What is AWS Network Access Control List (NACL)?
Overview
NACL AWS or Network Access Control Lists is a set of rules that decides whether certain traffic is allowed or denied when it enters or leaves a specific network area, known as a subnet. You can either use the pre-defined network ACL that comes with your Virtual Private Cloud (VPC), or you can create your custom network ACL with rules that work similarly to the rules you set for your security groups. This custom ACL adds an extra layer of security to your VPC, allowing you to fine-tune which traffic is permitted and which is blocked. Using network ACLs doesn't cost you any extra money. It's a built-in feature to help safeguard your network without incurring additional charges.
Components of NACL
NACL AWS consists of several key components:
- Inbound Rules:
Inbound rules are a set of rules that define what inbound (incoming) traffic is allowed or denied to reach resources within a subnet. Each rule specifies a rule number, an action (allow or deny), an IP address range (or source IP), and a port range (or protocol) for traffic coming into the subnet. - Outbound Rules:
Outbound rules, similar to inbound rules, control outbound (outgoing) traffic from the subnet. They also include a rule number, an action, source IP range, and port/protocol settings for traffic leaving the subnet. - Rule Numbers:
Each rule within an NACL AWS is identified by a unique rule number. Rule numbers are integers and dictate the order in which the rules are evaluated. Lower rule numbers are evaluated before higher ones. - Action:
The action specified in a rule can be either "allow" or "deny". "Allow" permits the specified traffic, while "deny" blocks it. - IP Address Ranges:
You define IP address ranges (CIDR notation) to specify the source or destination of traffic for each rule. This can be a single IP address, an IP range, or a wildcard such as 0.0.0.0/0 to represent all IP addresses. - Port Range/Protocol:
Rules may include port range and protocol information. Port ranges allow you to filter traffic based on specific ports (e.g., port 80 for HTTP). Protocol options include TCP, UDP, and ICMP. - Stateless:
NACL AWS is stateless, meaning you must define both inbound and outbound rules separately. If you allow inbound traffic for a specific port, you must also allow the corresponding outbound traffic for established connections. - Logging:
Optionally, you can enable logging for NACLs to capture information about the traffic that matches the rules. Logging can be useful for monitoring and troubleshooting network activity. - Default NACL:
The default network ACL is configured to allow all traffic to flow in and out of the subnets with which it is associated. Each network ACL also includes a rule whose rule number is an asterisk (*). This rule ensures that if a packet doesn't match any of the other numbered rules, it's denied. You can't modify or remove this rule.
These components collectively allow you to define and enforce network security policies within your AWS Virtual Private Cloud by controlling the flow of traffic in and out of your subnets based on your specified rules and criteria.
When to Use NACLs?
NACL AWS is useful for specific scenarios where you need granular control over network traffic at the subnet level. Here are some situations when you should consider using NACLs:
- Segmentation and Isolation:
When you want to segment your VPC into multiple subnets and enforce network isolation between them. NACLs can be used to restrict traffic between subnets based on specific rules. - Compliance and Security:
When you have strict compliance requirements or need to implement fine-grained security controls, NACLs can provide an additional layer of security alongside security groups. - Traffic Filtering:
When you need to filter traffic at a low level, such as allowing or denying traffic based on IP addresses, ports, or protocols. NACLs can be used to filter traffic before it reaches instances in a subnet. - Public and Private Subnets:
In architectures with both public and private subnets, NACL AWS can be employed to control the flow of traffic between the internet and internal resources, providing an extra security layer beyond security groups. - Logging and Monitoring:
If you require detailed logging of network traffic for monitoring, auditing, or compliance purposes, NACL AWS can be configured to log traffic that matches specific rules. - DDoS Mitigation:
NACLs can be part of your defense strategy against Distributed Denial of Service (DDoS) attacks. By defining rules to block traffic from suspicious IP ranges, you can reduce the impact of malicious traffic. - Legacy Applications:
In situations where you have legacy applications that require specific network configurations, NACLs can be used to accommodate those requirements. - Hybrid Cloud Environments:
When you have a hybrid cloud setup with on-premises resources connecting to AWS VPCs, NACL AWS can help control traffic between these environments. - Traffic Prioritization:
If you need to prioritize certain types of traffic over others, you can use NACLs to control the flow of traffic according to your prioritization rules. - Testing and Development:
NACL AWS can be valuable in testing and development environments where you want to isolate resources and control the traffic flow for debugging or testing purposes.
While NACLs offer fine-grained control, it's essential to use them judiciously. In many cases, you may rely more heavily on AWS security groups for managing network access because they are stateful and easier to configure for common use cases. NACL AWS is typically used in conjunction with security groups to provide comprehensive network security within your AWS VPC.
Creating a NACL
Here is a sequence of steps to create and configure an NACL AWS, using the AWS Management Console, AWS CLI as well and AWS CloudFormation:
AWS Management Console
-
Sign in to AWS Console:
- Log in to your AWS account using your credentials.
-
Access VPC Dashboard:
- From the AWS Console, select "VPC" to access the Virtual Private Cloud dashboard.
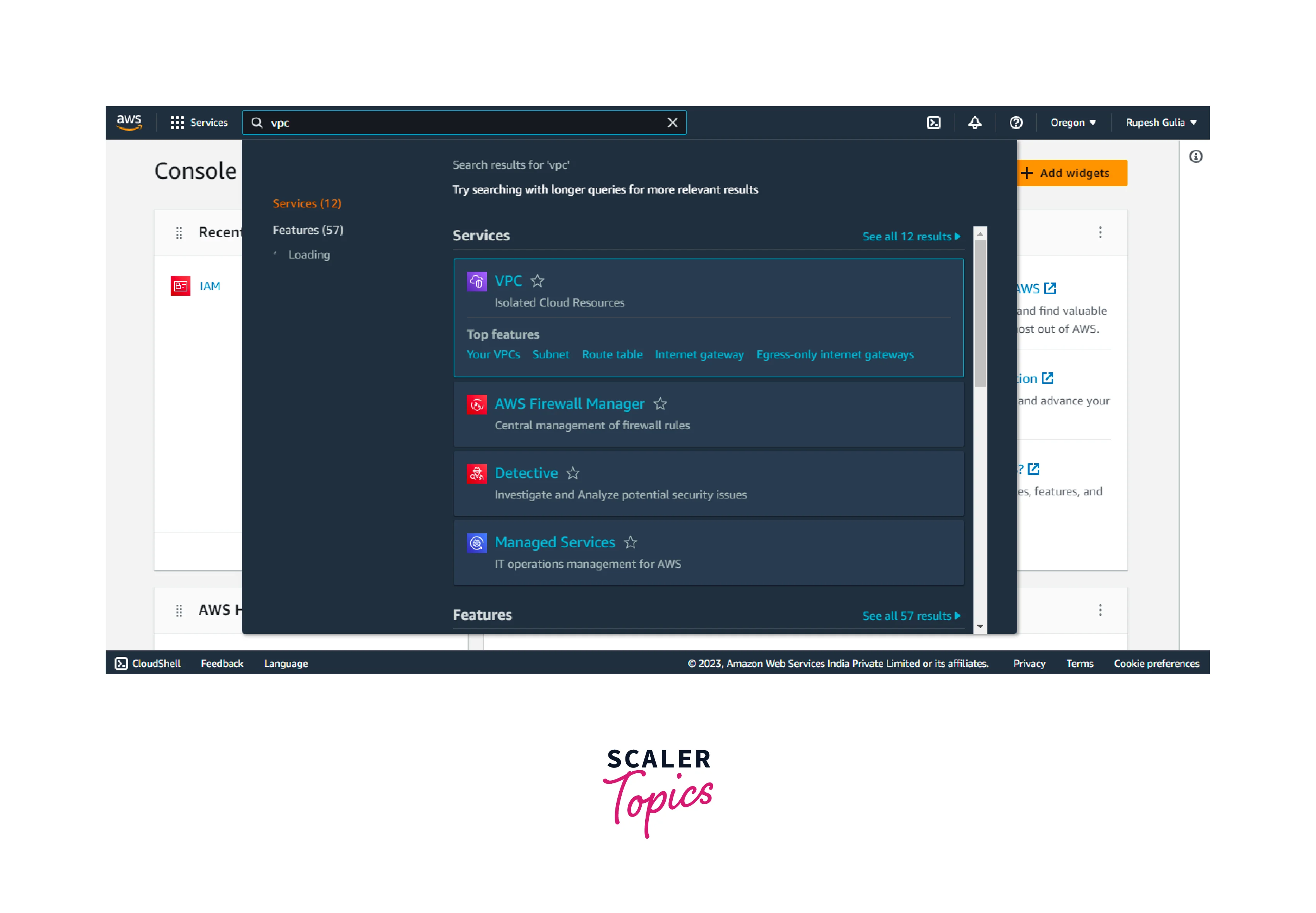
- From the AWS Console, select "VPC" to access the Virtual Private Cloud dashboard.
-
Navigate to Network ACLs:
- In the VPC dashboard, locate and click on "Network ACLs" in the left navigation pane.
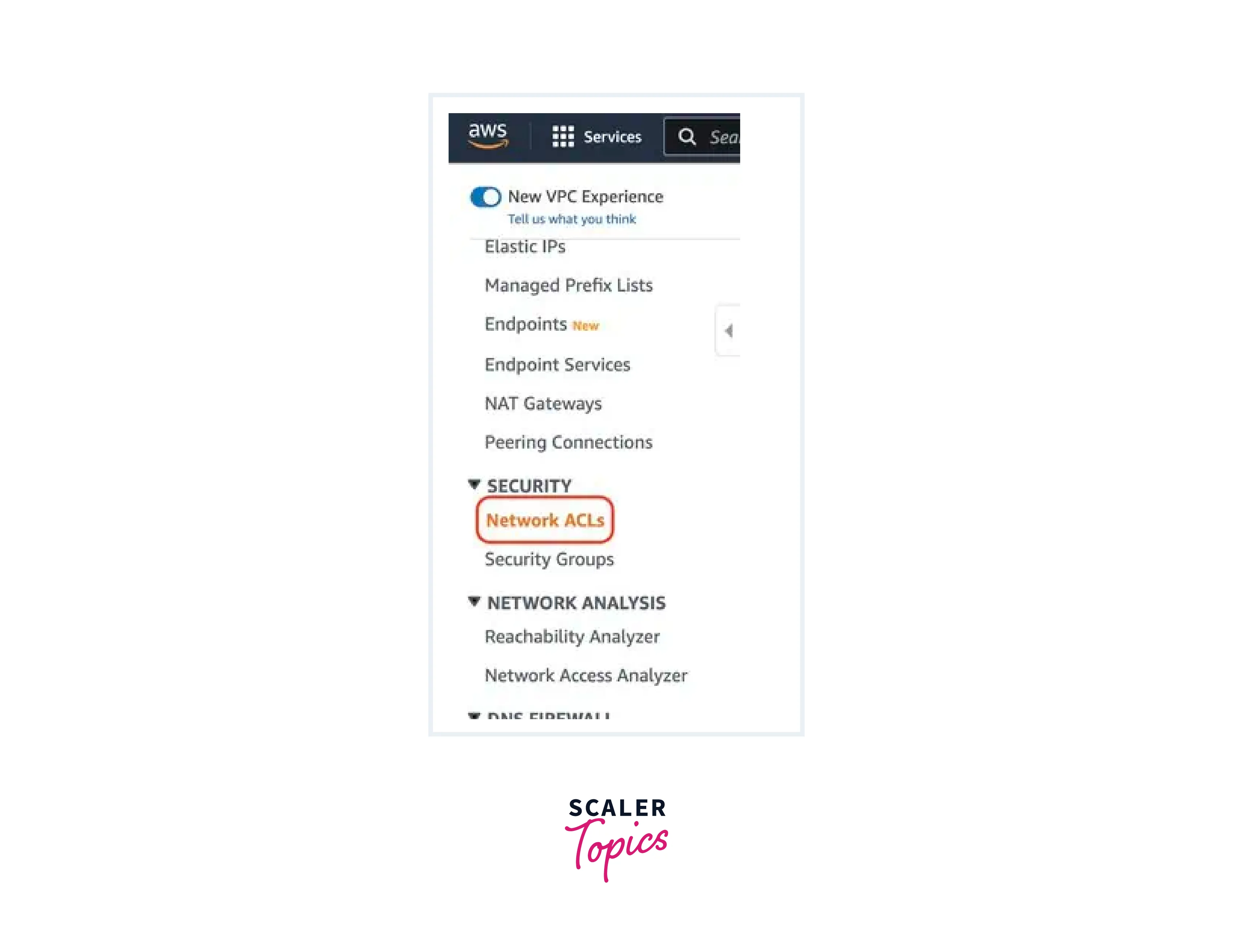
- In the VPC dashboard, locate and click on "Network ACLs" in the left navigation pane.
-
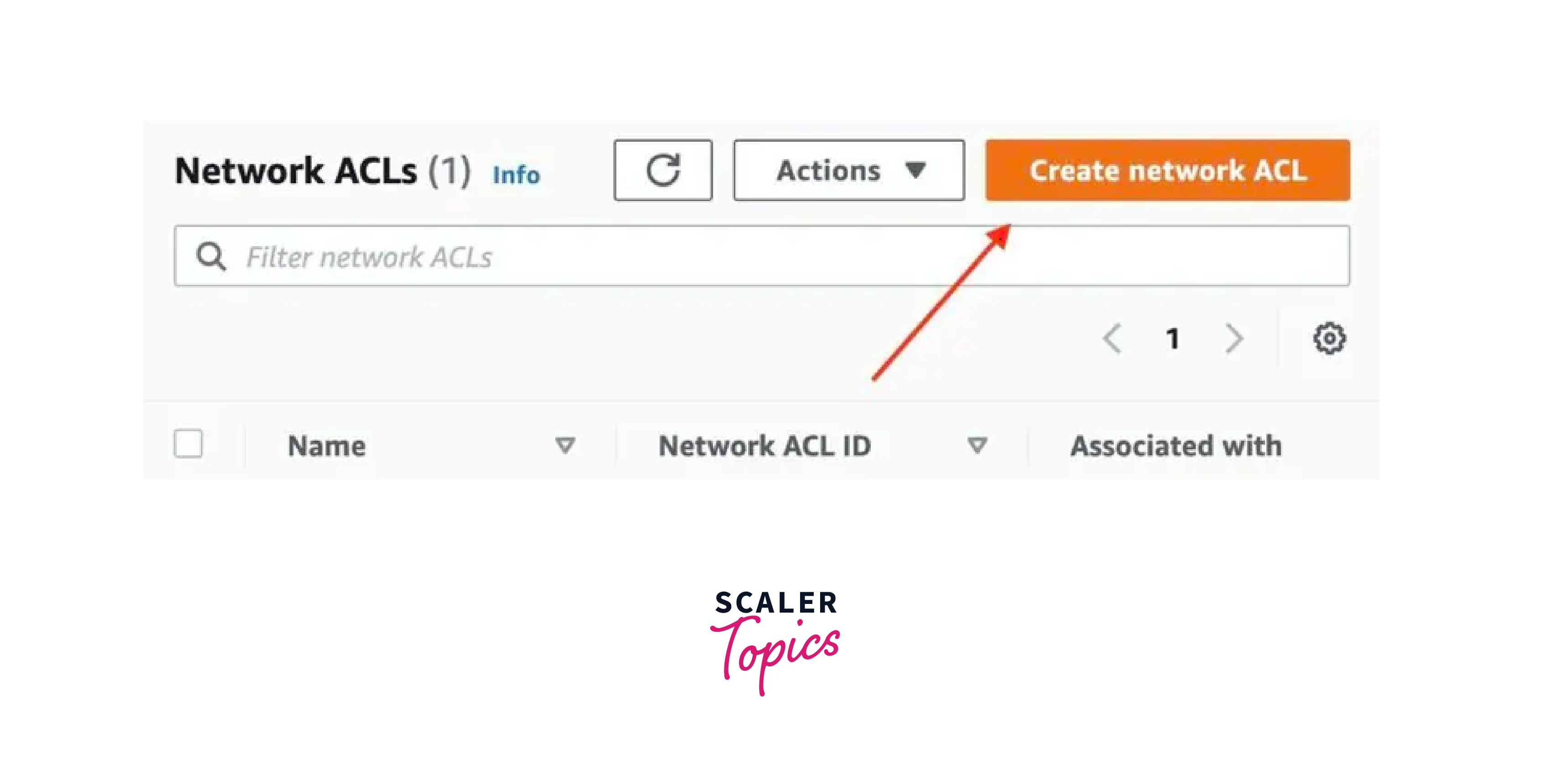
Create a New NACL AWS:
- Click the "Create network ACL" button.
- Provide a name and select a VPC for your NACL AWS.
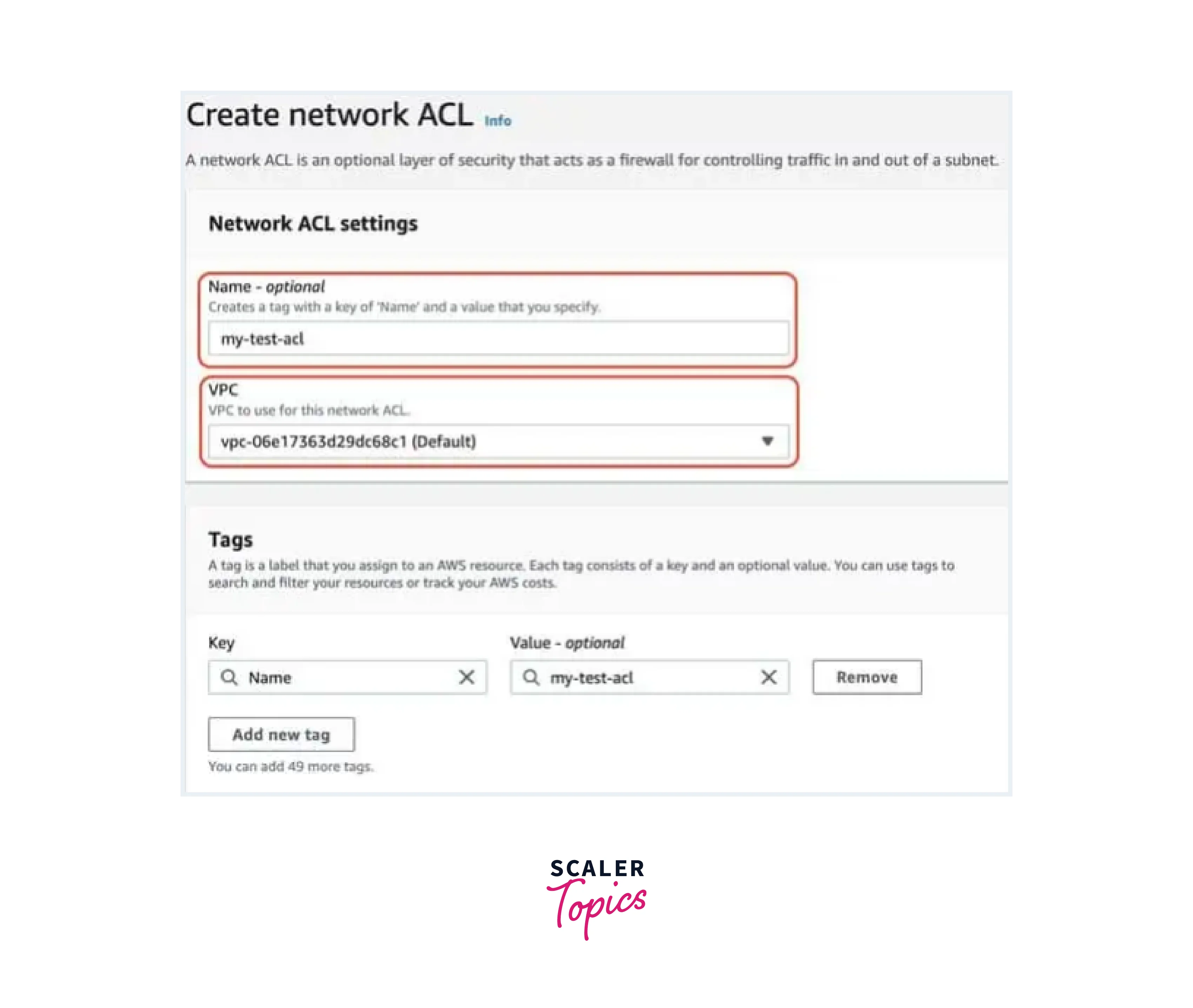
- Click "Create network ACL".
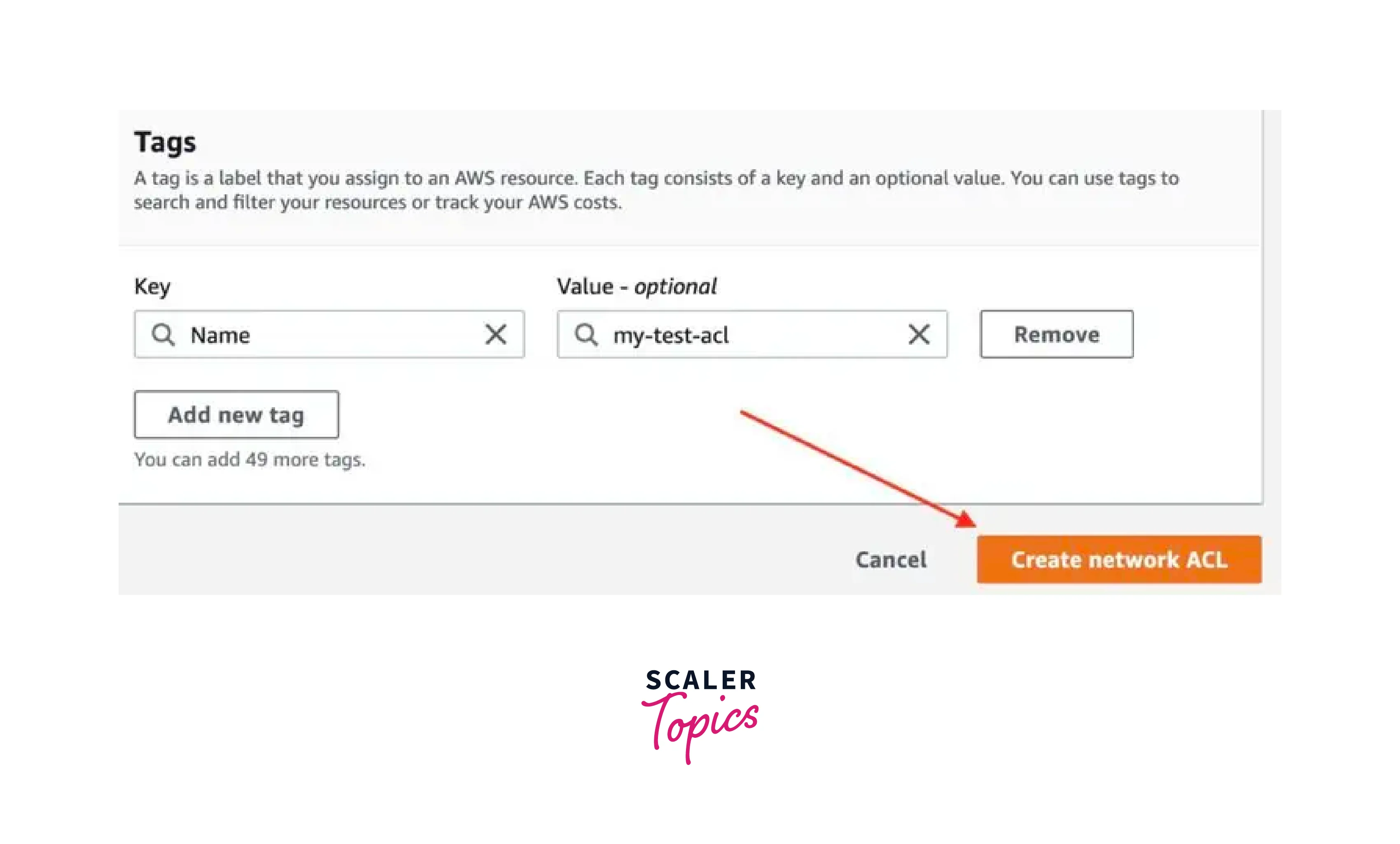
- Click the "Create network ACL" button.
-
Configure Inbound Rules:
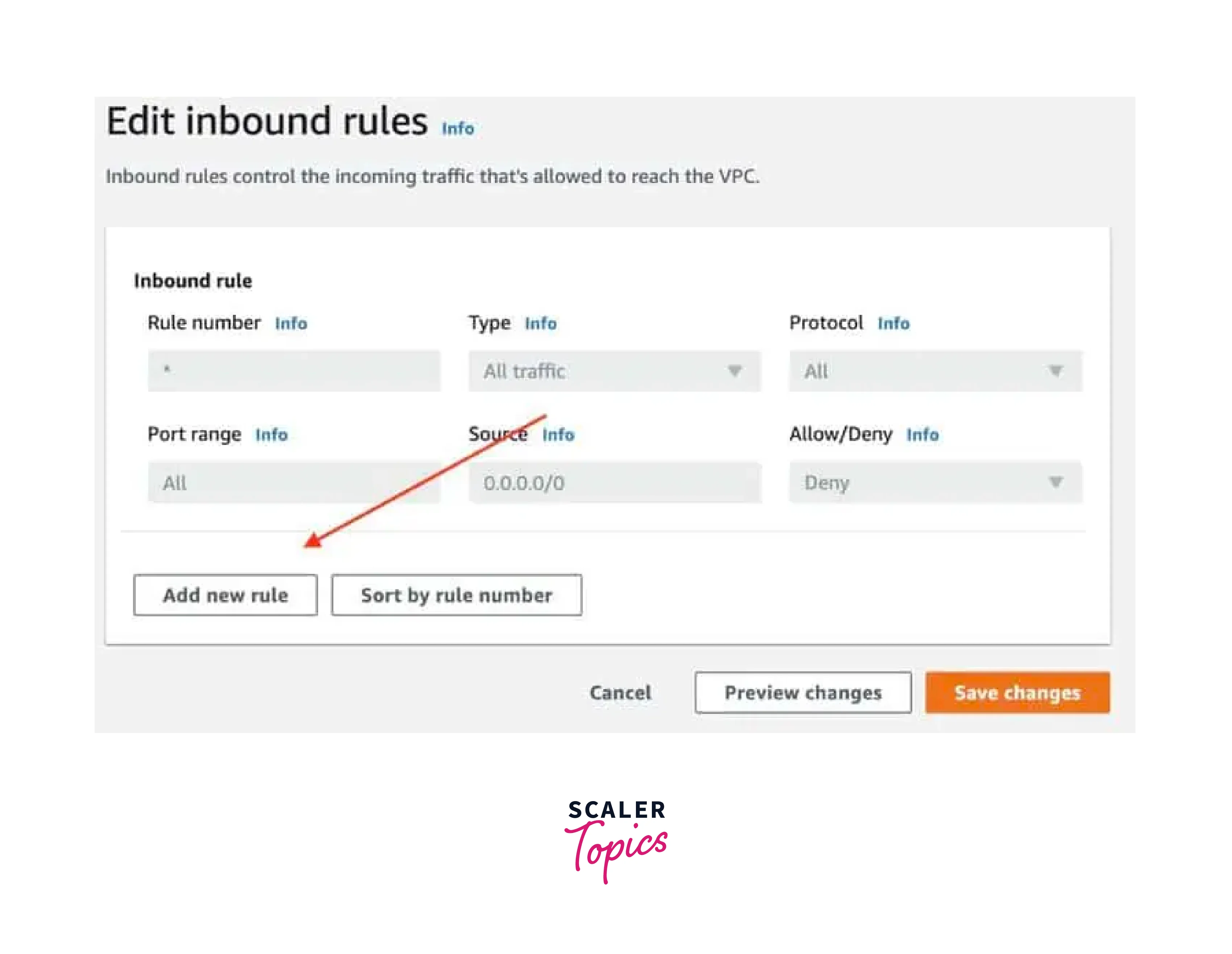
- Select the newly created NACL, then click "Actions" and choose "View details".
- Click "Edit inbound rules".
- Add new inbound rules by specifying rule numbers, actions (allow or deny), source IP ranges, and port/protocol settings.
- Click "Save changes".
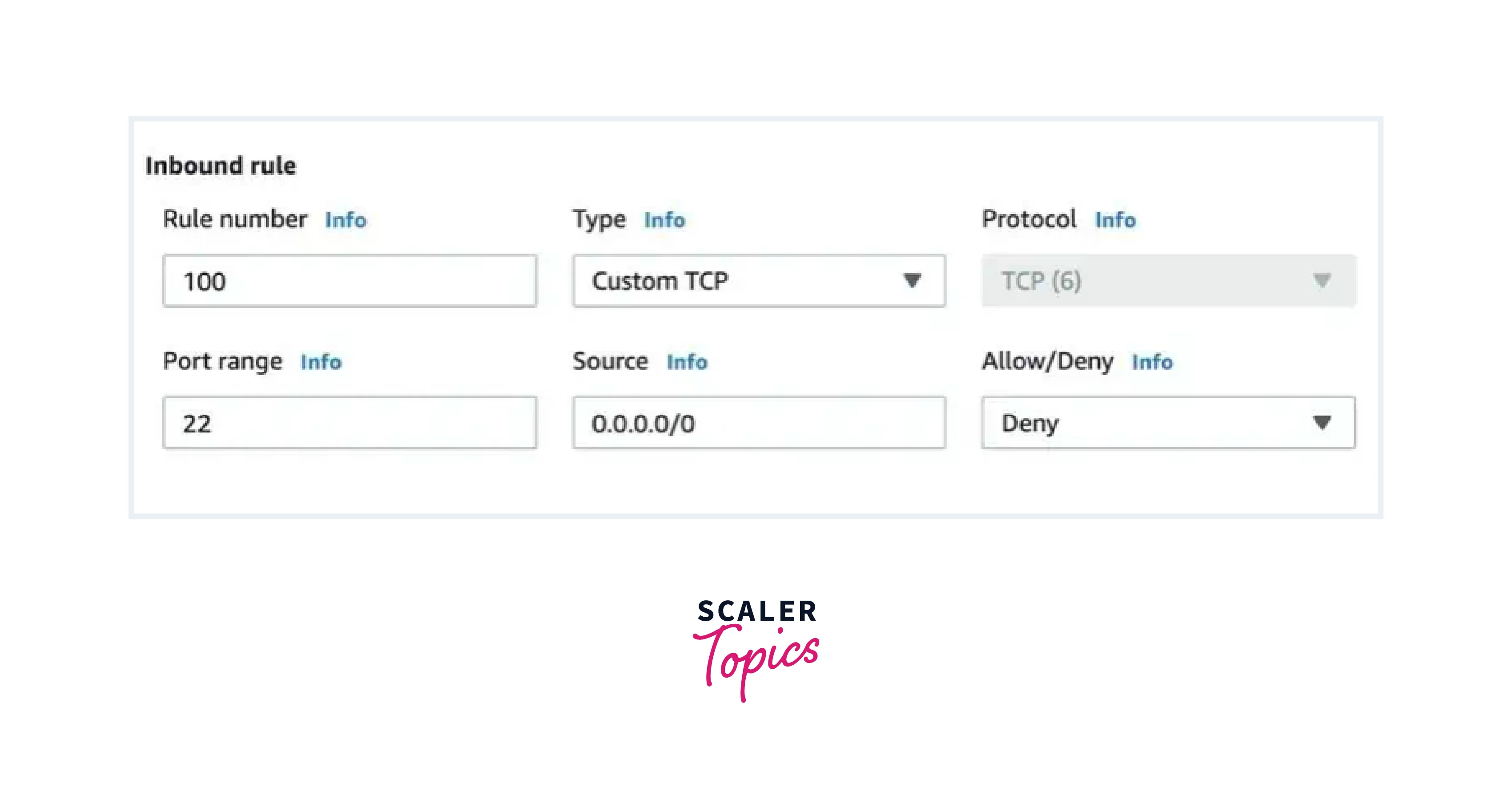
-
Configure Outbound Rules:
- Similar to inbound rules, click "Edit outbound rules" to configure outbound traffic rules.
- Add new outbound rules following the same format.
- Click "Save changes".
-
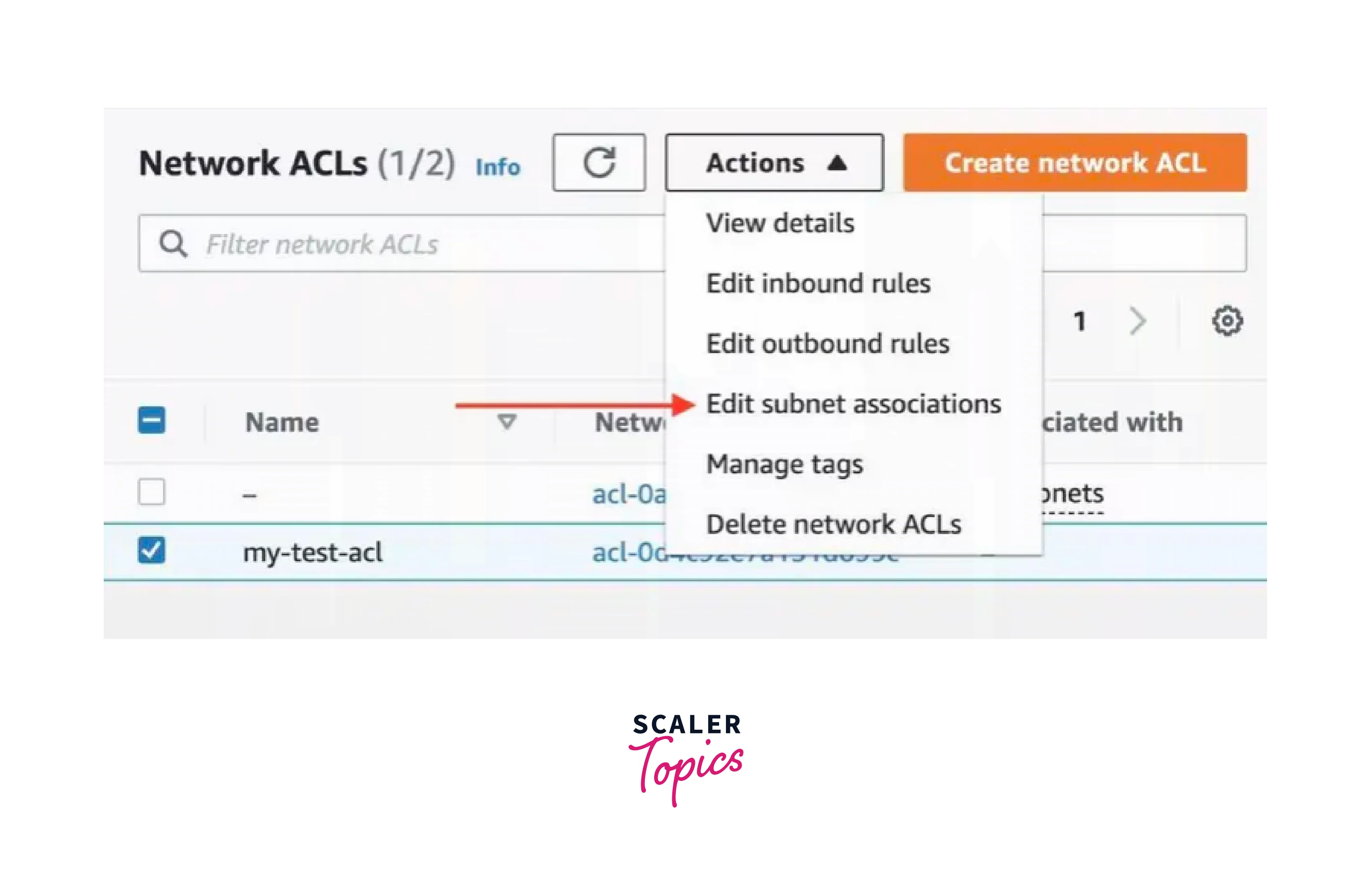
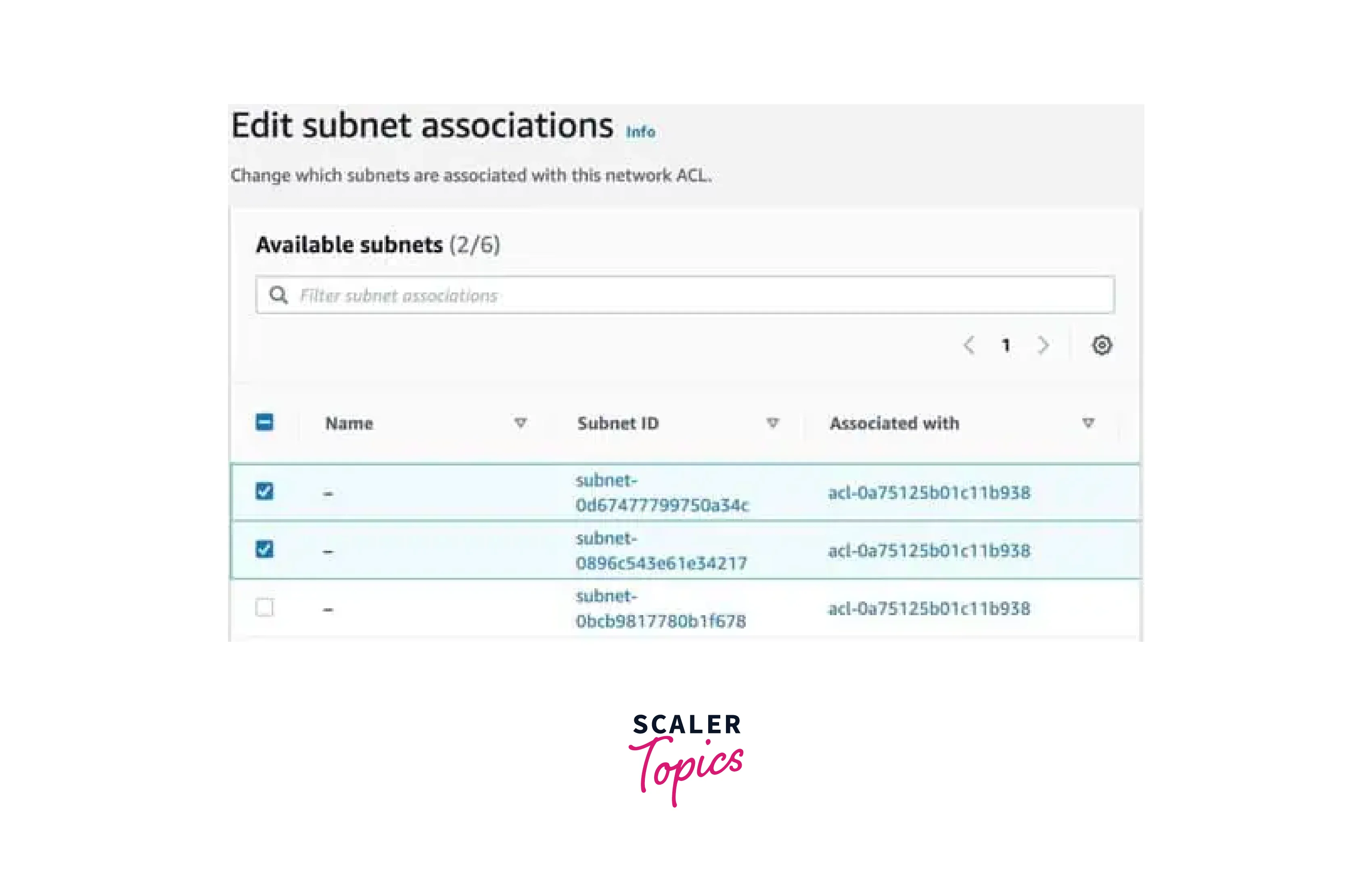
Associate NACL with Subnets:
- Select the NACL, click "Actions", and choose "Edit subnet associations".
- Choose the subnets you want to associate with the NACL AWS.
- Click "Save Changes".
AWS CLI
-
Create NACL:
- Use the AWS CLI to create a new NACL AWS, specifying the VPC:
- Use the AWS CLI to create a new NACL AWS, specifying the VPC:
-
Create Ingress Rule:
- Use the AWS CLI to add an ingress rule to the NACL:
- Use the AWS CLI to add an ingress rule to the NACL:
-
Create Egress Rule:
- Similarly, create an egress rule to block outbound traffic:
- Similarly, create an egress rule to block outbound traffic:
AWS CloudFormation (YAML Example)
-
Define NACL in YAML:
- Create a CloudFormation template in YAML format, specifying the NACL AWS properties:
- Create a CloudFormation template in YAML format, specifying the NACL AWS properties:
-
Deploy via AWS Console:
- Save the YAML template as a file (e.g., testNACL.yaml).
- Deploy the template using the AWS CloudFormation service through the AWS Console.
These steps provide a clear sequence for creating and configuring a Network Access Control List in AWS using different methods. Make sure to adapt the steps to your specific use case and requirements.
Best Practices for Managing NACLs
NACL AWS is used to control inbound and outbound traffic at the subnet level. Here are some best practices for managing NACLs effectively:
- Understand NACL Basics:
Before creating NACLs, understand their purpose and how they differ from Security Groups. NACLs operate at the subnet level and are stateless, meaning you need to define both inbound and outbound rules separately. - Follow the Principle of Least Privilege:
Only allow necessary traffic and deny all other traffic. Start with a default "Deny All" rule for both inbound and outbound traffic and add rules as needed. Avoid overly permissive rules. - Use Descriptive Rule Names:
Give your NACL rules meaningful and descriptive names. This makes it easier to understand the purpose of each rule when reviewing or troubleshooting. - Plan and Document:
Before creating NACL AWS rules, plan out your network security requirements and document them. This helps ensure that you create rules that align with your security policies. - Prioritize Security Over Convenience:
It's better to have slightly more complex NACL rules that provide better security than to have overly permissive rules for the sake of convenience. - Logging and Monitoring:
Enable VPC Flow Logs to monitor and analyze network traffic. This helps in identifying unusual or unauthorized traffic patterns. Use Amazon CloudWatch or other monitoring tools to set up alerts for suspicious activities. - Regularly Review and Update:
Network requirements can change over time. Periodically review your NACL AWS rules to ensure they still align with your security requirements. Remove any rules that are no longer necessary. - Use Separate NACLs for Different Subnets:
Consider using different NACLs for different subnets based on the level of security required. Critical or sensitive subnets may have stricter rules compared to less sensitive ones. - Allow Only Necessary Ports and Protocols:
Be specific when allowing inbound and outbound traffic. Only open the ports and protocols required for your applications to function. Avoid opening all ports unnecessarily. - Test Your Rules:
After creating NACL AWS rules, test them to ensure they work as intended. Test various scenarios, such as allowed and denied traffic, to verify that your NACL effectively enforces your security policies.
Conclusion
- NACLs are a security layer in AWS that acts as a virtual firewall for controlling inbound and outbound traffic to and from Amazon VPC (Virtual Private Cloud) resources.
- NACLs are stateless, meaning that rules for inbound and outbound traffic must be defined separately. Unlike Security Groups, NACLs don't keep track of connection states.
- Rules in NACLs are evaluated based on rule number and priority. Lower rule numbers have higher priority, and the first rule that matches a packet determines the action taken.
- Each rule in an NACL is defined with a rule number, protocol (TCP, UDP, or ICMP), a source IP or IP range, and an action (allow or deny).
- By default, an NACL allows all outbound and inbound traffic. Custom rules must be created to allow specific traffic.
- NACLs are associated with subnets within a VPC. Each subnet can be associated with only one NACL, but one NACL can be associated with multiple subnets.
