How do a Port Scan in Linux?
Performing a port scan in Linux involves using specialized network scanning tools to check for open ports on a target system. Here is a step-by-step explanation of how to conduct scanning using a Linux port scanner:
- Install a Port Scanning Tool: The most common and powerful tool for port scanning in Linux is Nmap (Network Mapper). Ensure you have Nmap installed on your Linux system. If not installed, you can typically install it using your package manager.
- Identify the Target: Determine the IP address or hostname of the system you want to scan for open ports.
- Choose the Scan Type: Decide on the port scan type you want to perform. Some common scan types include TCP SYN scan, TCP Connect scan, UDP scan, and more.
- Execute the Port Scan Command: Open a terminal or command prompt on your Linux system and use the appropriate nmap command to perform the port scan.
- Analyze the Results: Once the scan is complete, Nmap will display the results showing the status of each scanned port (open, closed, or filtered). Analyze the results to identify any potential vulnerabilities or security issues.
- Consider Additional Scans: For a more comprehensive analysis, you can try other Nmap scan options, such as operating system detection (-O), service version detection (-sV), or script scanning (-sC).
Remember to use port scanner Linux tools responsibly and ethically. Ensure you have proper authorization before scanning any network or system that you do not own or manage. Unauthorized scanning is considered unethical and may have legal consequences.
What is TCP Scanning?
TCP scanning is used in computer networking and cybersecurity to identify open ports on a target system. Ports are communication endpoints that enable data to flow in and out of a computer or network device. Each port is associated with a specific service or application.
TCP (Transmission Control Protocol) is a core protocol of the Internet protocol suite and is responsible for establishing and maintaining reliable connections between devices. TCP scanning takes advantage of how TCP works to determine whether specific ports on a target system are open, closed, or filtered.
During a TCP scan, the scanning tool sends TCP packets to the target system's IP address and port number. The system behaviour in response to these packets helps the Linux port scanner tool infer the status of the ports. There are three common TCP scanning techniques:
- SYN Scanning (Half-Open Scanning): The scanning tool sends an SYN packet to the target's port and receives an SYN-ACK response if the port is open. It avoids completing the connection establishment, resulting in a stealthier approach compared to a full connection establishment's three-way handshake.
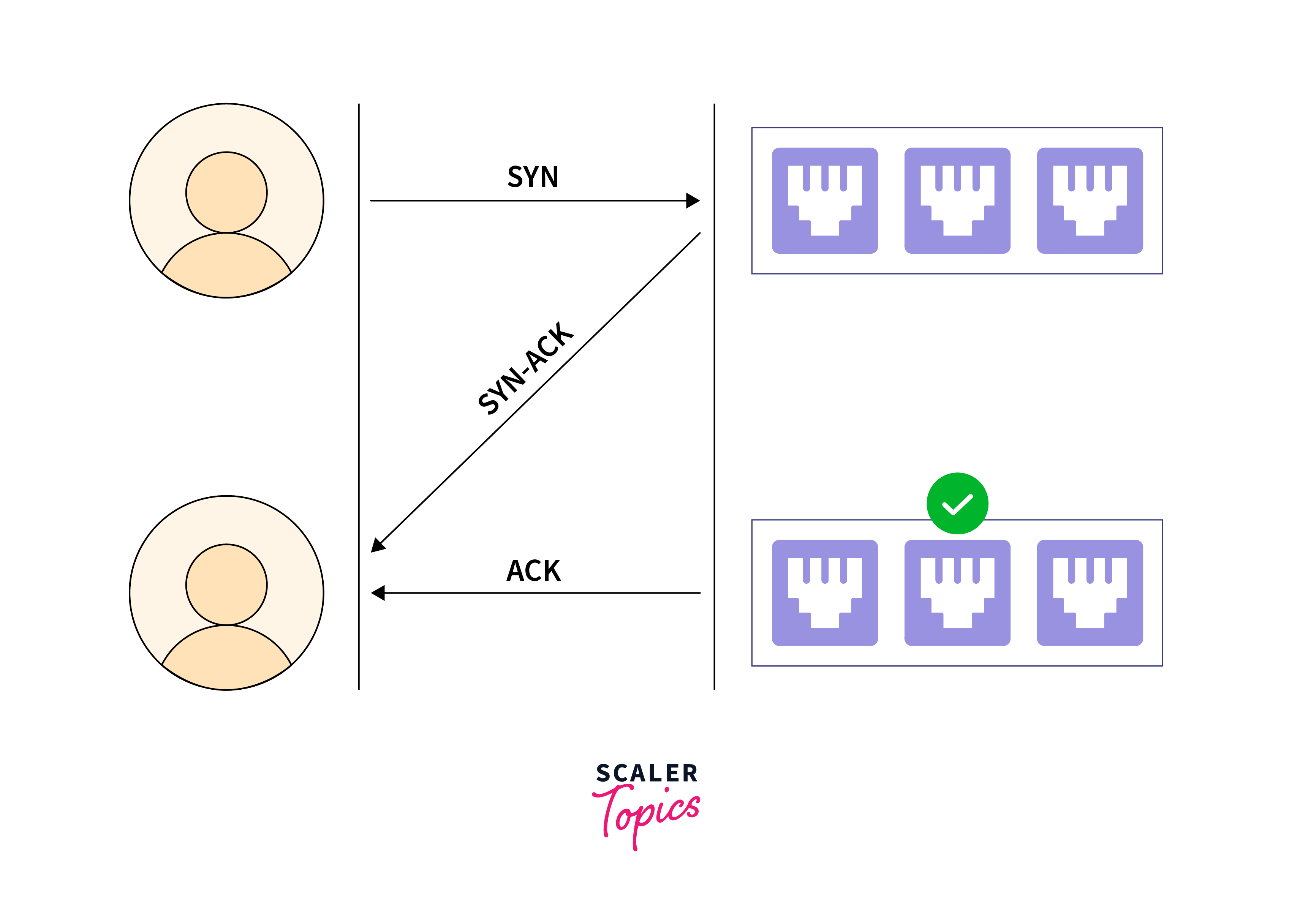
- TCP Connect Scanning: The scanning tool opens a full TCP connection to the target's port. If the port is open, the connection will be established, and the scanning tool will terminate it immediately. This method provides the most accurate results but is also the most easily detectable and traceable.
- FIN Scanning: This scanning tool sends a TCP FIN (finish) packet to the target's port. If the port is closed, the target will respond with an RST (reset) packet. If open, there will be no response. This technique relies on the behaviour of closed ports responding with an RST packet while open ports do not respond.
What is UDP Scanning?
UDP scanning is a network scanning technique used to identify open ports on a target system using the UDP (User Datagram Protocol) protocol. UDP is a connectionless transport protocol, which means it does not establish a connection before sending data. Instead, it sends packets directly to the target without any handshake or acknowledgement.
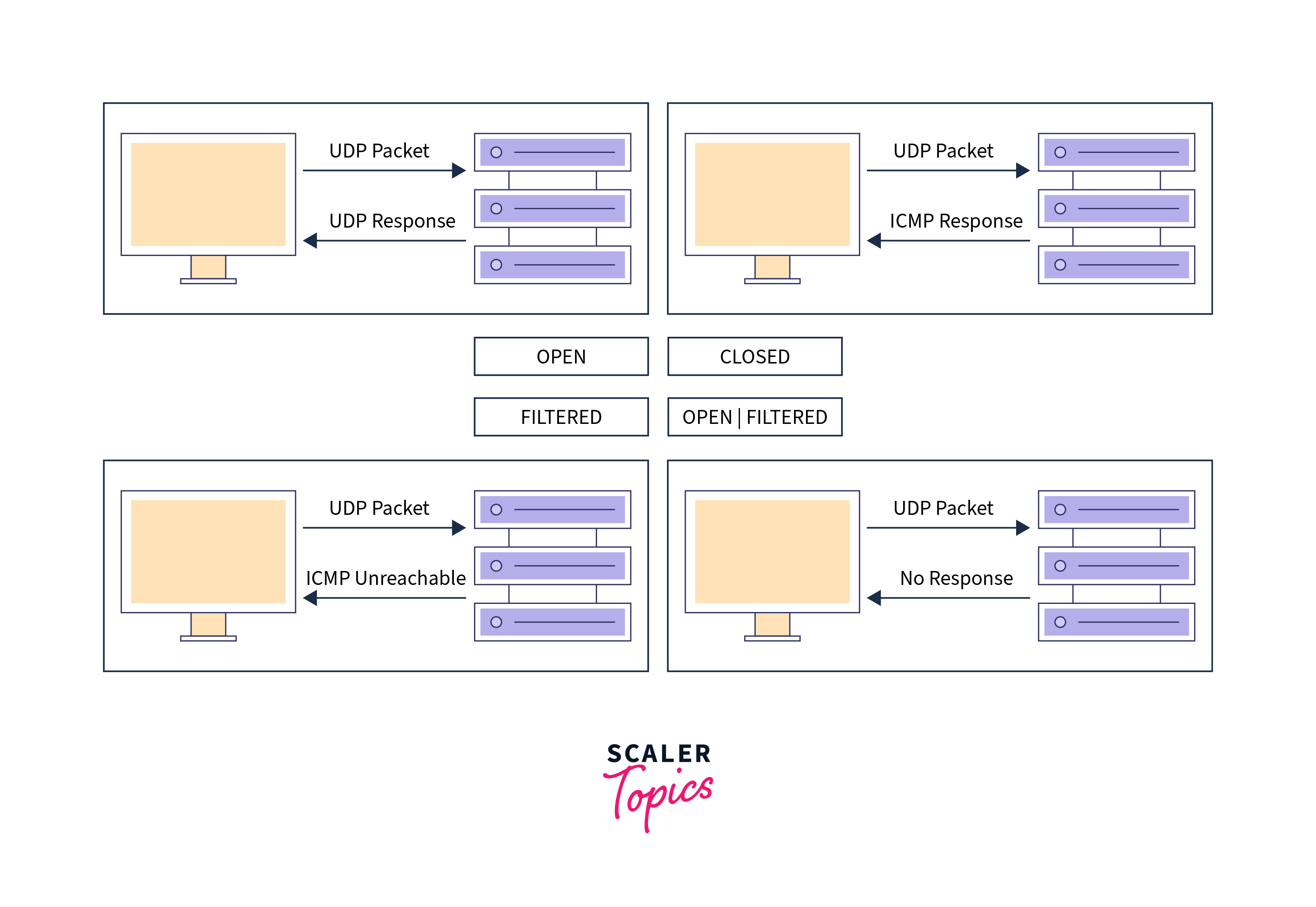
In UDP scanning, the scanning tool sends UDP packets to specific port numbers on the target system. The scanner uses the response of the target system to these packets to deduce the status of the ports. UDP scanning is trickier than TCP scanning because open UDP ports may not always respond, making it difficult to determine their status definitively.
If the target system responds with an ICMP (Internet Control Message Protocol) packet, typically an "ICMP port unreachable" message, it indicates the port is closed. On the other hand, if the target system does not respond, it suggests that the port may be open or filtered by a firewall.
Linux Port Scanner
Several powerful port scanning tools are available for Linux systems that network administrators and security professionals often rely on to assess network security and identify potential vulnerabilities. Let's take a closer look at some of these tools:
Nmap:
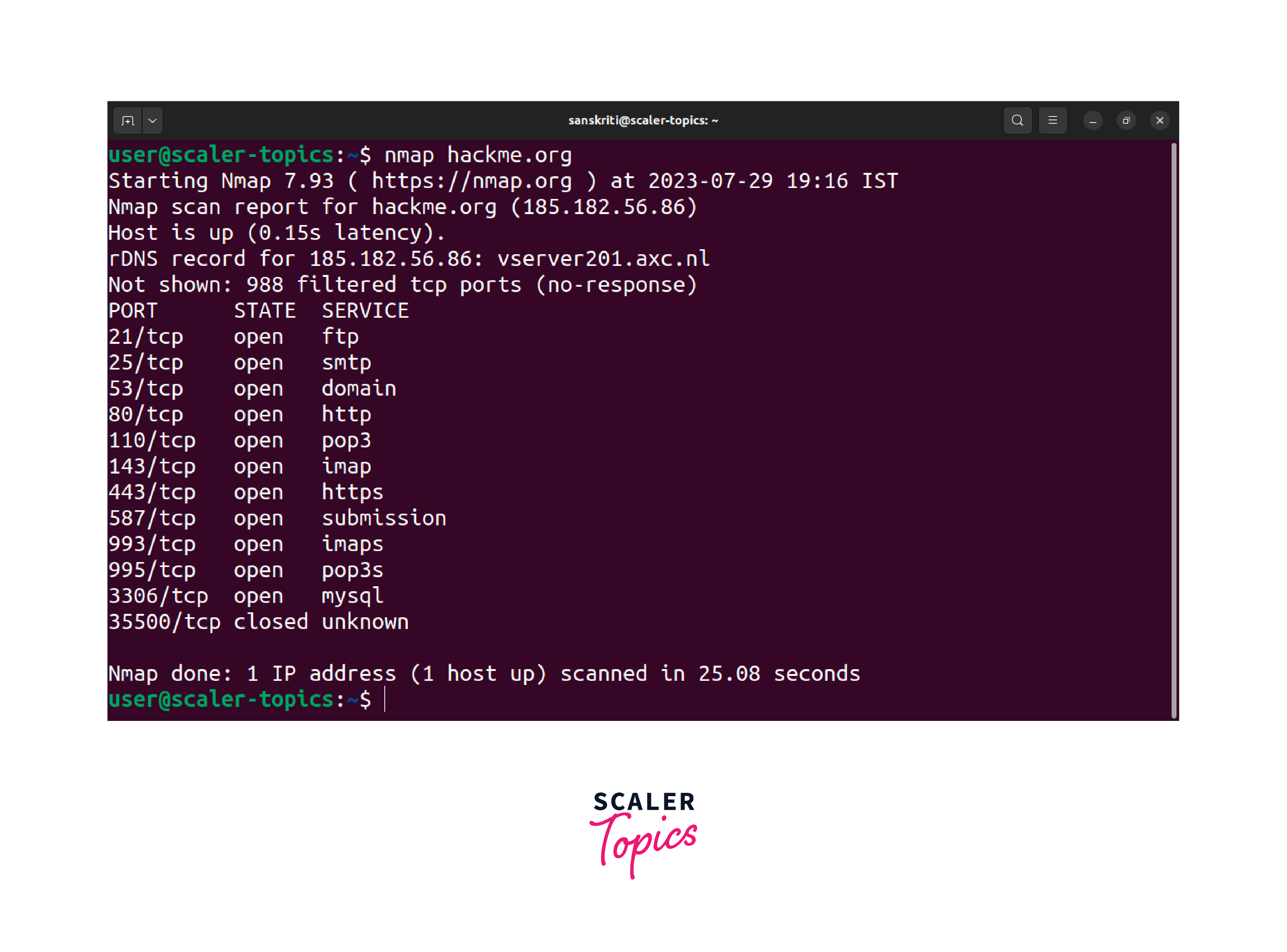
Nmap, short for Network Mapper, is one of the most popular and versatile port scanner Linux tools. It allows users to perform various types of scans, including TCP SYN scans, TCP connect scans, and much more. Nmap is known for its efficiency and ability to scan large networks. Here's an example of a TCP SYN scan using Nmap:
When you execute this command, Nmap will use a TCP SYN scan (also known as half-open scanning) as the default scan type to identify open ports and services on the target domain hackme.org.
Zenmap:
Zenmap is a graphical user interface (GUI) for Nmap, providing a user-friendly way to interact with Nmap's features. It allows users to visualize scan results and navigate the data more easily. Here's an example of using Zenmap for a quick scan:
The command runs Zenmap with aggressive timing and a fast scan mode on the target IP address 10.0.0.1, prioritizing common ports for quicker results.
Netcap:
Netcap is another powerful command-line network analysis tool that includes Linux port scanner capabilities. It allows users to capture and analyze network packets, making it useful for more detailed analysis. Here's an example of Netcap:
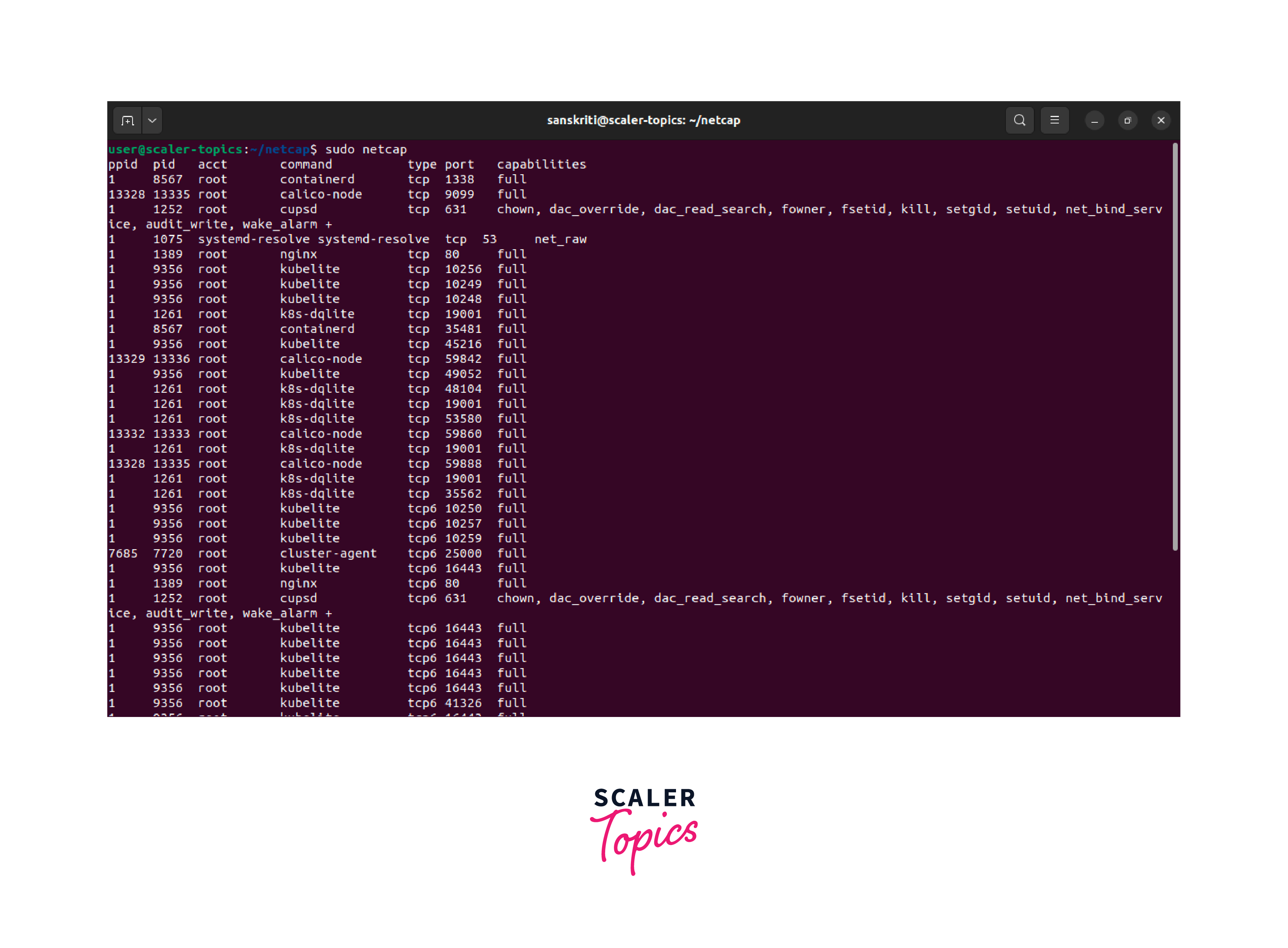
The command displays packet details like source/destination IPs, ports, and protocols on the terminal. This helps with network troubleshooting, security analysis, and monitoring network activities.
Unicornscan:
Designed for reliability and efficiency in large-scale network scanning, Unicornscan is a fast and lightweight Linux port scanner that uses asynchronous transmission to achieve high-speed scanning. Here's an example of a simple scan using Unicornscan:
The command executes the unicornscan tool to perform a port scan on the IP address 192.168.2.50, specifically targeting all ports on the system (port range from 1 to 65535). The tool will attempt to identify the status of each scanned port (open, closed, or filtered) on the target system.
Conclusion
In conclusion, port scanner Linux helps security professionals to assess the security posture of their systems and identify potential vulnerabilities. Here are the key takeaways from the article:
- Port scanning in Linux involves using network scanning tools like Nmap, Zenmap, Netcap, and Unicornscan to identify open ports on a target system.
- TCP scanning utilizes techniques, such as SYN scanning, TCP Connect scanning, and FIN scanning, to determine the status of ports on a target system.
- UDP scanning is employed to identify open ports using the UDP protocol, though it can be more challenging due to the lack of reliable responses.
- Perform network scanning responsibly with proper authorization; unauthorized scanning is unethical and may have legal consequences.
