Playfair Cipher Program in C

Overview
playfair cipher program in c is a manual symmetrical encryption technique that is used to encrypt or encode a message. As this technique uses the same key for encryption and decryption, so this technique falls under the category of symmetrical encryption technique. It was the first literal digraph substitution cipher. Playfair Cipher was the successor of traditional monoalphabetic ciphers that was able to encrypt only a single letter. In this algorithm, two letters are paired and then encrypted.
What is Playfair Cipher?
The playfair cipher program in c is a multi-letter symmetrical encryption technique. This technique was first invented by Charles Wheatstone in 1854. Then you think why the name of the technique is not related to the name of the inventor this is because Lord Playfair promoted this technique later on at a very high pace, so the technique was named after his name. In this technique, a pair of letters are encrypted instead of a single letter. In the Playfair Cipher technique, suppose if the plaintext letter 'd' is replaced as 'm' for the next occurrence of 'd', it may not be 'm'. It could be a different character. Obviously, this will be confusing for the attackers because 'd' will be encrypted as different letters instead of a one to one mapping. This is the concept of the multi-letter encryption technique which improves the security as compared to other ciphers. This technique is also known by some other names such as Playfair square, Wheatstone-Playfair cipher, or Wheatstone cipher.
Encryption Technique
When a message is sent by the sender and received by the receiver, the message travels through some intermediate channels which are essential for transferring a message. There are chances of hacking the message in between transmission. So "Encryption Techniques" are used to secure this message and make delivery of the message without any intervention. The Playfair Cipher technique is a symmetrical encryption technique that encodes two letters of a message at a time. Let us see how the Playfair Cipher encryption algorithm works in the playfair cipher program in c.
The Playfair Cipher Encryption Algorithm
The Playfair Cipher technique is done in two steps which are given below. In this technique, some parameters are given and some parameters we need to find, in this algorithm. For example- The given parameters are the message which is the "plain-text" that we need to convert into the cipher-text and the second thing is the "keyword" that we need to write into the matrix structure of 5*5.
-
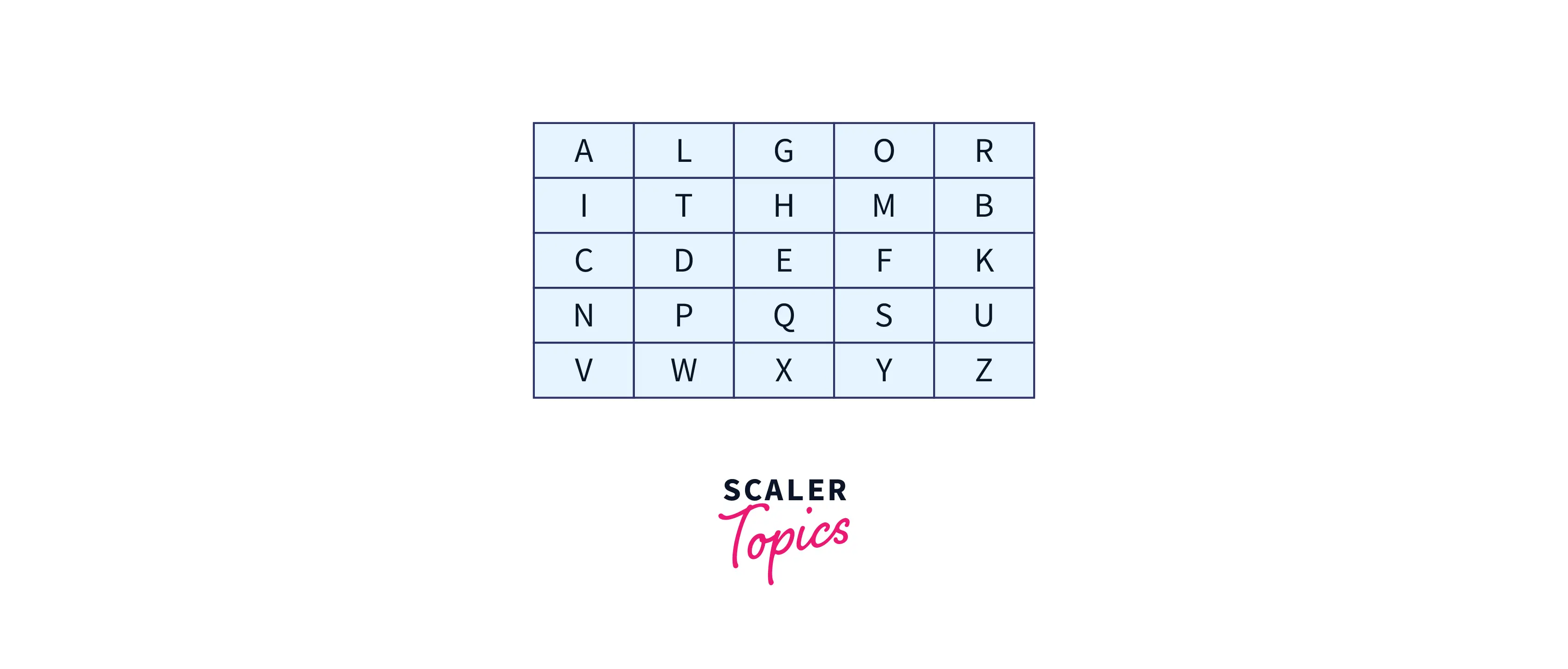
Generate the Key Square(5×5): First, a square box that consists of a 5*5 grid is made in which we need to write the keyword. This text box works as the key using which we will encrypt the plain text. In this key, the alphabet is filled in each box. All the alphabet should be unique. Generally, the letter "J" is removed from the key because the key square can contain only 25 letters. But, if there is "J" already present in plain text then it is replaced by "I".
-
Algorithm to Encrypt the Plain Text: The plain text that we need to encrypt, is split into pairs of letters (digraphs). After splitting the plain text, if the number of letters is odd, then a 'Z' is added to the last letter. Also, the letters inside a pair should be unique. All the unique letters from left to right of Keyword are filled in the grid and then the rest grids are filled with the remaining letters of alphabets. For example, we have 'Chipher' as plain text. After splitting it will be- ( Ch, ip, he, and rz).
In some cases, when there is the repetition of a letter in the text then pair is not made with the same text. A bogus letter is added to each repeated text. Suppose we have 'Hello' as plain text. So, the text will split like this- ( 'he', 'lx, 'lo' ) Here 'x' is the bogus letter.
All about the rules is that there should be uniqueness maintained throughout the cells of the key. After filling the grids for keyword "ALGORITHM" as explained above, the box will look like this-
Rules for Encryption
There are some specific rules for encrypting the plain text in the concept of "playfair cipher program in c" into the key that are as follows:
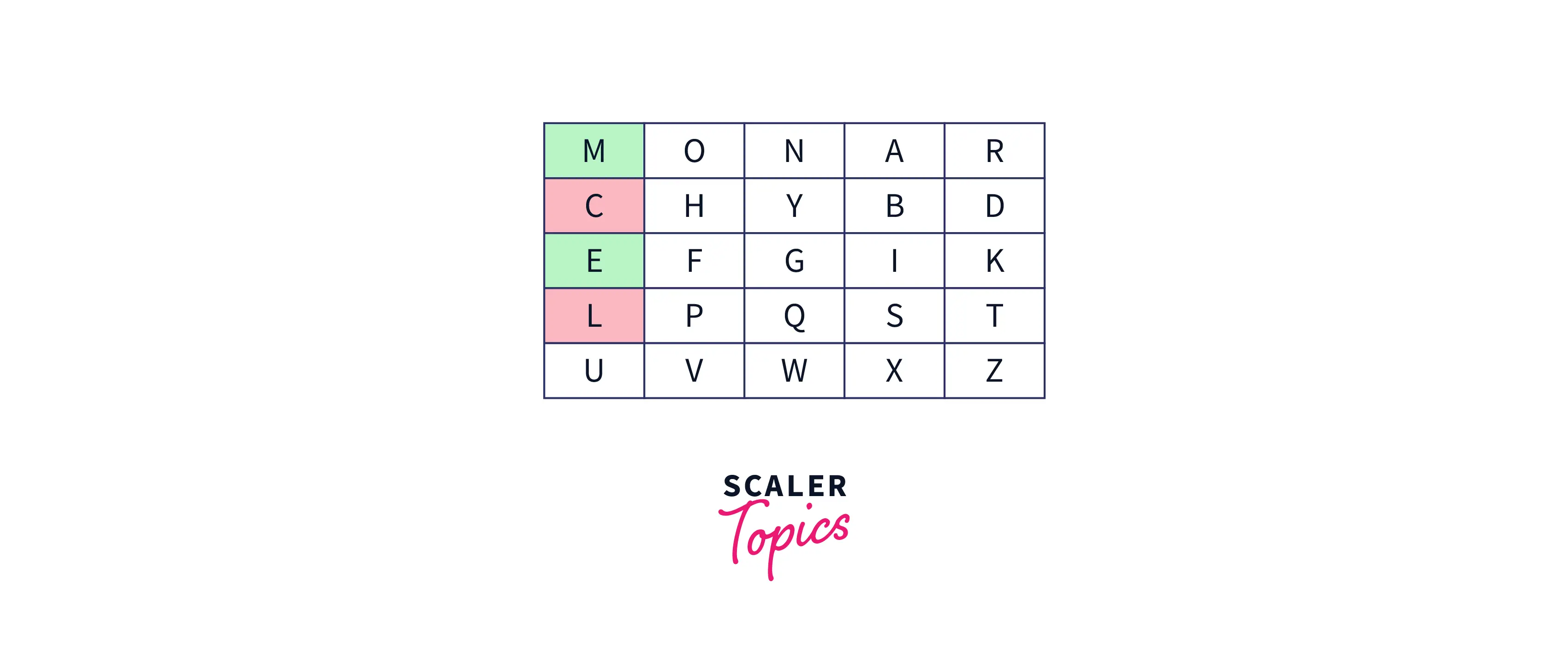
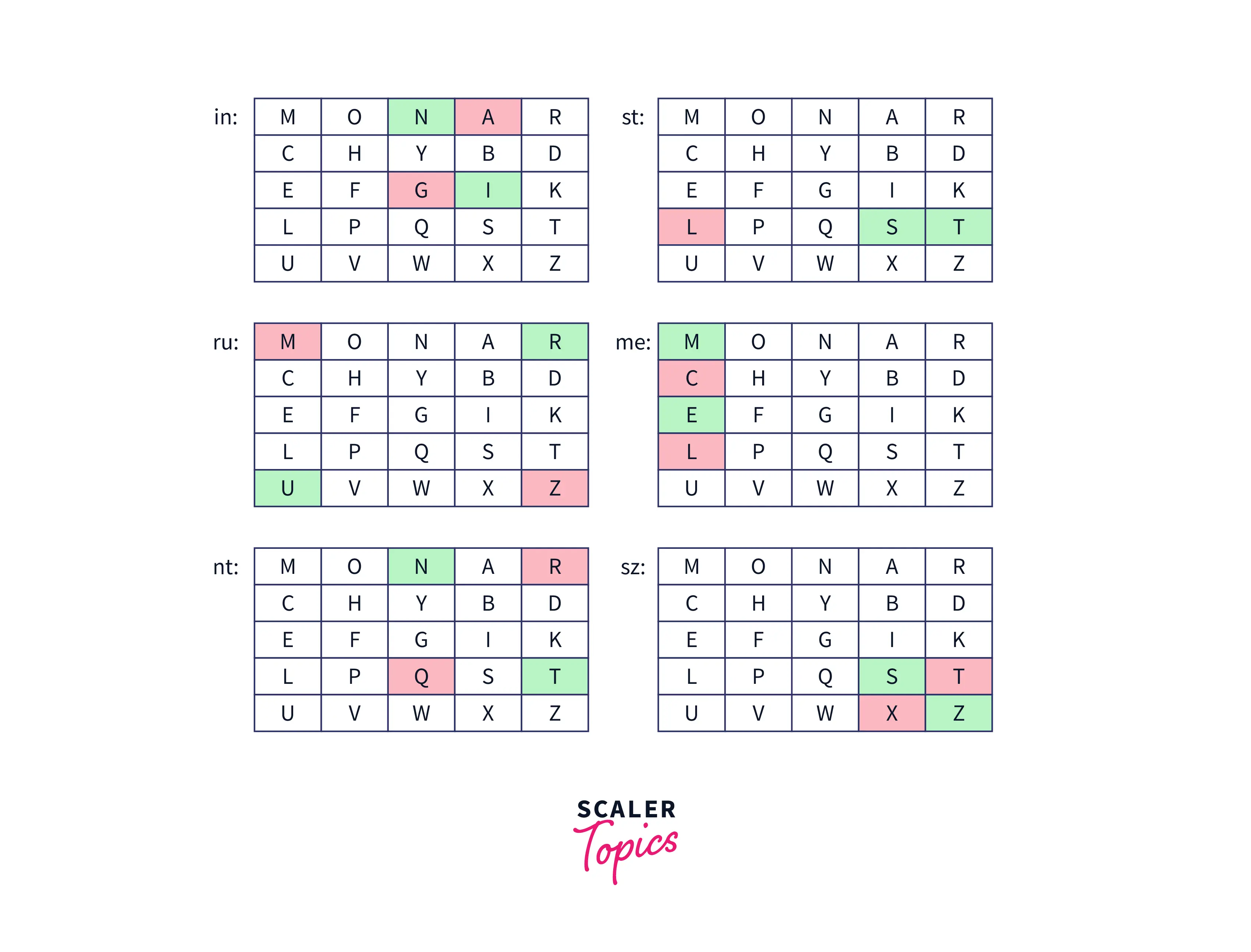
- After the split of the plain text into pairs, if all the letters of a digraph are in the same column, then we should take the letter just below the letters of the pair. Suppose the digraph is "me" then according to the rules, the encrypted text will be "cl.
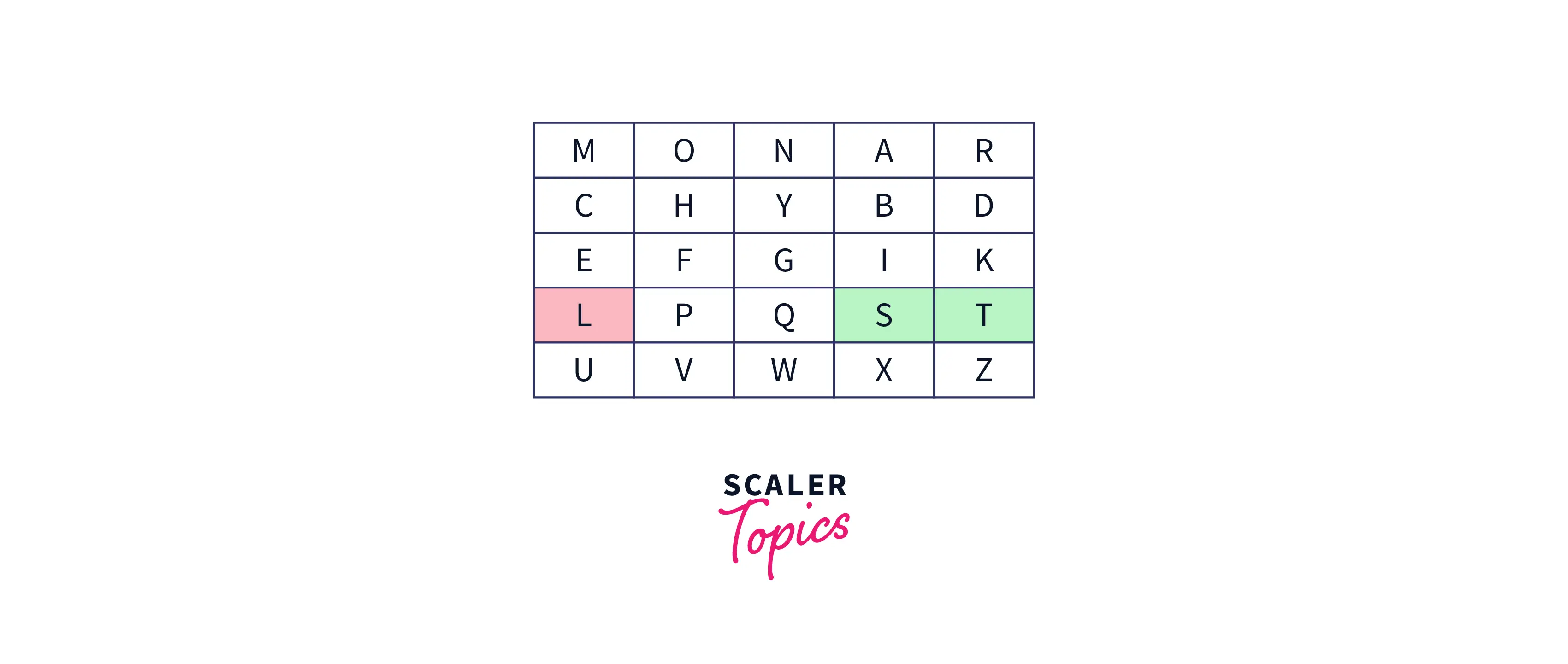
- After the split of the plain text into pairs of letters, if all the letters of a digraph are in the same row, then we should take the letter that is right to the letter of the pair. Suppose the digraph is "st" then according to the rules, the encrypted text will be "tl.
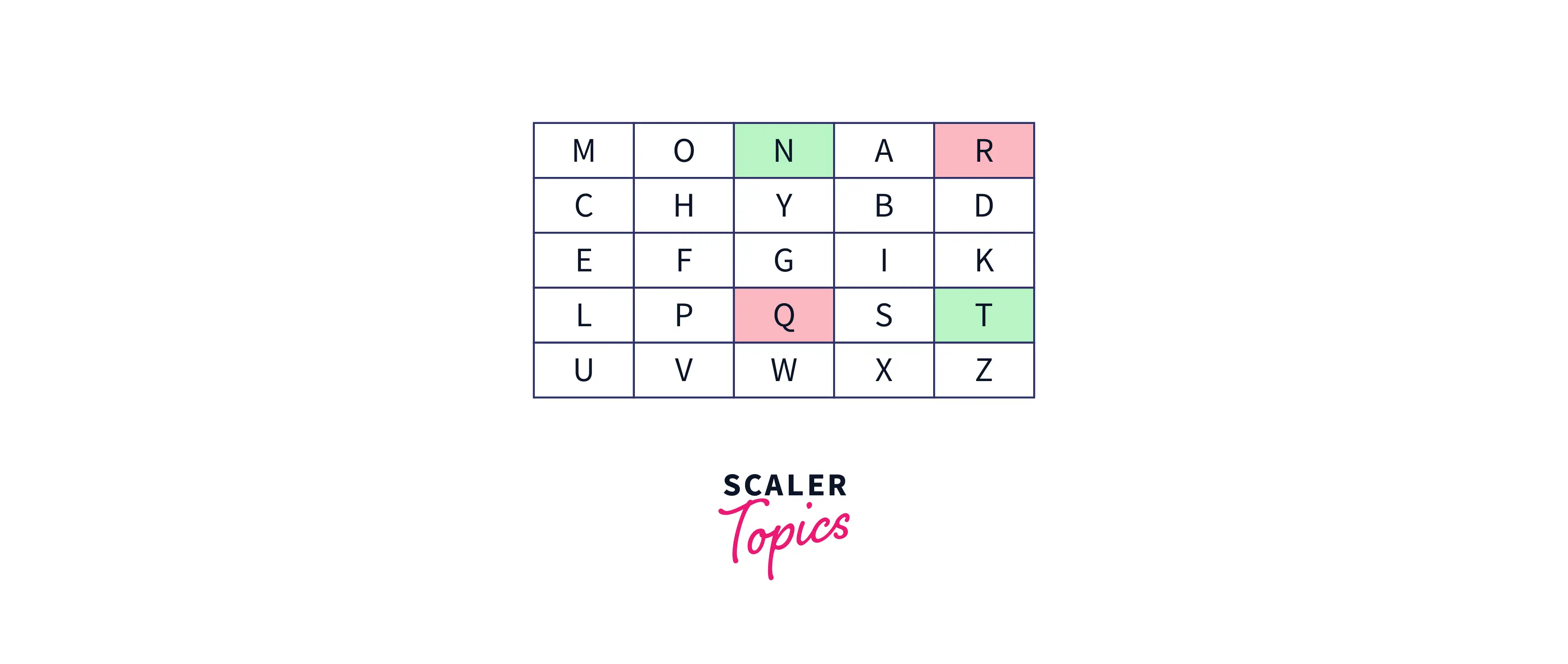
- If both the above conditions are not true, then just draw an imaginary rectangle by taking the positions of these two letters as diagonal of rectangle and then swap the letters with another diagonal letters. Suppose the digraph is "nt" then according to the rules, the encrypted text will be "rq.
Suppose we have "Instrument" as plain text and "Monarchy" as key. Using the above rules of encryption, the encrypted result of "Instrument" with the key "Monarchy" will be "gatlmzclrqtx".
Implementation of Playfair Cipher in C
Let us see how playfair cipher program in c language implemented using an example.
Output:
The above code will encrypt the plain text to cipher text using the Playfair cipher technique. First, we call encryptByPlayfairCipher() which removes space, converts plain text to lowercase, makes the plain text of even length, and then generates a square grid using generateKeyTable(). Then using that square grid encrypt() will encode the plain text to cipher text.
Decryption Technique
For decrypting the messages all the processes are done the same as encryption but in reverse order. As we know this is a symmetrical encryption technique, so the key will be the same for encryption and decryption. The decryption is done at the receiver's side.
The Playfair Cipher Decryption Algorithm
Again the decryption will be done in the following two algorithms:
-
Generate the key Square(5×5) at the Receiver’s End: The square will be of order 5*5 in which the letters of a key are entered one by one. All the alphabet present inside the text box should be unique. Since there are 26 letters in the alphabet, and the square has only 25 grid so the letters "J" is generally removed from the box. If the letter "J" is present in the cipher text then "J' is replaced with "I" in the square box. Initially, all the unique letters from left to right of the key are filled in the boxes. After that, all the remaining letters of the alphabet are filled in order of appearing.
-
Algorithm to Decrypt the Ciphertext The ciphertext is split into two letters known as "Digraphs". The number of characters of a ciphertext is always even. After that, the key-matric is traversed by pair, and the corresponding encipher is searched for that particular pair.
Example: Ciphertext = "gatlmzclrqtx" When it is split into pairs = 'ga' 'tl' 'mz' 'cl' 'rq' 'tx'
Rules for Decryption
There are some rules for decrypting cipher text in "playfair cipher program in c", which are as follows:
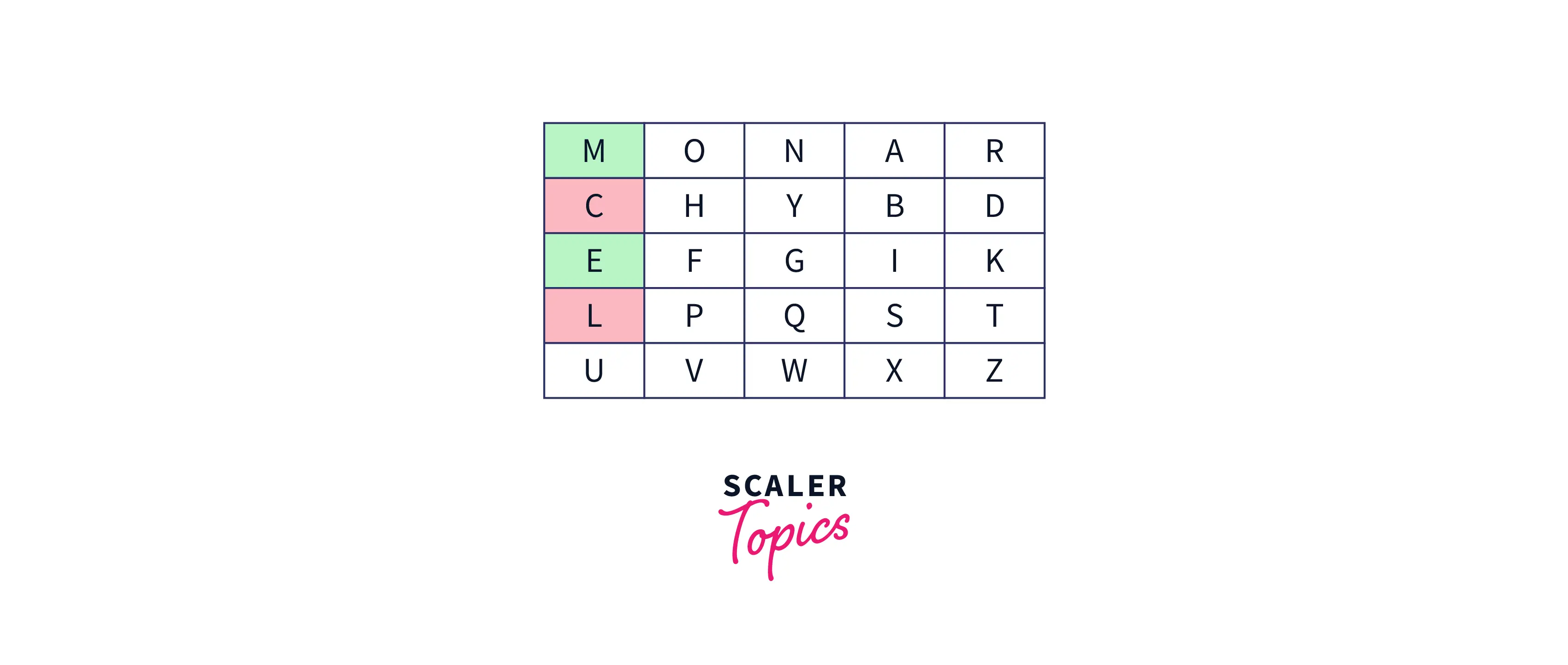
- If both the letters of the digraph are in the same column, then the letter above each letter will be taken. Example: Suppose the digraph is "cl", then, according to rules, the decrypted text will be "me".
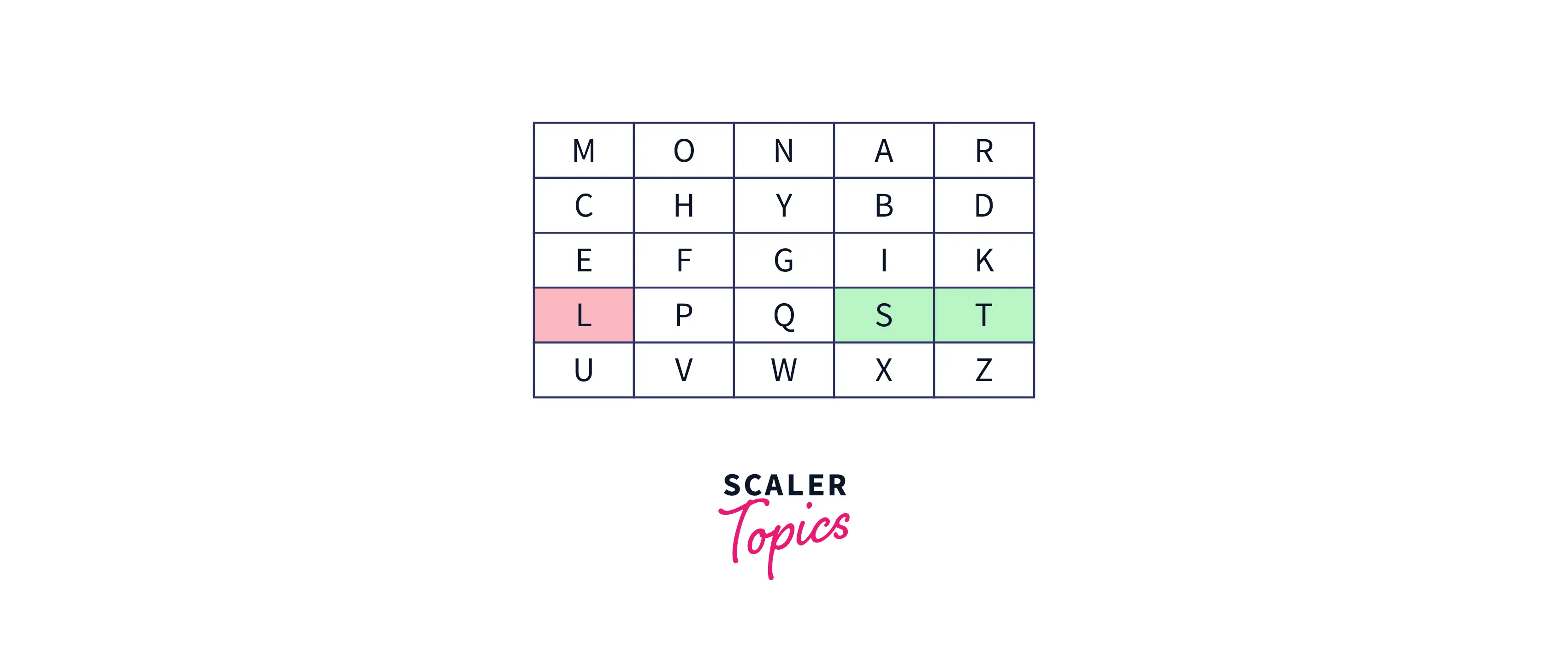
- If both the letters of the digraph are in the same row, then the letter that is left most to the row of the text of the digraph is taken. Example: Suppose the digraph is "tl" then the decrypted text will be "st".
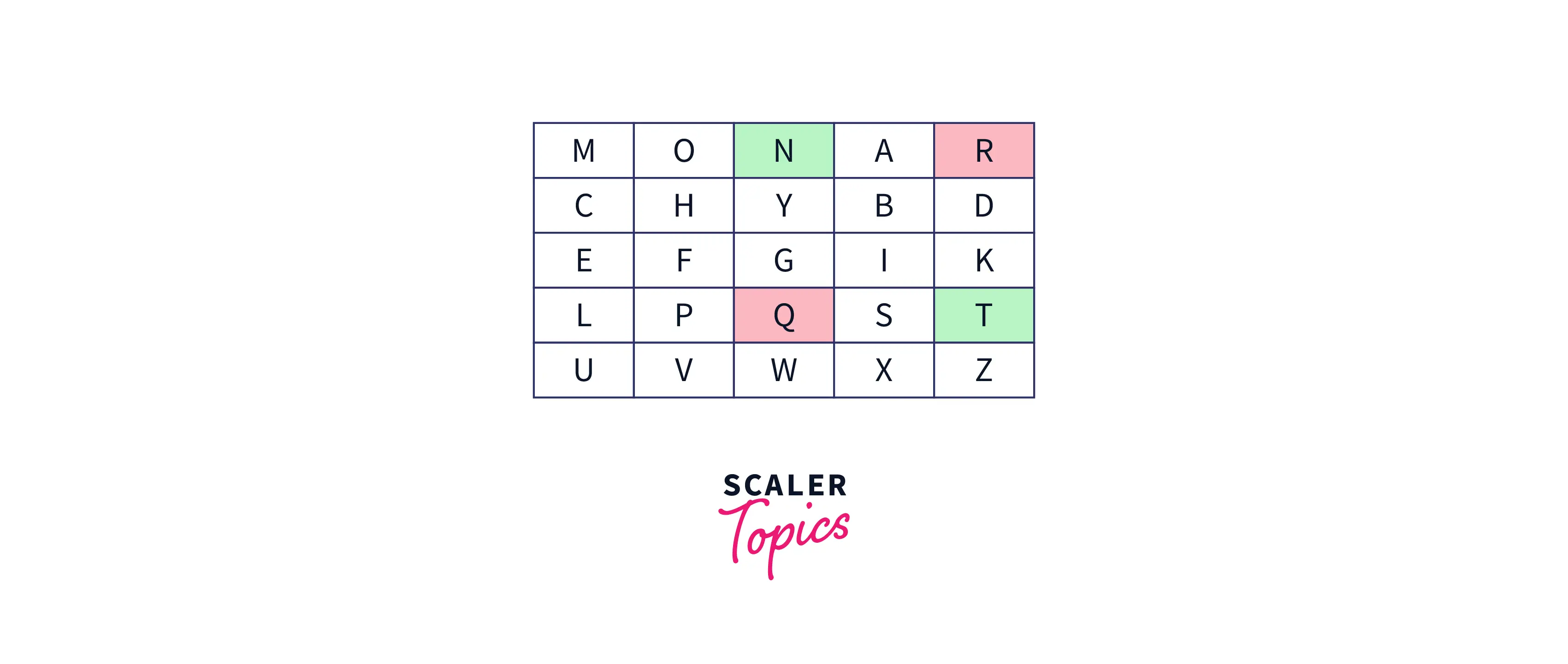
- If both the above conditions are not true, then a rectangle should be formed with the two letters as diagnol and then replace them with letters on the horizontal side and opposite to the corner of the rectangle. Example: Suppose the digraph is "rq" then the decrypted text will be "nt".
Implementation of Playfair Cipher Decryption in C
Let us see how playfair cipher is implemented in C language for decryption:
Output:
The above code will decrypt the cipher text to plain text using the Playfair cipher decryption technique. First, we call decryptByPlayfairCipher() which removes the space from cipher text and converts it to lowercase then call generateKeyTable() to generate a square grid. Then decrypt() will use that square grid to convert the cipher text to plain text.
Advantages and Disadvantages
Following are the advantages and disadvantages of the playfair cipher program in c.
Advantages of Playfair Cipher
- Since the digraph of the Playfair cipher consists of pair of letters in it, so the possibility of breaking the digraph is hard. The diagraphs can be of (25*25) =625 types, which is much larger than traditional monographs (25 diagraphs).
- In this technique, more pair of letters is needed to decode the encryption by 'Frequency Analysis'.
Disadvantages of Playfair Cipher
- In cipher text, suppose we have (XY) as a digraph so, its reverse will be (YX), both correspond to each other, which can be easily break-down by using frequency analysis. By doing this, the language of plain text could be known which makes this technique easy to decode.
- In Playfair cipher encryption, both the encryption key and decryption key are the same.
Conclusion
- Playfair cipher program in c is a symmetrical encryption technique used to encrypt and decrypt a message.
- Playfair cipher technique was invented by Charles Wheatstone in 1884, but its nomenclature was done by another person named 'Lord Playfair' who promoted this technique extensively and make this technique popular.
- This technique splits the message into pairs of texts and then encrypts them.
- The encryption consists of two steps that are generating the key square to make a cipher text, and then encryption of cipher text is done using the algorithm.
- All the letters inside the square should be unique and in order of appearing.
- The Decryption is also same as encryption, we just have to follow the same step in reverse order.
- This method was so efficient and popular that it was used by British forces during World War 1 and by the Australians during World War 2.
