Azure Network Security Group (NSGs)
Overview
Azure is Microsoft's cloud computing platform, offering a wide array of services for building, deploying, and managing applications and infrastructure. It encompasses Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) solutions. Azure's services span data management, AI and machine learning, IoT, DevOps, and security, with a strong focus on hybrid cloud capabilities for seamless integration of on-premises and cloud resources. It provides a global network of data centers, making it a leading choice for organizations seeking scalability, agility, and innovation in the digital era.
What is Azure Network Security Group (NSGs)?
Azure Network Security Groups (NSGs) are a fundamental component of Azure's network security offerings. They act as a virtual firewall, allowing you to control inbound and outbound network traffic to and from Azure resources, including virtual machines, virtual networks, and Azure App Service Environments. NSGs are rule-based and can be associated with subnets or individual network interfaces.
Key features and functions of Azure NSGs include:
- Filtering Traffic:
NSGs enable you to define rules that allow or deny specific types of traffic based on source and destination IP addresses, ports, and protocols. - Priority Rules:
Rules in an NSG are processed based on priority. The rule with the lowest priority that matches the traffic criteria is applied. - Stateful Inspection:
NSGs are stateful, meaning they keep track of the state of established connections, allowing response traffic for outbound connections without requiring specific rules. - Default Rules:
When you create an NSG, it includes default rules that permit outbound traffic and deny inbound traffic unless you add custom rules. - Logging and Monitoring:
NSGs can be configured to log network traffic, helping with security analysis and compliance monitoring. - Application Security Groups (ASGs):
ASGs can be used in conjunction with NSGs to simplify the management of network security rules for a group of resources with similar security requirements.
Azure NSGs play a crucial role in securing your Azure resources by controlling network traffic and implementing network security policies to protect against unauthorized access and potential threats. They are an essential part of building secure and compliant Azure environments.
How does it Work?
Azure Network Security Groups (NSGs) work by applying a set of network security rules to control inbound and outbound traffic to and from Azure resources. Here's how they work:
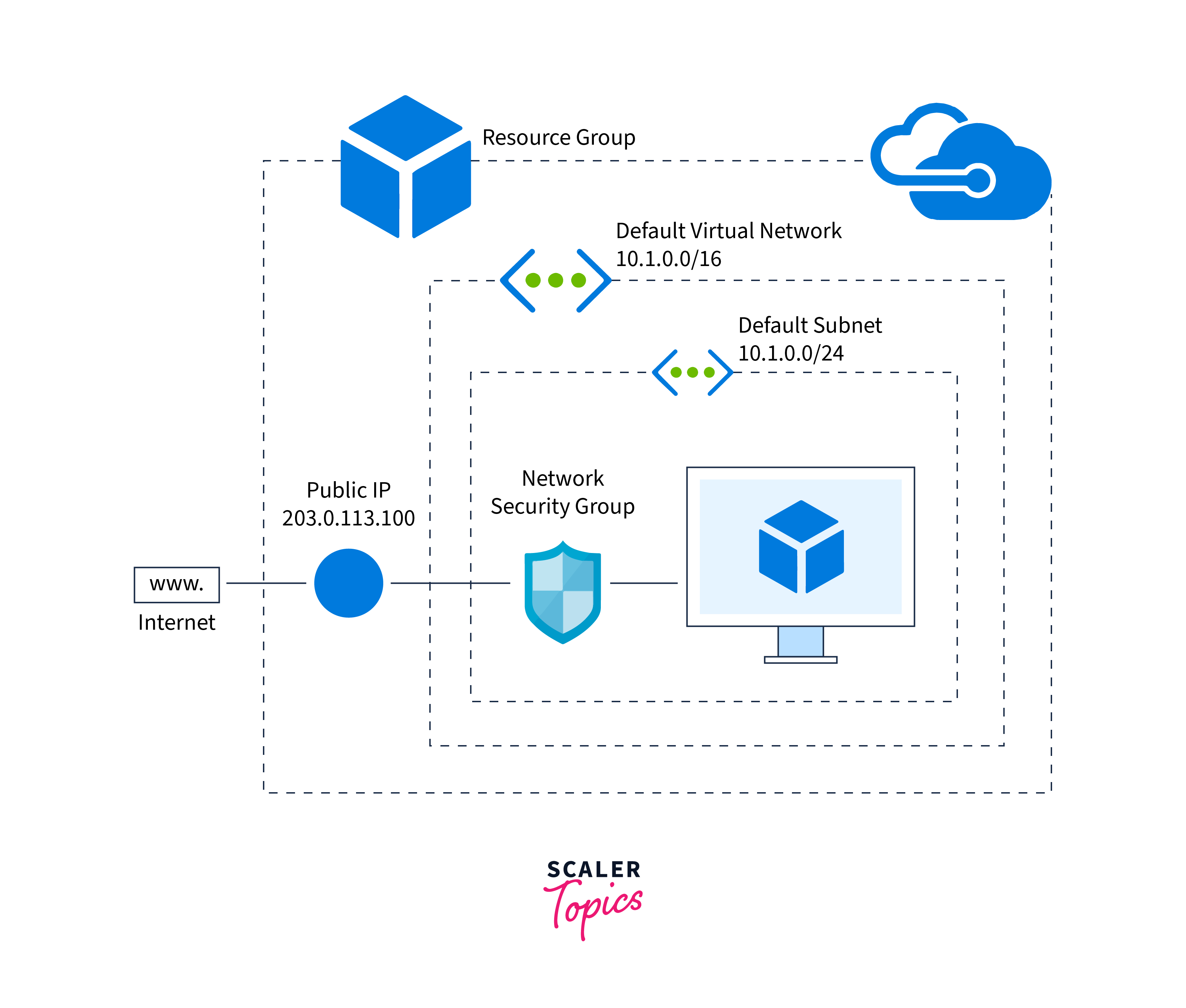
- Rule-Based Access Control:
NSGs operate based on a rule-based access control model. You define rules specifying the allowed or denied traffic based on criteria such as source IP addresses, destination IP addresses, ports, and protocols. - Rule Priority:
Each rule in an NSG has a priority assigned to it. When network traffic enters or exits a virtual network or subnet associated with an NSG, the rules are processed in priority order. The rule with the lowest priority that matches the traffic criteria is applied. You can have both allow and deny rules, and the most specific rule takes precedence. - Stateful Inspection:
NSGs are stateful, meaning they keep track of the state of established connections. When you allow outbound traffic, the NSG automatically permits the response traffic for established connections without requiring explicit rules. This simplifies the rule set and enhances security. - Default Rules:
When you create an NSG, it includes default rules that permit outbound traffic (e.g., allowing all outbound traffic to the internet) and deny all inbound traffic. These defaults can be customized to meet your specific needs. - Association with Resources:
NSGs can be associated with Azure resources at the subnet level or with individual network interfaces. When associated with a subnet, the rules apply to all resources within that subnet. When associated with a network interface, the rules apply to traffic specific to that interface. - Logging and Monitoring:
NSGs can be configured to log network traffic, providing visibility into the traffic that matches your rules. You can analyze these logs for security analysis, troubleshooting, and compliance monitoring. - Dynamic Updates:
NSGs are dynamic, allowing you to modify and update rules as your security requirements change. You can also associate or disassociate NSGs with resources as needed.
By defining and configuring NSGs, you can implement a robust network security posture within your Azure environment. They are a critical component for securing your virtual networks and resources, ensuring that only authorized traffic is allowed while denying or blocking unwanted and potentially harmful traffic.
Security Rules
In Azure Network Security Groups (NSGs), security rules are used to control inbound and outbound network traffic to and from Azure resources. There are default security rules and augmented security rules.
Default Security Rules
Default security rules for inbound traffic typically refer to the predefined rules or policies that control and manage incoming network traffic to a device, server, or network infrastructure. These rules are commonly found in firewalls, routers, or other network security devices and are set up to protect the network from unauthorized access and potential security threats
-
Inbound Security Rules:
These rules control traffic entering an Azure resource, such as a virtual machine, from external sources. By default, when you create an NSG, it includes a default inbound security rule that denies all inbound traffic. You can customize and add additional rules to permit specific types of inbound traffic as needed. -
Outbound Security Rules:
These rules govern traffic leaving an Azure resource and going to external destinations, such as the internet or other Azure services. By default, when you create an NSG, it includes a default outbound security rule that allows all outbound traffic. You can customize and add outbound rules to restrict or control specific outbound traffic.
Augmented Security Rules
Augmented security rules are custom security rules that you create to supplement the default security rules. You can add these rules to define more specific access controls for your Azure resources. Augmented security rules can be used to allow or deny traffic based on criteria such as source IP addresses, destination IP addresses, ports, and protocols. These rules allow you to tailor the security of your resources to meet your specific requirements.
For example, you might create augmented security rules to:
- Allow inbound traffic on a specific port for a web server.
- Deny inbound traffic from a specific IP address range known for malicious activity.
- Permit outbound traffic to a specific IP address for a database server.
By combining default and augmented security rules in an NSG, you can fine-tune the network security for your Azure resources, ensuring that only authorized traffic is allowed and unauthorized or potentially harmful traffic is denied. This helps enhance the security posture of your Azure environment.
Azure Platform Considerations
When considering the Azure platform for your organization's cloud computing needs, there are several important factors and considerations to keep in mind:
- Business Objectives:
Begin by defining your organization's business objectives and IT goals. Determine how Azure can align with and support these objectives, whether it's reducing operational costs, enhancing scalability, improving agility, or enabling innovation. - Workload Compatibility:
Assess the compatibility of your workloads with Azure. While Azure supports a wide range of applications and services, certain legacy systems or highly specialized workloads may require additional planning or customization for migration. - Cost Management:
Understand Azure's pricing model and estimate your expected costs. Azure offers various pricing options, including pay-as-you-go, reserved instances, and consumption-based billing. Implement cost management tools and practices to optimize your cloud spending. - Security and Compliance:
Azure provides robust security features, but it's essential to configure and manage them correctly. Evaluate Azure's security offerings, including Azure Active Directory, Azure Security Center, and network security groups. Ensure compliance with industry regulations and data protection requirements. - Data Management:
Consider your data storage and management needs. Azure offers various data services, including Azure SQL Database, Azure Cosmos DB, and Azure Blob Storage. Plan for data migration, backups, and disaster recovery. - Networking and Connectivity:
Design your Azure network architecture to meet performance, availability, and security requirements. Azure provides virtual networks, VPN gateways, ExpressRoute for private connectivity, and Azure Load Balancer for high availability. - Hybrid Cloud Integration:
Determine if you need hybrid cloud capabilities to integrate on-premises infrastructure with Azure. Azure offers solutions like Azure Arc for managing on-premises resources and Azure Stack for running Azure services on your infrastructure. - Scalability and Availability:
Leverage Azure's scalability and high availability features to ensure your applications remain responsive and accessible. Use Azure Availability Zones and Azure Auto Scaling to enhance resilience. - Monitoring and Management:
Implement monitoring and management solutions like Azure Monitor and Azure Management Groups to gain insights into your Azure resources' performance and health. Set up alerts and automation for proactive management.
How to Create Network Security Groups in Azure?
To create Network Security Groups (NSGs) in Azure, you can follow these steps using the Azure Portal:
-
Sign in to Azure Portal:
Log in to your Azure account at https://portal.azure.com/.
-
Navigate to Network Security Groups:
Once logged in, you can navigate to the Network Security Groups section by either:
- Clicking on "Create a resource" and search for "Network Security Group", then selecting it.
- In the Azure Portal's left-hand menu, click on "All services", search for "Network Security Groups", and select it.
-
Create a New NSG:
To create a new NSG, click the "+ Add" button.
-
Basic Settings:
Fill in the basic information for your NSG, including the subscription, resource group, and a unique name for the NSG.
-
Region:
Select the Azure region where you want to deploy the NSG. This region does not need to match the region of your resources; NSGs can be associated with resources in different regions.
-
Inbound Security Rules and Outbound Security Rules:
You can configure inbound and outbound security rules based on your requirements. These rules define which traffic is allowed or denied. To add a rule:
- Click "Inbound security rules" or "Outbound security rules".
- Click the "+ Add" button.
- Configure the rule by specifying the name, source, source port range, destination, destination port range, protocol, action (allow or deny), and priority (lower numbers have higher priority).
-
Associating NSG with Resources:
After creating the NSG and defining security rules, you need to associate it with Azure resources, such as virtual machines or subnets. To do this:
- Locate the resource you want to associate with the NSG.
- In the resource settings, find the "Networking" or "Security" section, depending on the resource type.
- Add the NSG to the appropriate network interfaces, subnets, or resources.
-
Review and Create:
Review the settings to ensure they meet your requirements, and then click the "Review + create" button.
-
Validation and Deployment:
Azure will validate your NSG configuration. If everything is in order, click the "Create" button to deploy the NSG.
Azure NSG Best Practices
Implementing Network Security Groups (NSGs) effectively in Azure requires the following best practices to enhance security, manageability, and performance:
- Plan and Document Your NSG Strategy:
- Clearly define your network security requirements and objectives before creating NSGs.
- Document the purpose and rules for each NSG to maintain an organized and understandable security posture.
- Use Azure Policy for Governance:
- Implement Azure Policy to enforce naming conventions, rule configurations, and compliance standards consistently across NSGs and resources.
- Least Privilege Principle:
- Follow the principle of least privilege when creating NSG rules. Only allow necessary traffic and deny everything else.
- Rule Prioritization:
- Assign priorities to NSG rules to control rule evaluation orders effectively. Rules with lower priorities are processed first.
- Consider using higher priority deny rules to block unwanted traffic before allowing specific traffic.
- Avoid Broad Allow Rules:
- Minimize the use of "Any" as the source or destination in NSG rules. Instead, use specific IP ranges or service tags to limit exposure.
- Use Application Security Groups (ASGs):
- Implement ASGs to simplify the management of NSG rules for groups of resources with similar security requirements. This enhances rule readability and maintenance.
- Logging and Monitoring:
- Enable NSG flow logs to capture information about allowed and denied traffic.
- Use Azure Monitor to set up alerts and analyze NSG flow data for security and compliance monitoring.
- Network Peering Considerations:
- If you have virtual networks peered together, understand how NSGs are evaluated across peered networks. Rules should be aligned with your network architecture.
- Regularly Review and Update Rules:
- Conduct periodic reviews of your NSG rules to ensure they align with changing security requirements.
- Remove unnecessary or outdated rules to reduce complexity and improve performance.
- Testing and Validation:
- Before deploying NSGs in a production environment, thoroughly test them in a staging or development environment to ensure they do not disrupt critical services.
- Use Service Tags:
- Leverage Azure's service tags to simplify rule creation. Service tags represent predefined IP address ranges for Azure services like Azure Storage or Azure SQL Database.
- Monitoring and Incident Response:
- Establish an incident response plan for NSG-related security events. Regularly review NSG logs to identify and respond to potential security threats promptly.
- Plan for Scalability:
- Design NSGs with scalability in mind to accommodate future growth. Consider the impact of adding more resources or expanding to different regions.
- Integration with Azure Services:
- Azure Network Security Groups (NSGs) can be integrated seamlessly with other Azure services to enhance overall security. When used alongside Azure Firewall, NSGs help filter traffic at the subnet or network interface level, complementing the higher-level protection provided by Azure Firewall. Additionally, when combined with Azure Security Center, NSGs can contribute to a comprehensive security strategy by providing network-level controls that align with security policies and recommendations, ensuring a more robust defense against threats and vulnerabilities across Azure resources.
- Troubleshooting and Tips:
- Misconfigured Rules:
Check rule priorities, ensuring more specific rules come before general ones. - Logging:
Enable NSG flow logs to identify traffic issues and rule violations. - Resource Associations:
Verify that NSGs are correctly associated with resources, like subnets or NICs. - Default Rules:
Be cautious with default deny inbound rules; create necessary allow rules. - Rule Testing:
Use Azure Network Watcher's "Security Group View" to simulate rule evaluations. - Concurrency:
Avoid exceeding NSG rule limits; consider merging rules for efficiency.
- Misconfigured Rules:
Azure NSG Capabilities
Azure Network Security Groups (NSGs) provide a range of capabilities for controlling network traffic to and from Azure resources. Here are the key capabilities and features of Azure NSGs:
- Traffic Filtering:
NSGs allow you to define rules that specify which traffic is allowed or denied based on various criteria, including source and destination IP addresses, ports, and protocols. - Inbound and Outbound Rules:
NSGs support both inbound and outbound security rules. Inbound rules control traffic coming into Azure resources, while outbound rules govern traffic leaving Azure resources. - Stateful Filtering:
NSGs are stateful, meaning they keep track of the state of established connections. This enables response traffic for outbound connections without requiring specific rules. - Rule Prioritization:
NSG rules have priorities, and the rule with the lowest priority that matches the traffic criteria is applied. This allows you to control rule evaluation orders effectively. - Default Rules:
When you create an NSG, it includes default rules that permit outbound traffic and deny inbound traffic. These defaults can be customized to meet your specific requirements. - Logging and Monitoring:
NSGs can be configured to log network traffic, which can be useful for security analysis, troubleshooting, and compliance monitoring. You can also integrate NSG flow logs with Azure Monitor and Azure Security Center. - Application Security Groups (ASGs):
ASGs can be used in conjunction with NSGs to simplify the management of security rules for groups of resources with similar security requirements. ASGs enhance rule readability and maintenance. - Dynamic Updates:
NSGs are dynamic, allowing you to modify and update rules as your security requirements change. You can add, remove, or modify rules without disrupting network traffic. - Resource Association:
NSGs can be associated with Azure resources at the subnet level or with individual network interfaces. This enables you to control traffic for specific resources or groups of resources. - Service Tags:
Azure provides predefined service tags representing IP address ranges for Azure services like Azure Storage, Azure SQL Database, and more. You can use these service tags in NSG rules to simplify rule creation. - Integration with Azure Virtual Networks:
NSGs seamlessly integrate with Azure Virtual Networks, allowing you to apply network security policies at the network level. - Azure Firewall Integration:
You can integrate NSGs with Azure Firewall to add a layer of security for traffic leaving your virtual network.
Conclusion
- Azure NSGs are a network security feature that filters inbound and outbound traffic to and from Azure resources, acting as a virtual firewall.
- They operate on a rule-based system, allowing you to define rules to permit or deny traffic based on source/destination IP, port, and protocol.
- NSGs are associated with Azure resources such as virtual machines, subnets, or network interfaces, providing granular control at the resource level.
- By default, NSGs deny all inbound traffic and allow all outbound traffic, requiring custom rules for specific configurations.
- NSGs are stateful, meaning that if you create an inbound rule to allow traffic from a specific source, the corresponding outbound response is automatically permitted.
- Azure provides logging and monitoring capabilities to track and analyze network traffic and NSG rule effectiveness.
- NSGs are used for security segmentation, helping organizations enforce security policies and restrict unauthorized access.
