What are Namespaces?
What are Namespaces?
Namespaces are a Linux kernel feature introduced in the kernel version 2.6.24 in 2008 that provide processes with their isolated system view. Linux namespaces are used to isolate independent processes from one another.
Namespaces in Linux define a set of resources that a process can use. This way, the process cannot utilize the resources allocated to another process as it is isolated and cannot see the existence of other resources.
In a nutshell, namespaces in Linux provide fine-grained partitioning of global resources like mount points, IPC (inter-process communication) and network stack among multiple processes.
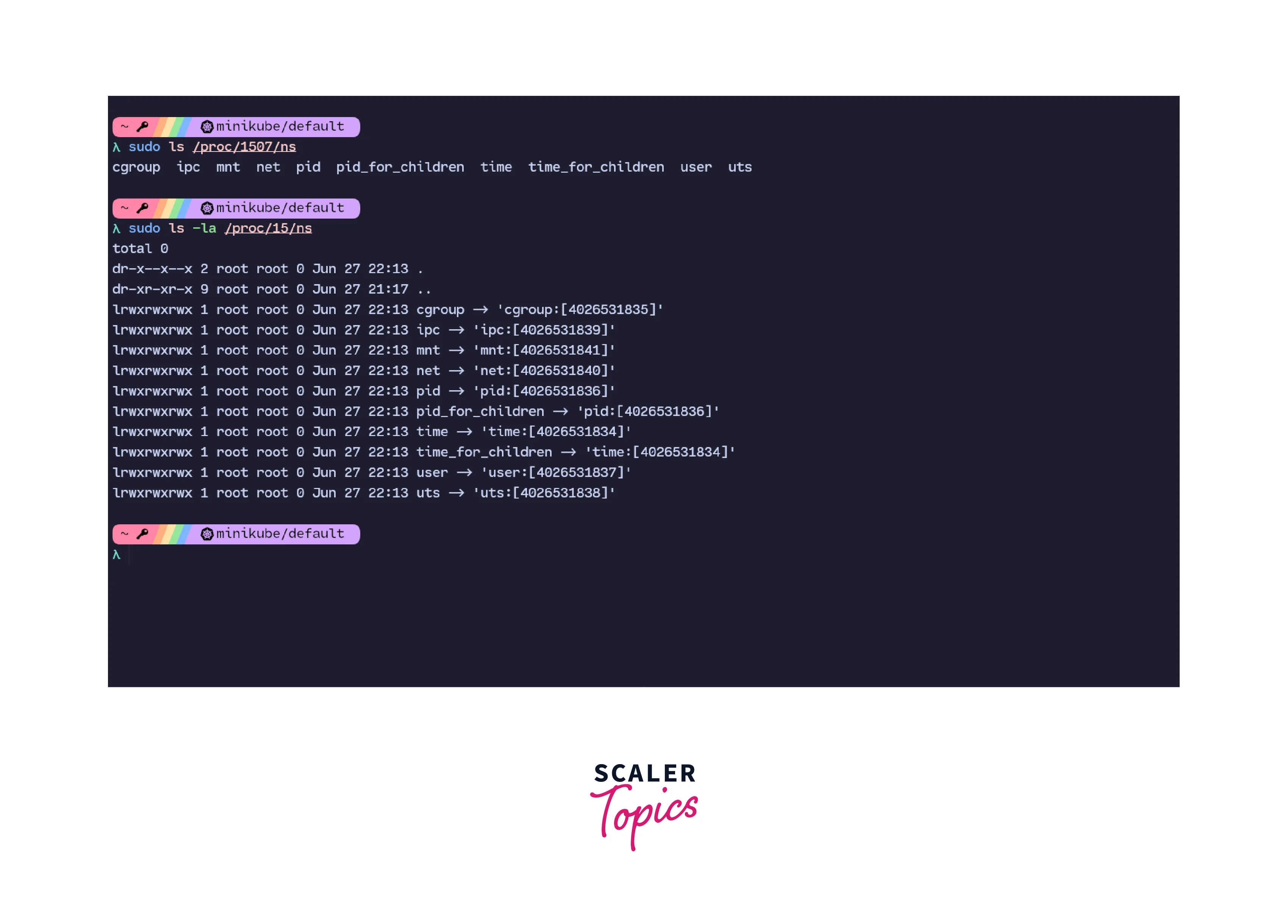
Namespaces in Linux are listed under /proc/<pid>/ns by the Linux kernel.
Why use Namespaces?
Linux namespaces provide resource isolation for processes. This not only provides a way to control how many resources a process can consume, but it also provides a security mechanism. Since namespaces in Linux provide very fine-grained control over resources used in a process, we can run processes that can pose a risk to the system securely in namespaces without affecting the entire system.
If a malicious process is executed inside a namespace, it might try to destroy the filesystem but because it is namespaced, its destructive behaviour does not cause damage to the working of other processes.
Linux namespaces are also used widely in the field of software containerization. Projects like Docker and LXC (Linux Containers) use namespaces to run isolated environments called containers. Namespaces in Linux also provide the ability to share specific processes like system mount points.
Creating a New Namespace
To create a namespace in Linux, we need to use the unshare command. Running the unshare --help command in a terminal gives us the following options:
To create a namespace in Linux, we use the unshare command followed by the flags we need to pass to create a new namespace.
For example, running the id command gives us the current user and their id.
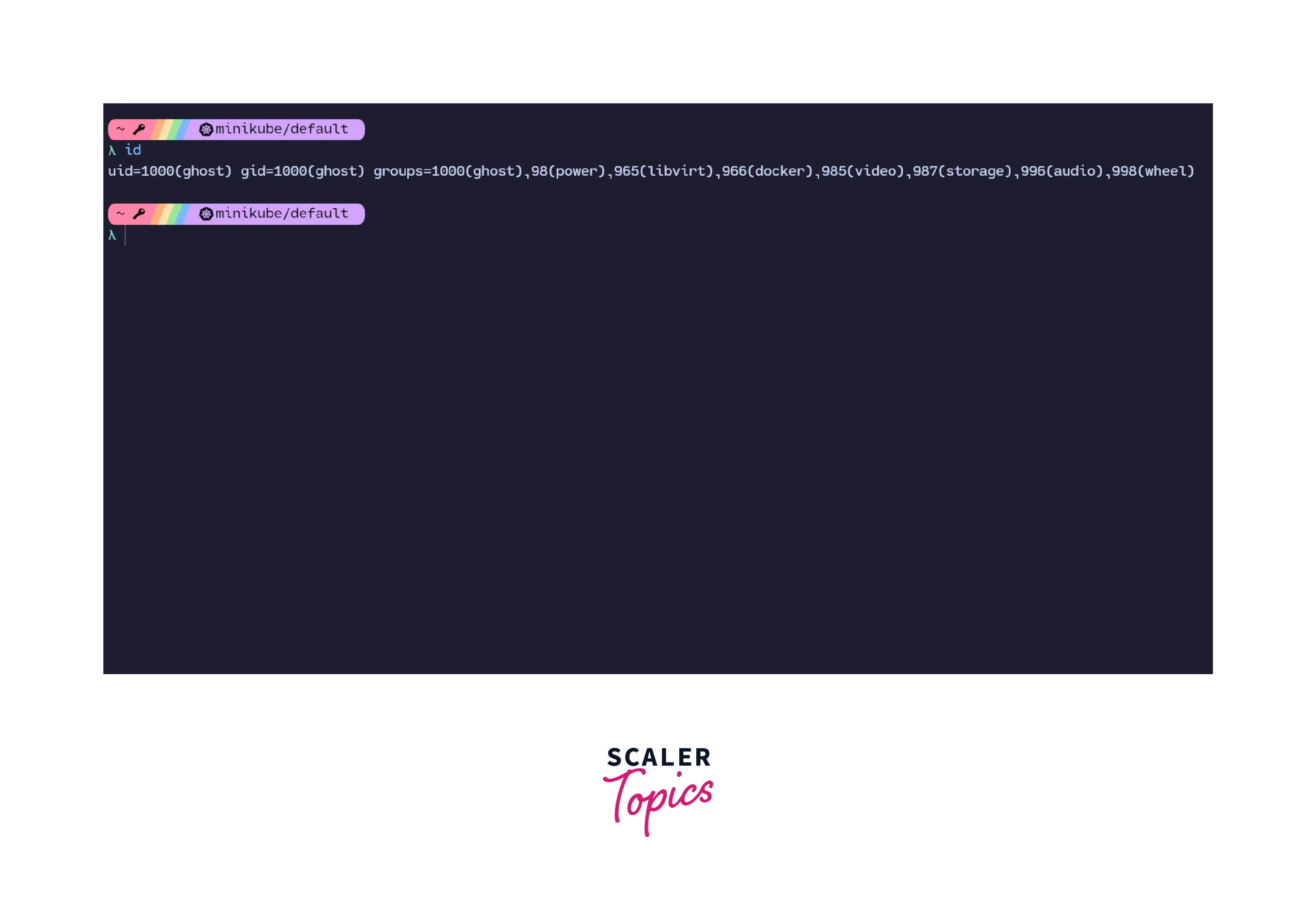
As can be seen in the image, the user is not root and currently has a uid of 1000 with a distinct shell prompt. Now if we create a new namespace, the user changes, as well as the prompt.
To create a new user Linux namespace, we can run the command:
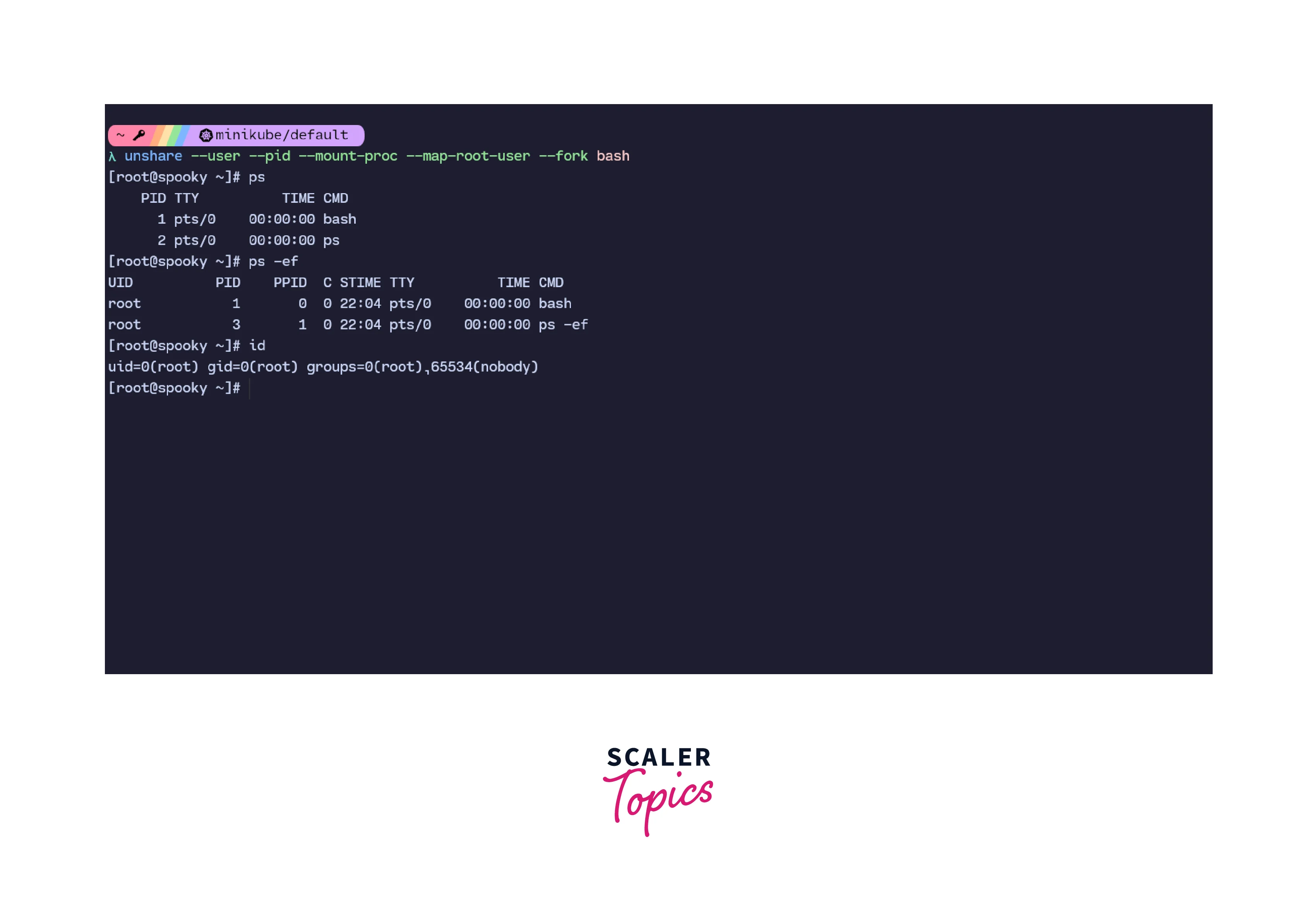
The previous command creates a new namespace in Linux with its own PID and user namespaces. The root user of the system is mapped to this namespace and the bash shell is forked. There is a change in the PID as well which is seen in the image, and the shell prompt is also different, giving us an idea of how Linux namespaces work.
Types of Namespaces
There are 8 types of different Linux namespaces:
1. PID Namespace:
Historically, the Linux kernel has always maintained a single process tree. This tree holds a reference to every process currently running in the kernel. These process trees are maintained with the help of a pseudo-filesystem called the procfs. With the help of the PID namespace, we can isolate independent processes from one another. So, processes do not have any idea of what is happening on the system outside their namespace. This way, we can also run multiple processes simultaneously which were not designed to run simultaneously. Let's take an example of PID 1. PID 1 is the first process that starts after the kernel boots, which is usually the init system which is responsible for starting other services and processes and maintaining the system. Most modern distributions use Systemd as their init system.
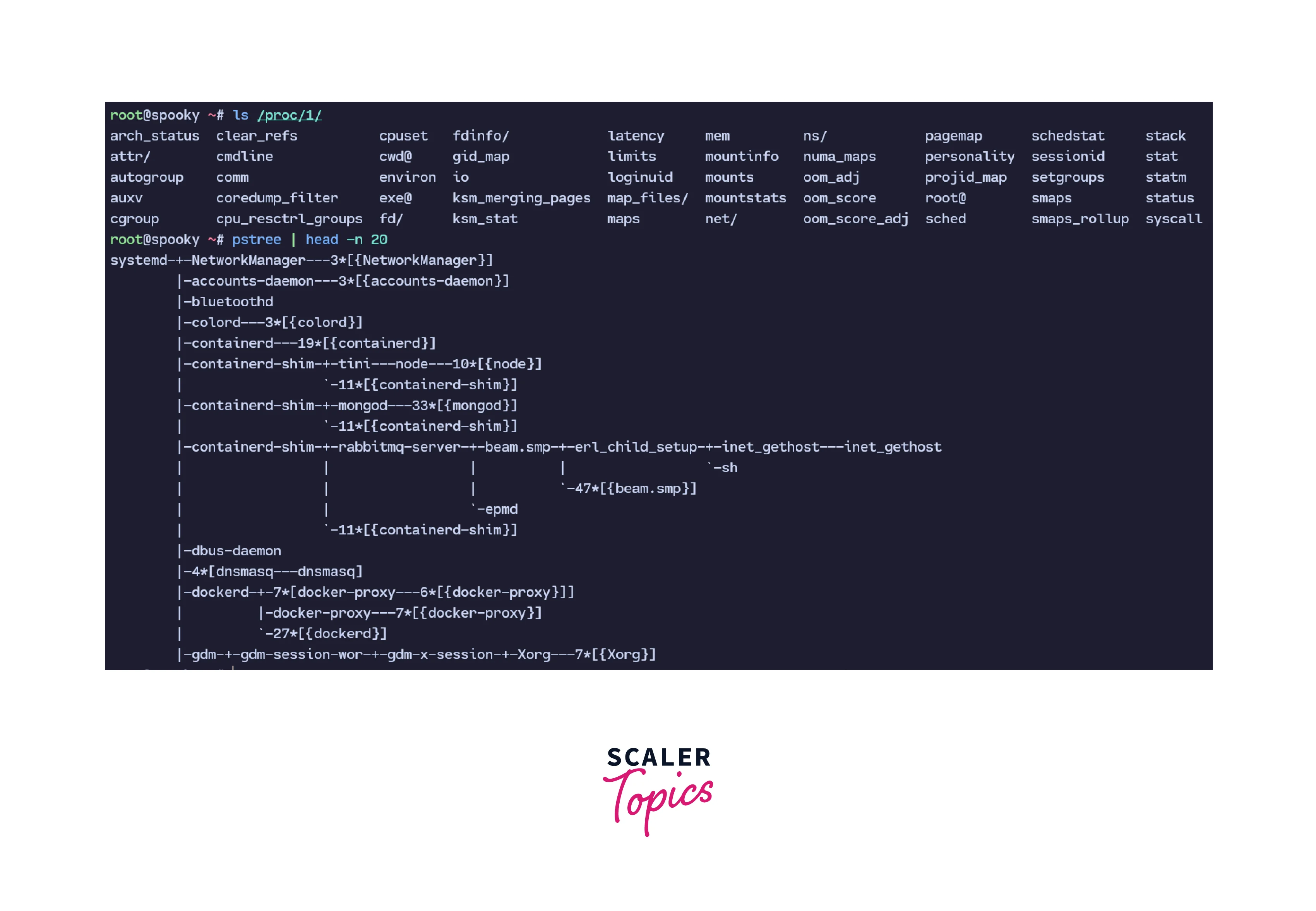 With the introduction of the PID namespace, it became possible to isolate resources and let other processes be PID 1 in their namespaces.
With the introduction of the PID namespace, it became possible to isolate resources and let other processes be PID 1 in their namespaces.
2. NET Namespace:
The NET namespace in Linux limits the limit of what the process can perceive in the host network. This allows a process to have its own network stack, completely separate from the host.
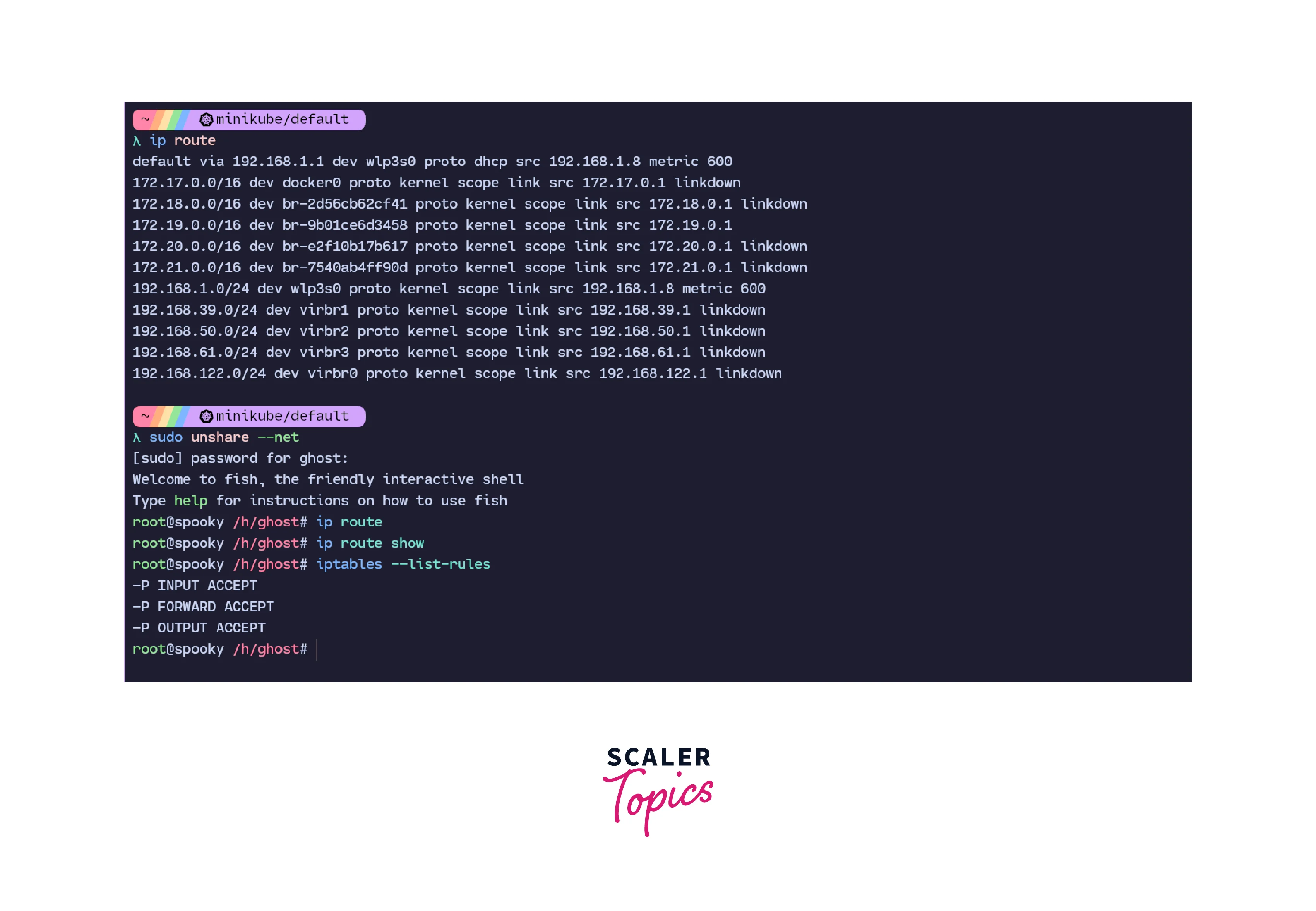
In the above image, the ip route command shows various routes for the current namespace but when a new NET namespace is created, it does not register any routes and hence, returns nothing. This shows the network stack isolation using the NET namespace.
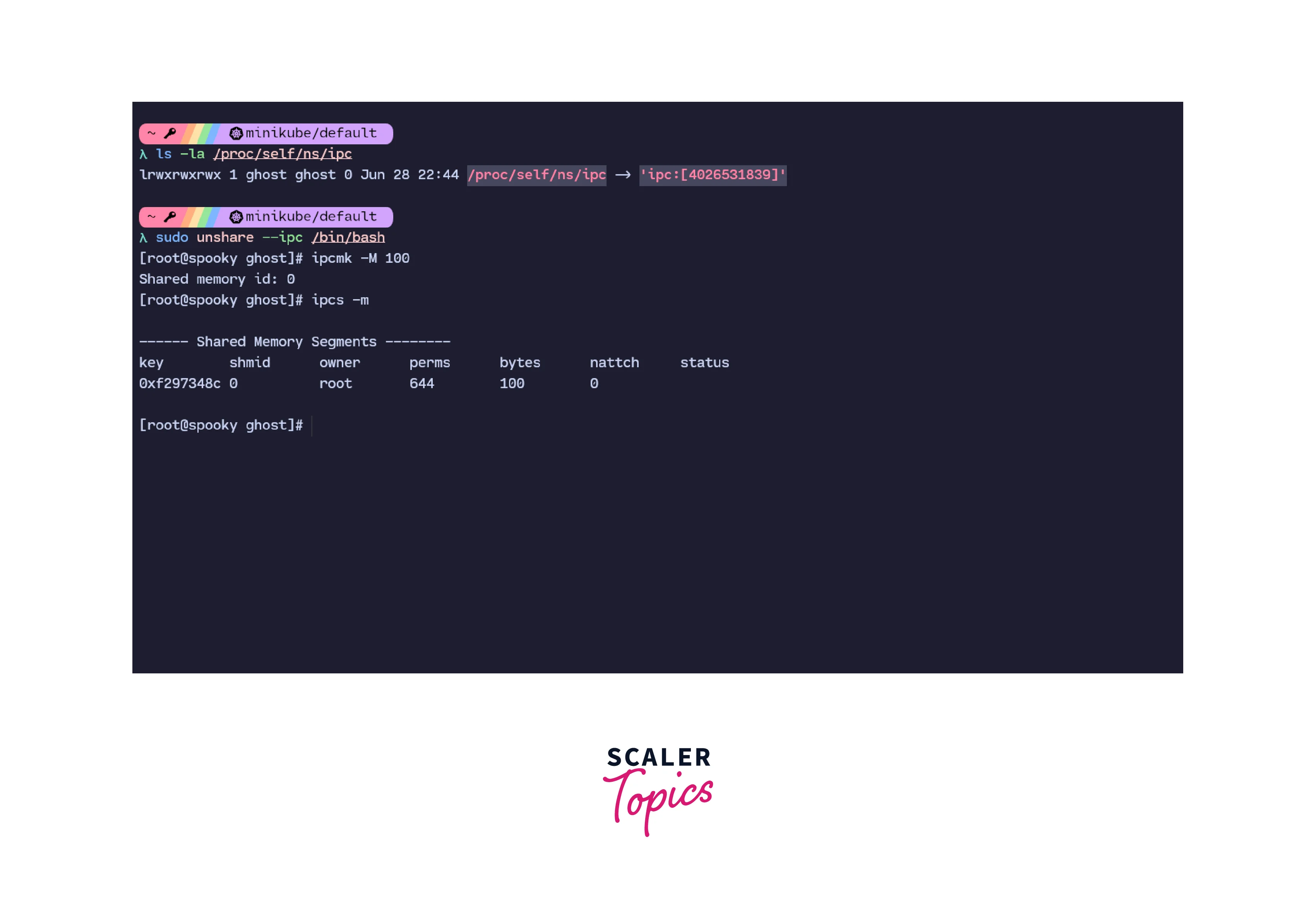
3. IPC Namespace:
IPC stands for Inter-Process Communication. As the term suggests, IPC defines how different processes communicate with each other. The IPC Linux namespace provides isolation of IPC objects like shared memory segments, message queues and semaphores. This namespace allows isolated processes in the same namespace to define shared memory segments for inter-process communications. This is done without interfering with the working of other namespaces.
4. UTS Namespace:
UTS stands for Unix Time Sharing namespace. The UTS Linux namespace is used to provide different and isolated hostnames and domain names to processes.
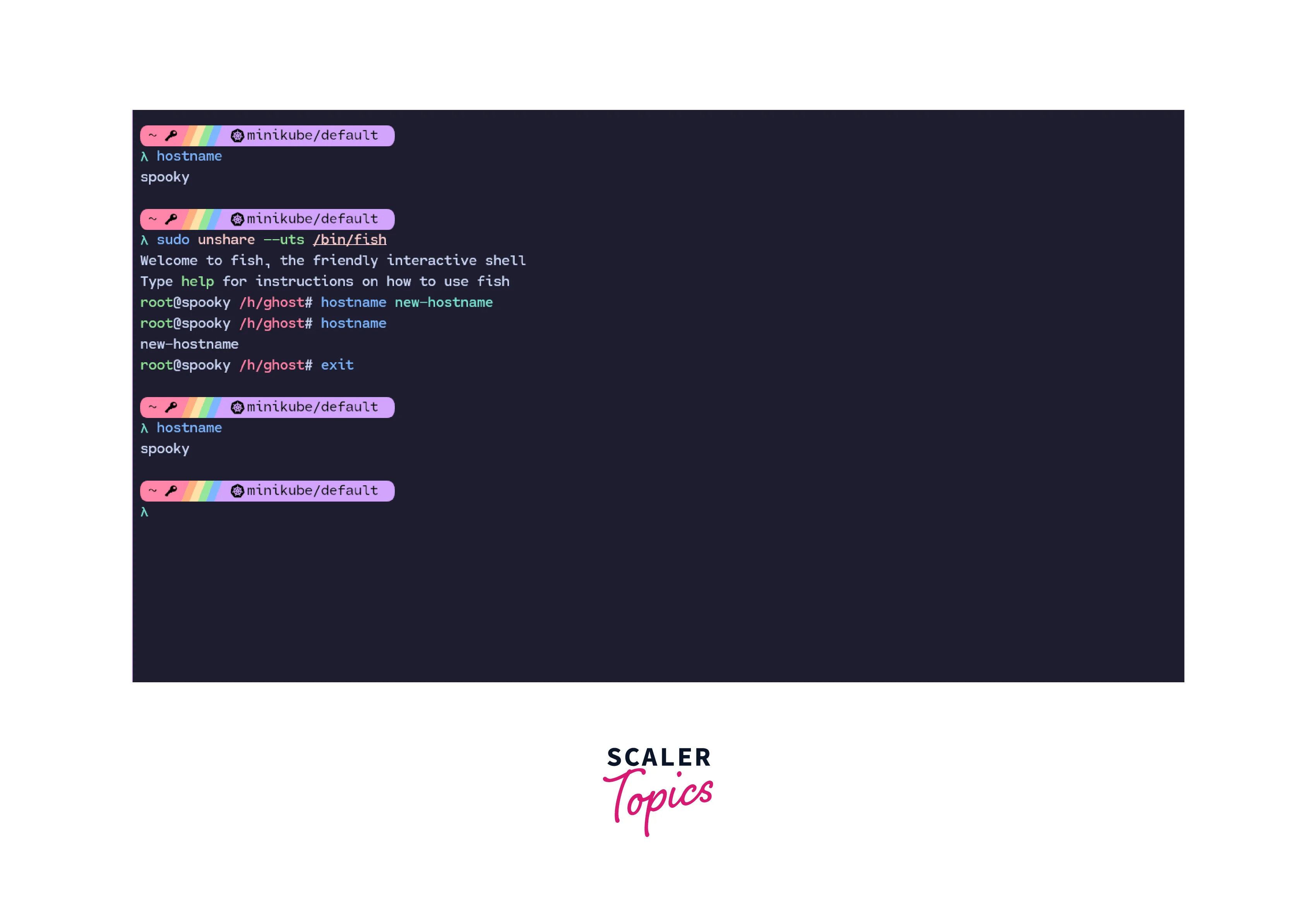
The first hostname returns the hostname of the current namespace. When we switch the namespace, we can change the hostname of the system in new namespace. But, when we switch back to our original namespace, we can see that we are back to using the actual hostname of the system. This is the isolation of hostnames and domain names provided by the UTS namespace in Linux.
5. USER Namespace:
The user namespace provides isolation in terms of security-related attributes and identifiers like user IDs and group IDs. This means that a process has full access and privileges for operations in its current namespace but does not have any access outside of its namespace.
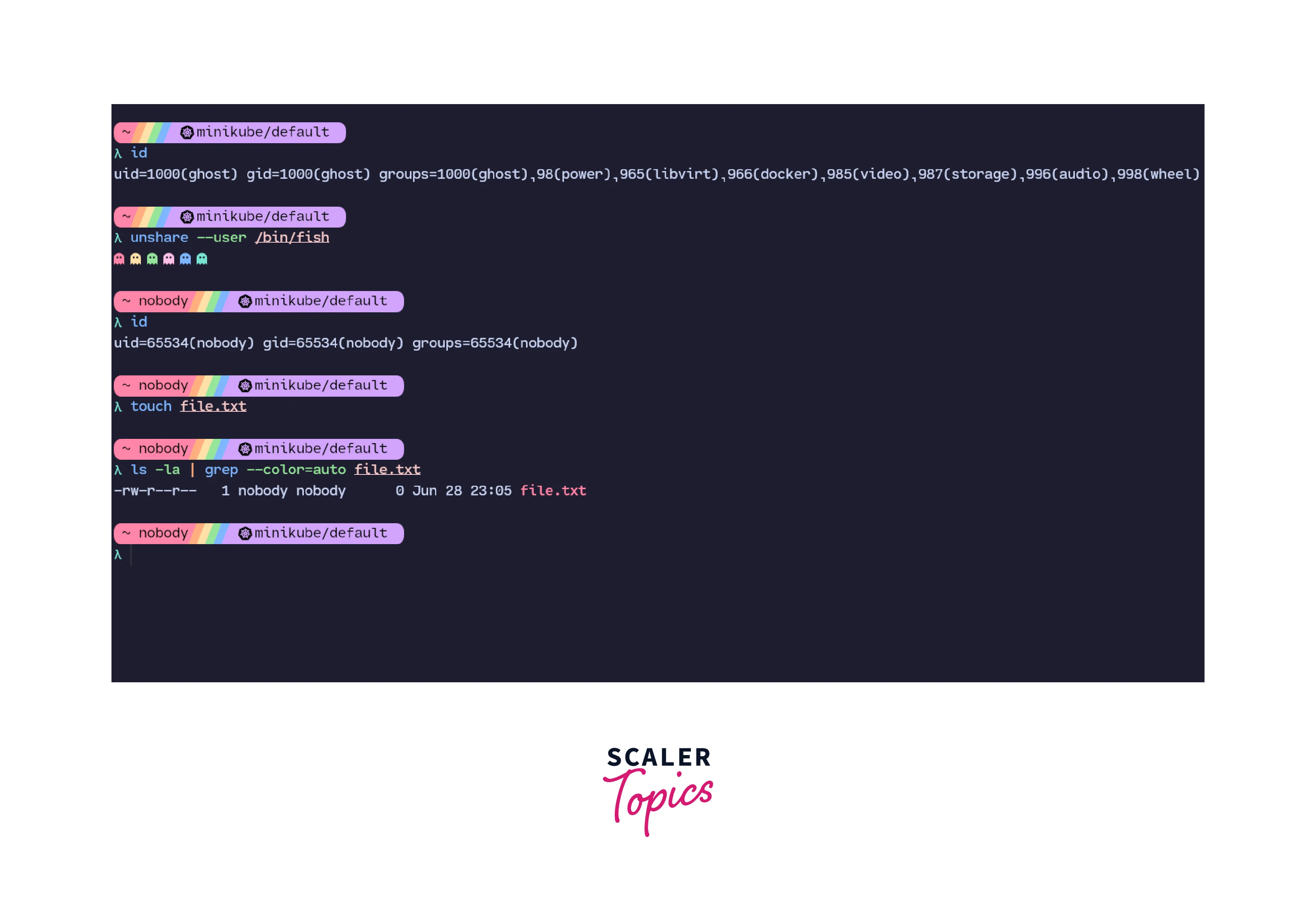
In the above image, in the current namespace, the user has an ID of 1000. But when we switch to a new User Linux namespace, we see that the user is nobody and has a different ID. Also, any files created by this user are owned by nobody and not by the user of the original namespace. From this, we can infer how the User namespace in Linux provides isolation of attributes like UIDs and group IDs.
6. MNT Namespace:
The MNT namespace represents the mount namespace. This namespace provides isolation of system mounts and mount points seen by a process. Every process has its mounts and changes in the mounts for one process do not change them for other processes. Mount namespace is very useful in tools used for containerization. This is because each container must have its own file system and file system configuration, independent of the host system.
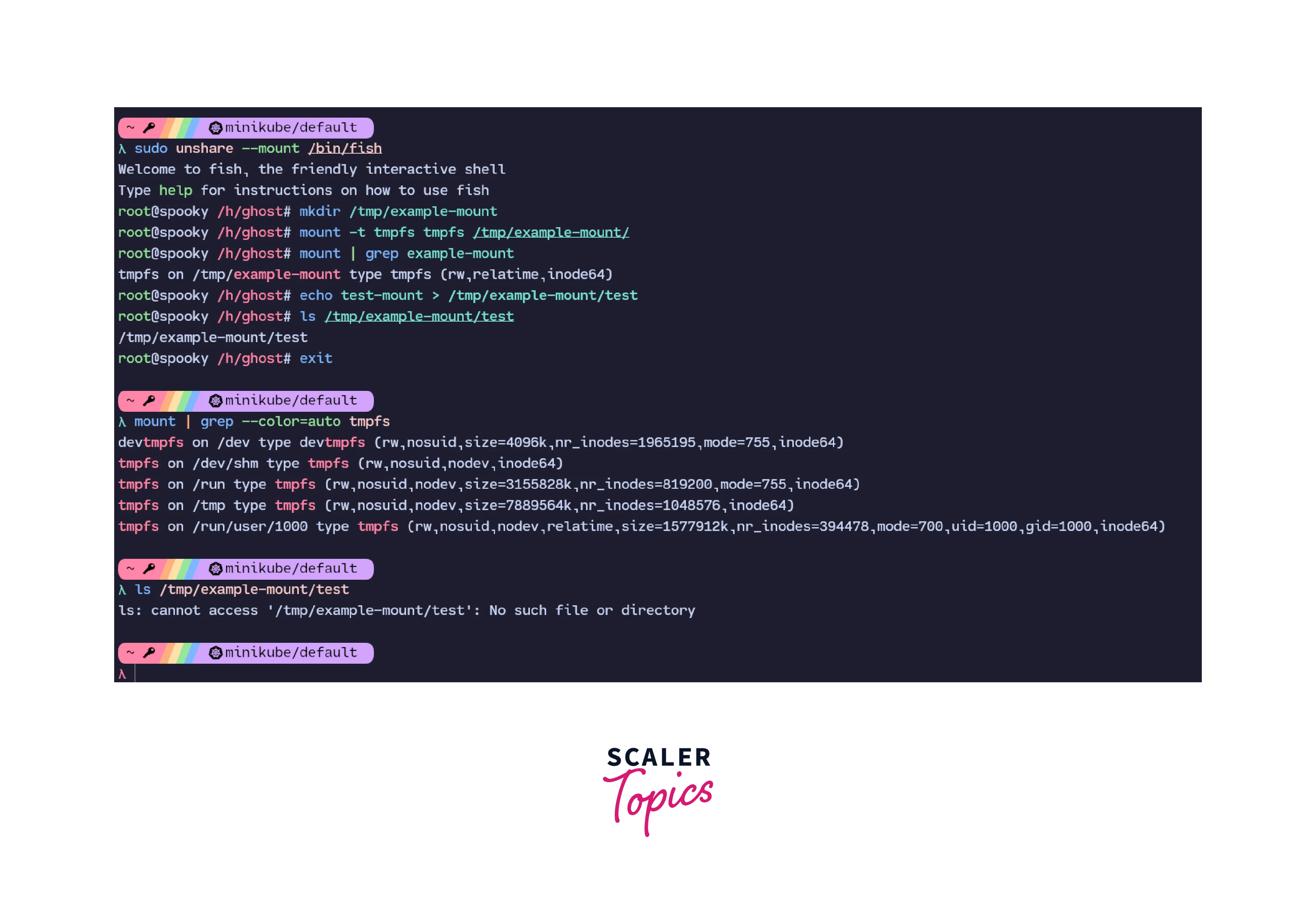
In the above picture, we first create a new mount namespace. We then go on to create a new directory under /tmp, mount this directory as a tmpfs and then create a new file example-mount in this newly mounted directory. We can prove that this file, as well as the mount point, exists. But when we switch back to the original namespace, we can see that neither the mount point is present in this namespace, and the file also does not exist. This demonstrates the isolation of mount points provided by the mount namespace in Linux.
7. CGROUP Namespace:
CGROUP stands for Control Groups. This namespace was introduced in 2016 as a part of the Linux kernel's 4.6 version release. We can control, limit and virtualize the amount of resources consumed by a process using Cgroups. Cgroups are created in the /sys/fs/cgroup virtual file system directory. Cgroup namespaces in Linux, in essence, virtualize another file system as the namespace for a process with some PID. This virtualization provides isolation of system resources. This isolation aims to prevent information leaks. With the use of cgroups, the directory path outside this cgroup directory is not visible to a process. We can create cgroups by writing into the /sys/fs/cgroups directory:
Here, we are assigning fifty MB of memory limit. Now we can assign a process to this limit:
This process will now have a limit of 50 MB memory usage and will be killed by the kernel if it crosses this limit.
8. Time Namespace:
The time namespace is used to allow different system times within the same system. This is especially useful for cases like containers where we might need a different time than the host. The time namespace was recently added to the Linux kernel in 2020. We can create a time namespace by running:
Learn more
Conclusion
- Namespaces are a Linux kernel feature used to isolate independent processes from each other. There are 8 types of namespaces in Linux: mount, user, UTS (Unix Time Sharing), cgroup, IPC (Inter-process communication), Net, PID (Process ID) and time.
- Linux namespaces are heavily used in cases like containers to provide isolation to the container processes.
- We create new namespaces with the help of the unshare command.
