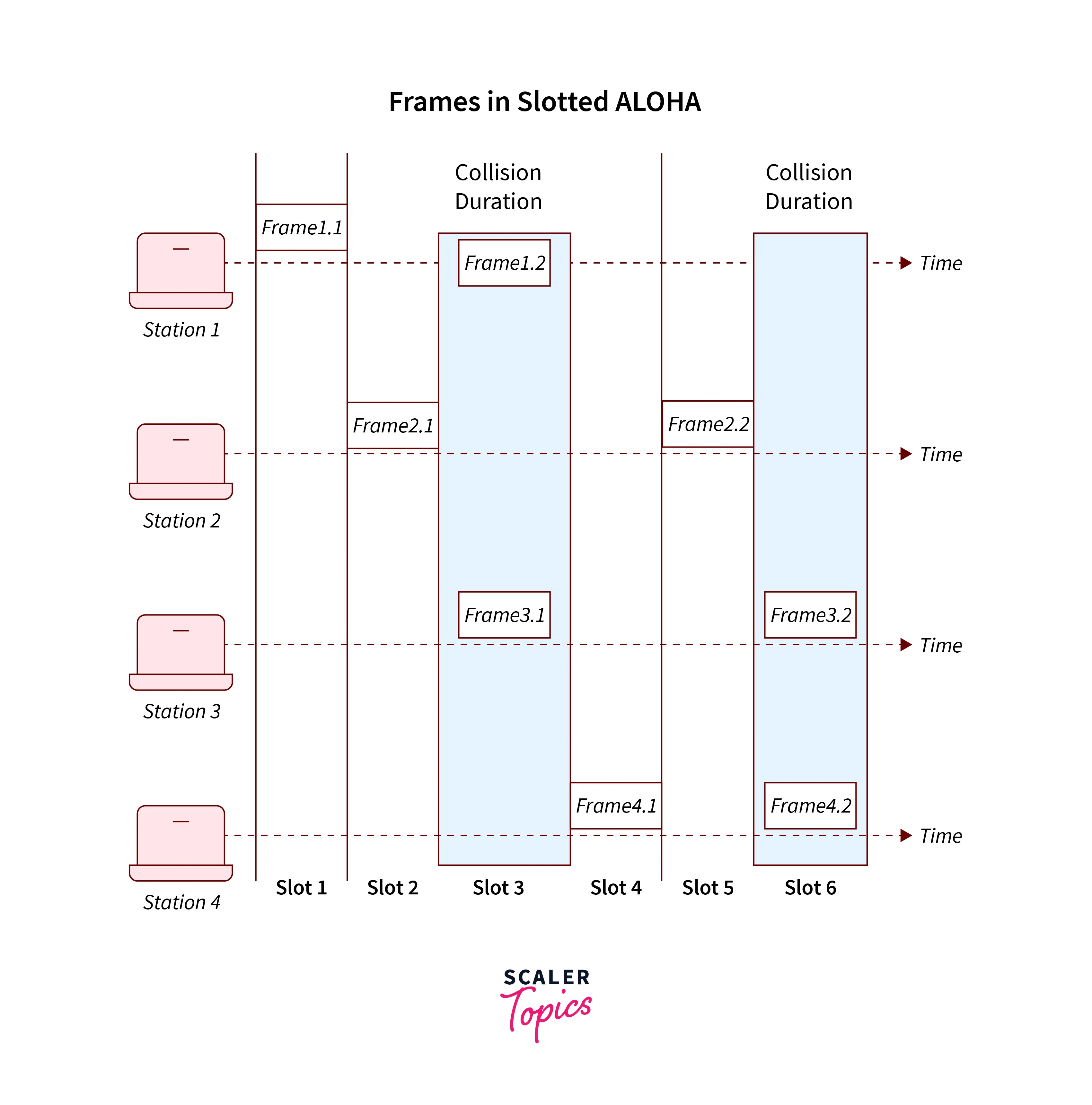
- Slotted Aloha
The Data Transmission in Slotted Aloha can transmit the data randomly at the start of any random time slot.
The timestamp in Slotted Aloha is discrete and basically, it is universally synchronized
The maximum efficiency of Slotted Aloha is 36.8%.
The Collision status of Slotted Aloha is that it basically reduces the total number to half and doubles the efficiency of pure Aloha.
CSM
CSMA basically stands for Carrier Sense Multiple Access. Currently, we have understood that once two or more stations begin redirecting data/information, then a collision happens, therefore this CSMA technique was developed to reduce the probabilities of collisions once two or more stations begin redirecting their signals over the data link layer. So the question is how they are doing it? The CSMA makes every station first check the medium whether it is busy or not before redirecting any data packet.
CSMA is having 4 different access protocol which is listed below:
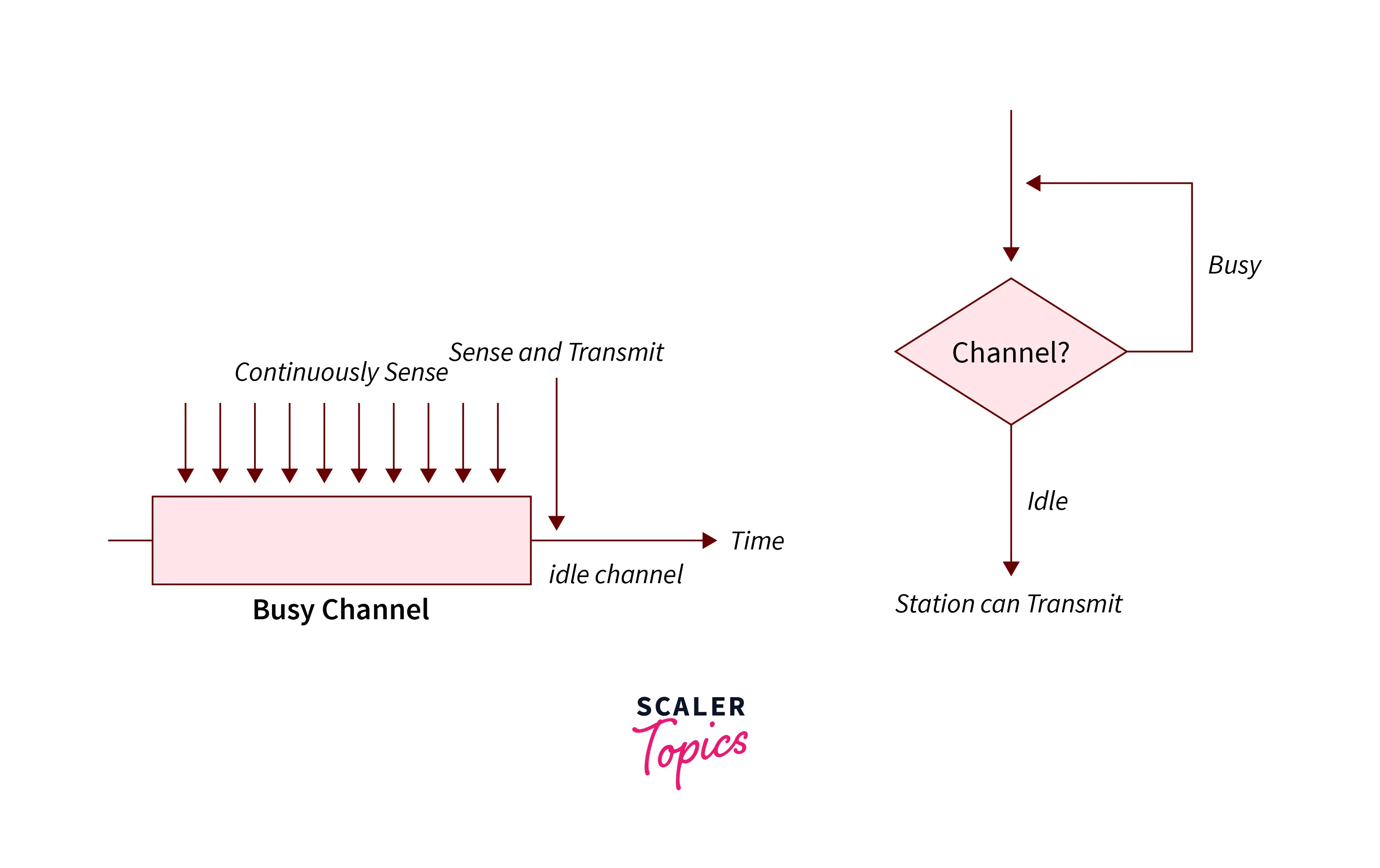
- 1-persistent :-
In this, initially, the node checks the channel, if the channel is passive then the node or station transmits information, it keeps on waiting and whenever the channel is passive, the stations transmit the data frame.
- Non-persistent:-
In this non-persistent, the station checks the channel equally as 1-persistent mode, however, the sole distinction is that once the channel is busy it checks it once more after a random quantity of your time, not like the 1-persistent mode wherever the stations keep it up checking incessantly. - P-persistent :-
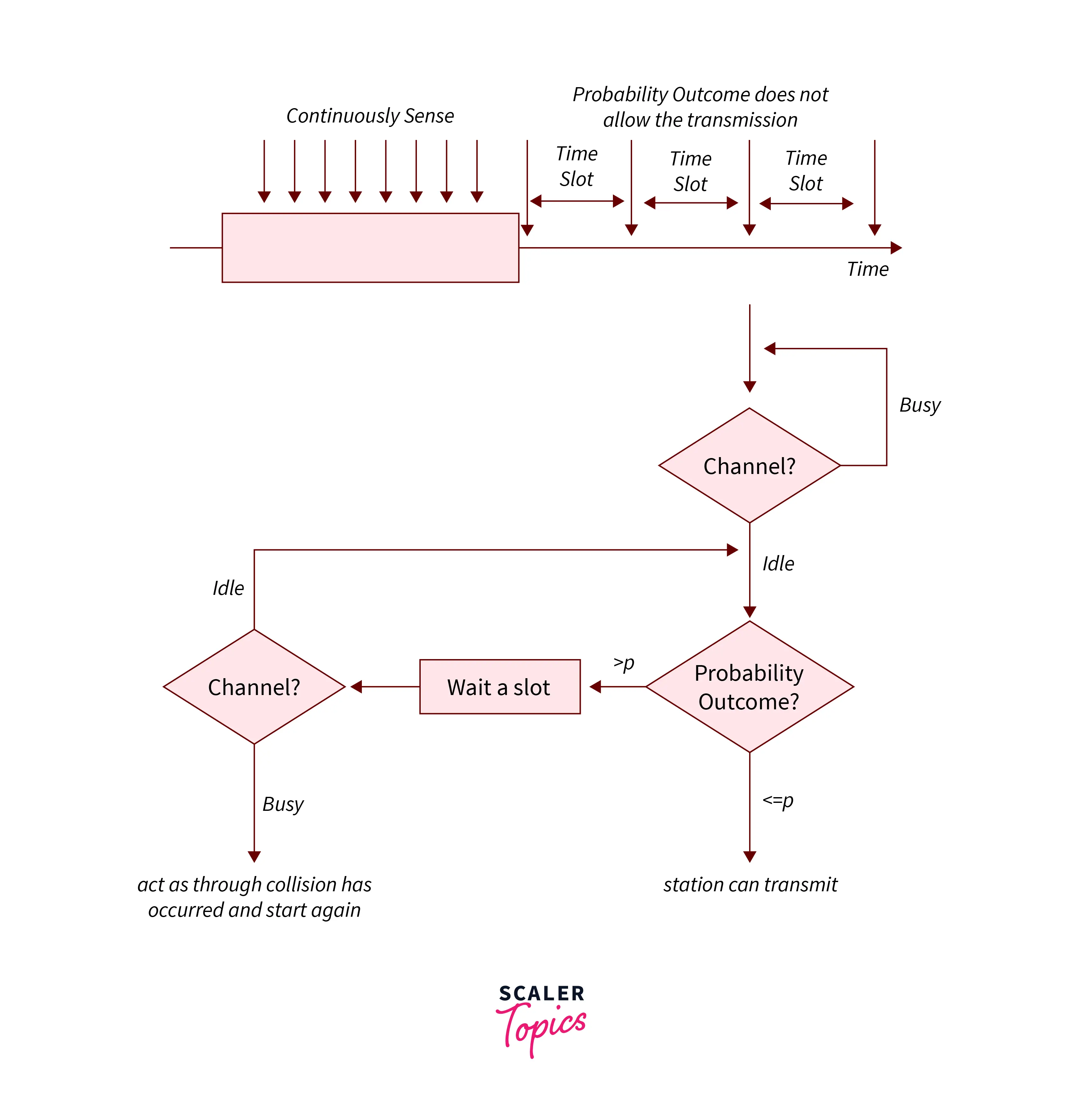
In P-persistent, the station checks the channel and if found passive then it transmits the information/data frame with the likelihood of P and if the data isn’t transmitted (1-P) then the station waits for a random quantity of your time and another time transmits the data with the likelihood P and this cycle goes on endlessly till the data-frame is sent successfully.
- O-persistent :-
In O-persistent, the transmission supports the prevalence of stations which is set beforehand and transmission happens in this given order. If the channel is passive, then the station waits for its address to send the data frame.
CSMA/CD
CSMA/CD basically means CSMA with Collision Detection.
In CSMA/CD, whenever the station transmits data-frame it then detects the channel or the medium to admit the state of the transmission that is profitably transmitted or failed. If the transmission succeeds, then it produces the successive frame otherwise it resends the formerly failed data frame. The purpose to recollect here is, that the frame coordinate universal time ought to be at minimum twice the most propagation time, which might be deduced once the gap between the 2 stations concerned in a collision is most.
CSMA/CA
CSMA/CAis generally known as CSMA with collision avoidance.
To sight the potential collisions, the sender receives the acknowledgment, and if there is just one acknowledgment gift of its own. then this suggests that the data frame has been sent profitably. But, if there are two or more additional acknowledgment signals then this means that the collision has occurred.
To avoid collision following methods are used in general
- Interframe Space
In the Interface space case, assume that your station waits for the channel to become passive and locate that the channel is passive, then it will not convey the data-frame Straight away to keep away from the collision due to propagation hold on. It rather waits for a few moments called interframe space or IFS, and when the time is up the station once again checks the medium for being passive. However, it ought to have remained in mind that the IFS length depends on the first concern of the station. - Contention Window
In this contention window, the time is split into slots. Say, if the sender is prepared for transmission of the data or the in, it then chooses a random variety of slots as waiting time that doubles every time if the channel is busy. But, if the channel is not passive at that moment, then it does not restart the whole method; however, it restarts the timer once when the channel is found passive again. - Acknowledgement
We have a tendency to mention on top of the sender station that will re-transmit the data if acknowledgment is not received prior to the timer runouts.
Controlled Access Protocols
In a controlled access protocol, the stations obtain info from each other to seek out what the station has the authority to send. It permits just one node to send at a time, to control the collision of messages on a shared medium. The 3 controlled-access methods are given below:
- Reservation
In the reservation methodology, a station has to create a reservation prior to data.
The schedule has 2 kinds of periods:
- Reservation interval of agreed time length
- Data transmission duration of variable frames.
If there are M stations, the reservation interval is split into M slots, and every station has only one slot.
Assume that station one encompasses a frame to send, it transmits one bit throughout slot one. No alternative station is permitted to transmit throughout this slot.
Commonly, i the station could announce that it’s a frame to send by inserting one bit into i the slot. Finally, all N slots have been checked, every station is aware of which stations want to transmit.
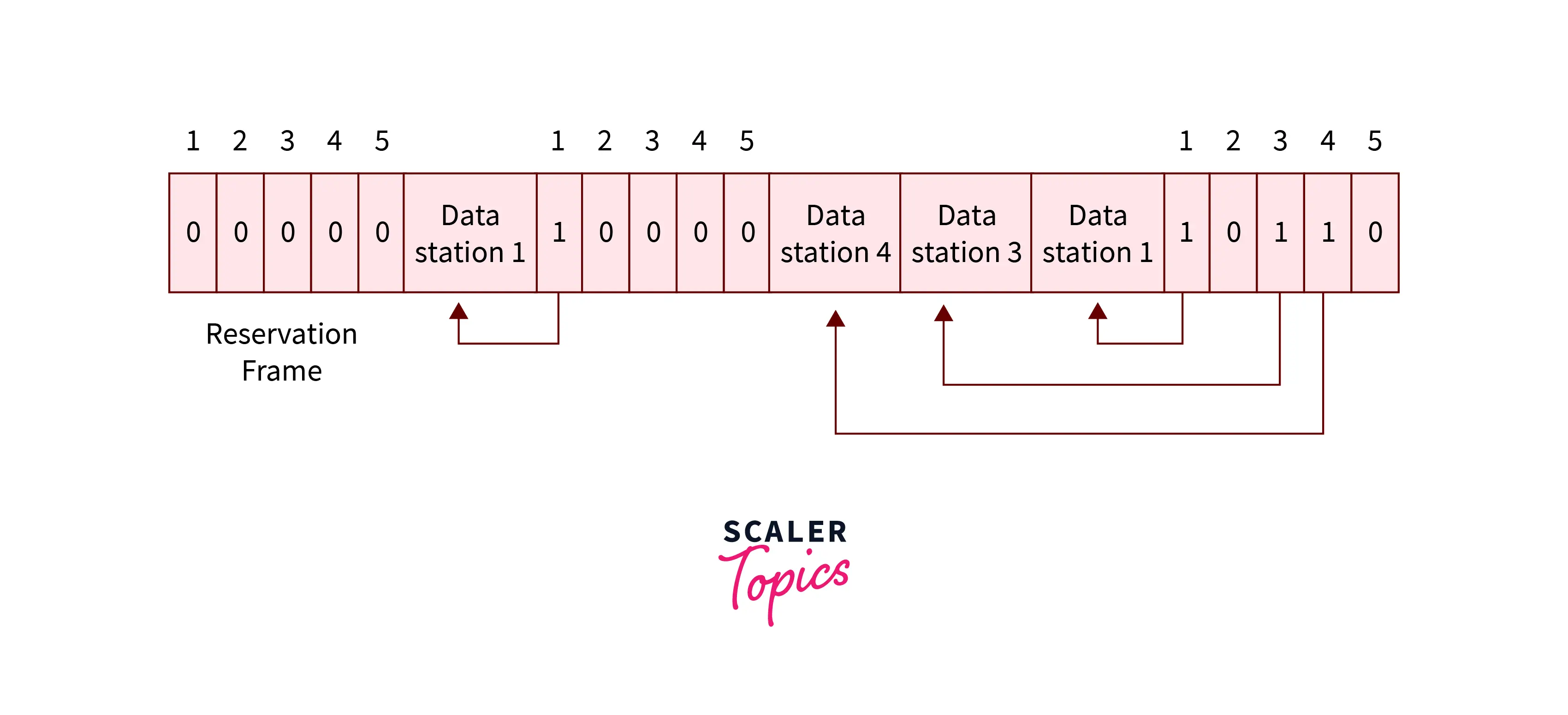
In this figure a condition with 5 stations and 5 slot reservations available. However in this given first interval only 1,3 and 4 are able to make the reservation and in another second interval, only 1 could make it.
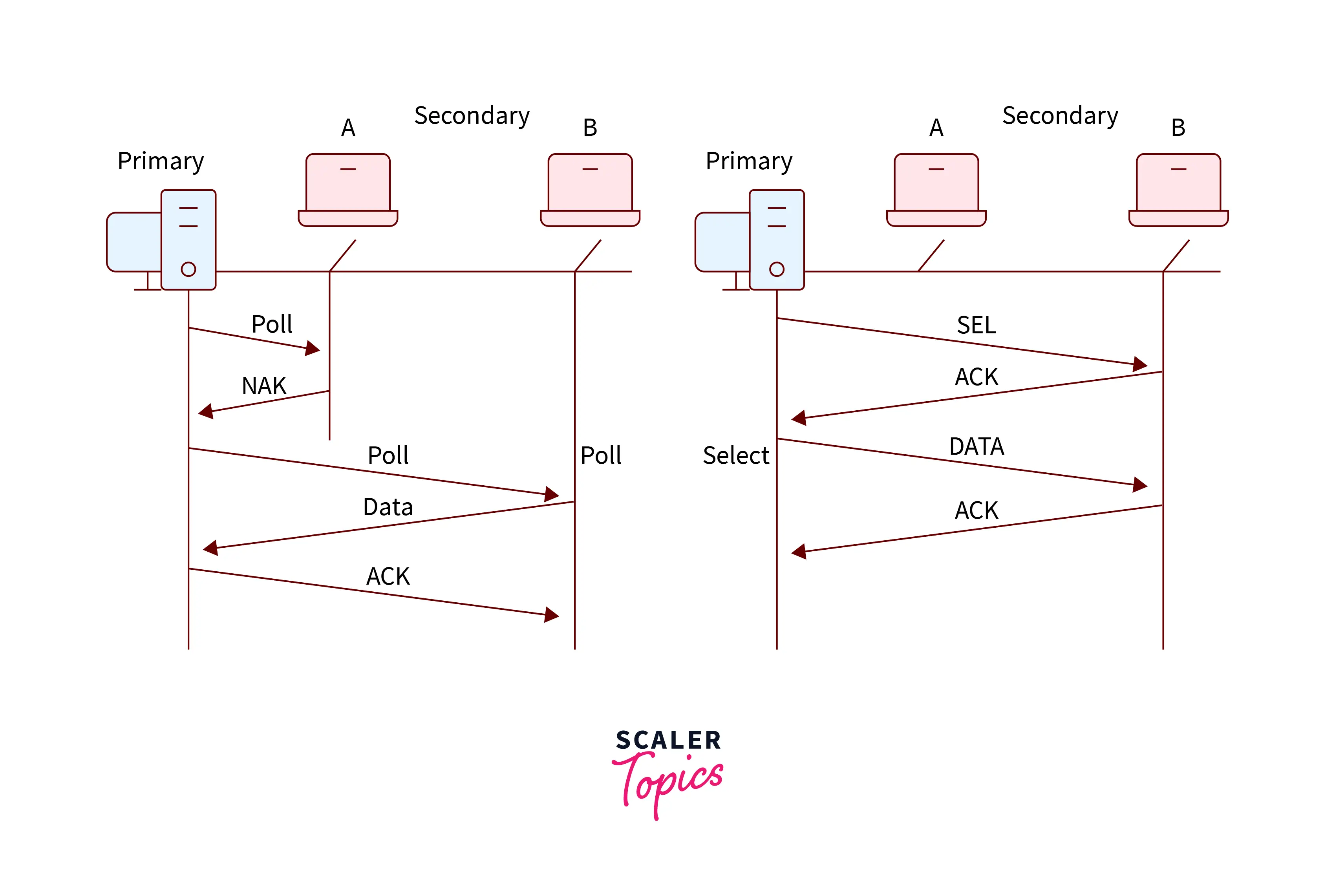
- Polling
The polling method is analogous to the roll call performed in school. rather like the teacher, a controller sends a message to every node successively.
In this, one acts as a primary station(controller) and therefore the others are secondary stations. All data exchanges should be created through the controller.
The message sent by the controller holds the address of the node being hand-picked for granting access.
Although all nodes receive the message however the addressed one responds to that and sends data if any. If no data is available, normally a “poll rejection”(NAK) message is dispatched back.
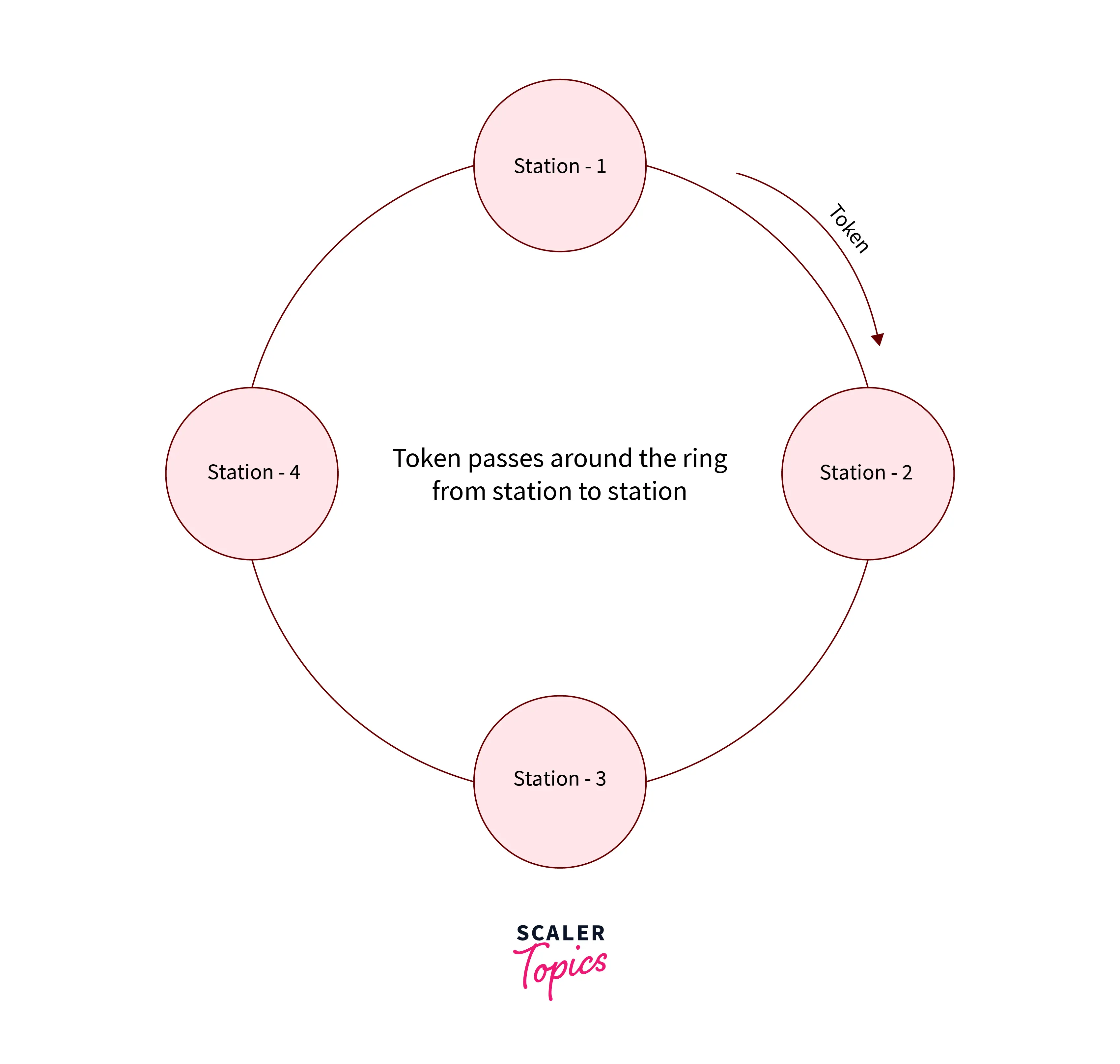
- Token Passing
In the token-passing process, the stations are linked logically to every alternative in the form of a ring, and access to stations is ruled by tokens.
A token could be a special bit pattern or a little message, that flows from 1 station to the consecutive in some predefined order.
In a Token ring, the token is passed from 1 station to a different adjacent station within the ring whereas, in the case of a Token bus, every station uses the bus to send the token to the consecutive station in some predefined order.
Basically, in both the given cases, the token represents permission to send. If a station incorporates a frame queued for transmission once it receives the token, it will redirect that frame before it passes the token to the consecutive station. If it has no queued frame, it passes the token merely.
### Channelization Protocols
In the channelization protocol, the accessible bandwidth of the link is split in time, frequency, and code to numerous stations to access the channel at the same time.
- Frequency Division Multiple Access (FDMA)
The convenient bandwidth is split into equal bands for every station that will be allotted its band. Guard bands are attached in such an order that no 2 bands overlap to avoid debate and noise.
- Time Division Multiple Access (TDMA)
In this Time Division of Multiple Access, the bandwidth is divided between multiple stations. To circumvent collision time is split into slots and stations are allocated these slots to transmit data. but there is an overhead of synchronization as every station must grasp its time slot. This is often resolved by adding synchronization bits to every slot. Another issue with TDMA is propagation delay which is determined by the supplementary guard bands.
- Code Division Multiple Access (CDMA)
One channel carries every transmission at the same time. There is neither a splitting of bandwidth nor a splitting of time. Let’s Assume, that there are plenty of people in a hall all speaking at an identical time, then in addition to that excellent reception of data is feasible if only 2 people speak an identical language. Similarly, data from completely different stations will be transmitted at the same time in numerous code languages.
:::
:::section{.summary}
Conclusion
- Multiple access protocols are used to coordinate access to the link.
- In Multiple access protocols, Nodes can regulate their transmission onto the shared broadcast channel by using Multiple Access Protocols.
- Multiple Access Protocol is used in both wired and wireless local area networks (LAN) and satellite networks.
- In Multiple Access Protocols, All nodes are capable of transmitting frames, more than 2 nodes can transmit frames at the same time.
- In the Multiple Access Protocol a sense, the signals of the colliding frames become inextricably tangled together.
- Thus, all the frames in the Multiple Access Protocol involved in the collision are lost, and the broadcast channel is wasted during the collision interval.