Scala Security
Overview
Security is an ongoing concern in software development, and Scala developers must prioritize it at every stage of the application lifecycle. By following best practices for secure development, implementing robust security measures, and staying informed about emerging threats, we can build Scala applications that are resilient in the face of security challenges.
Introduction
Scala, a potent language fusing object-oriented and functional paradigms, excels in secure, scalable app development. Yet, it's not impervious to security risks common to all languages. Neglecting security can expose Scala apps to data breaches, system failures, and unwelcome consequences. To ensure the security of our Scala applications, we should be aware of potential risks and follow best practices throughout the development lifecycle.
What are the Security Issues in Scala and What are Their Solutions?
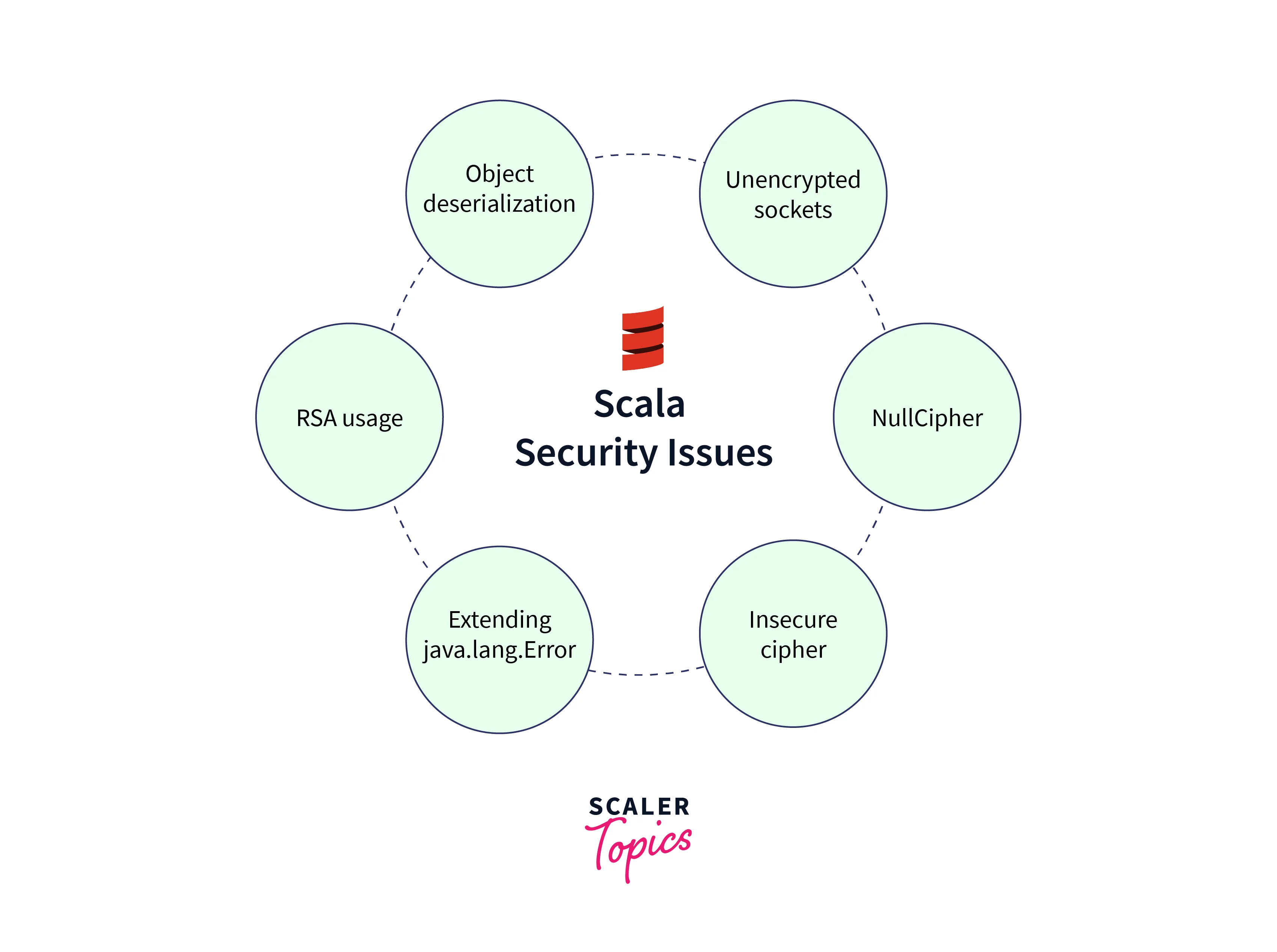
Avoid Object Deserialization of Untrusted Data
Object deserialization refers to converting serialized data to objects which is powerful but risky in Scala and other languages, especially with untrusted data.
The primary security concern with object deserialization is that it can lead to arbitrary code execution or other forms of malicious activity if not handled carefully.
Common Risks and Consequences:
Object deserialization of untrusted data can lead to code execution and unauthorized system actions, while also risking data exposure. Additionally, malicious deserialization can trigger resource consumption attacks, disrupting services and causing denial of service incidents.
Solution:
- Whitelisting: Maintain a whitelist of allowed classes that can be deserialized, and only deserialize objects of these classes. Scala provides libraries like Java's ObjectInputStream and ObjectOutputStream, which can be customized to use a custom ClassLoader to enforce this restriction.
- Use Serialization Filters: Consider using serialization filters provided by libraries like Apache Commons IO. These filters allow you to specify which classes are permitted during deserialization and block any attempts to deserialize unapproved classes.
- External Data Sources: If you must deserialize data from external sources, consider alternatives such as JSON or XML serialization, which are less prone to security risks. Libraries like Jackson or Circe can help your work with these formats in Scala.
Avoid Using the NullCipher
The "NullCipher" is a class provided in the Java Cryptography Extension (JCE) that essentially provides no encryption or decryption. It is a placeholder or stub class that is sometimes used by developers, often inadvertently, when encryption or decryption is not required.
Common Risks and Consequences:
NullCipher poses significant risks: it lacks encryption, leaving data vulnerable, and can mislead developers into thinking data is secure when it's not and non-compliance with encryption standards.
Solution:
- Choose Strong Algorithms: When working with encryption in Scala, use secure encryption algorithms like AES (Advanced Encryption Standard) or RSA (Rivest–Shamir–Adleman). These algorithms provide robust encryption capabilities.
- Proper Key Management: Ensure that encryption keys are generated, stored, and managed securely. Utilize key management best practices to protect your keys from unauthorized access.
- Review Code: Conduct code reviews to identify and replace instances of NullCipher with proper encryption algorithms in your Scala codebase.
Enforce Secure RSA Usage — RSA Algorithm Must Have Padding Set.
The RSA (Rivest-Shamir-Adleman) encryption algorithm is widely used for secure data encryption and digital signatures. However, to ensure the security of RSA encryption, it's crucial to use appropriate padding schemes. Padding adds randomization and security to the encryption process, making it more resistant to attacks.
Common Risks and Consequences:
Using RSA without proper padding introduces significant risks, including susceptibility to padding attacks that can compromise data security, and potential data integrity issues due to incorrect padding, leading to data mismatches and potential data corruption or unexpected behavior. Proper padding is crucial for RSA's security and data integrity.
Solution:
- Padding Schemes: Always use secure padding schemes with RSA, such as PKCS#1 v1.5 or OAEP (Optimal Asymmetric Encryption Padding), which add randomization and security to the encryption process.
- Library Support: When working with RSA in Scala, use cryptography libraries like Bouncy Castle or the Java Cryptography Extension (JCE), which provide built-in support for secure RSA encryption and decryption.
- Keep Libraries Updated: Ensure that you are using the latest versions of cryptography libraries to benefit from security updates and improvements.
- Regular Auditing: Periodically audit your codebase to confirm that RSA usage adheres to best practices and that proper padding is consistently applied.
IndexOf Checks Should be for Negative Numbers
When using the indexOf method in Scala, it's essential to account for the possibility of negative index values. The indexOf method is typically used to find the position of a specific element or substring within a collection or string. While it returns -1 when the element is not found, it can also return negative values when counting backward from the end of the collection. This behavior is crucial to consider, especially when writing code that relies on the result of indexOf.
Common Risks and Consequences:
The common risks of using indexOf include off-by-one errors and incorrect logic due to neglecting negative indices, leading to unexpected behavior or incorrect results. It can also result in index out-of-bounds errors if indices are manipulated without considering their signs, causing runtime issues.
Solution:
- Check for Negative Indices: Before using indexOf, validate the input index. Ensure it is within the valid range, which includes both positive and negative indices.
- Use a Safe Default: If you want to find the last occurrence of an element, consider using lastIndexOf or similar methods, which inherently handle negative indices appropriately.
- Error Handling: Implement error handling or validation logic to gracefully handle cases where the index is out of bounds or negative.
IndexOf Checks Should Use a Start Position
When using the indexOf method in Scala, it's essential to provide a start position as part of your search parameters. The indexOf method is typically used to find the position of a specific element or substring within a collection or string. By specifying a start position, you can control the search scope and avoid unintended results.
Common Risks and Consequences:
Using indexOf without specifying a start position can lead to inefficient searches, especially for multiple occurrences, and may yield incorrect results when searching from specific positions. Specifying a start position in large collections significantly improves performance.
Solution:
- Specify Start Position: Always provide a start position when using indexOf to indicate where the search should begin. This can significantly improve performance, especially when searching for multiple occurrences.
- Looping: If you need to find all occurrences, use a loop with the indexOf method, updating the start position in each iteration to find subsequent matches.
- Consider Regex: For more complex pattern matching, consider using regular expressions (Regex in Scala) to control the search criteria and position.
java.lang.Error Should not be Extended
In Java and Scala, extending the java.lang.Error class for custom exception handling is generally discouraged and considered a bad practice. The java.lang.Error class is typically reserved for serious and unrecoverable issues that are beyond the control of the application and often indicate critical errors at the JVM level. These errors usually lead to the termination of the application or, in some cases, the virtual machine itself.
Common Risks and Consequences:
Using java.lang.Error for custom exceptions can lead to unintended application termination and misleading semantics, as it may not accurately represent the error severity. This approach can also result in inflexible error handling, favoring abrupt termination rather than controlled recovery, which can be problematic for application stability and maintainability.
Solution:
- Use Exceptions: Instead of extending Error, create custom exception classes that extend java.lang.Exception or its subclasses (e.g., RuntimeException). This allows you to handle application-specific errors more appropriately.
- Clear Hierarchy: Design a clear exception hierarchy in your Scala codebase to categorize and handle different types of errors effectively. This makes it easier to catch and respond to specific exceptions.
- Documentation: Document your custom exceptions and their intended use cases, providing meaningful descriptions to help developers understand when and how to handle them.
Prevent Path Traversal
Path traversal attacks, also known as directory traversal attacks or directory climbing attacks, are security vulnerabilities that occur when an attacker manipulates file paths to gain unauthorized access to files and directories outside the intended scope. This is a critical security concern, especially when handling file and directory operations in Scala or any other programming language.
Common Risks and Consequences:
Path traversal risks include unauthorized access to sensitive files and data exfiltration, potentially causing data breaches or tampering. In severe cases, it can lead to system compromise, enabling the execution of arbitrary code and jeopardizing the entire system's security.
Solution:
- Input Validation: Always validate and sanitize user-provided input, such as file paths, to ensure it doesn't contain sequences like "../" that could navigate outside the intended directory.
- Whitelisting: Implement a whitelist of allowed file paths and only permit access to files within those directories.
- Use Framework Features: When working with web applications, utilize security features provided by your web framework, like route handlers or libraries, to securely handle file operations.
Prohibit Insecure Ciphers
Insecure ciphers are encryption algorithms that have known vulnerabilities or weaknesses, making them susceptible to various cryptographic attacks. Using insecure ciphers in your Scala applications can compromise the security of sensitive data and communications. It is crucial to avoid and prohibit the use of such ciphers to maintain the confidentiality and integrity of your data.
Common Risks and Consequences:
Insecure ciphers pose significant risks, including data exposure and susceptibility to cryptographic attacks, which can compromise data security. Non-compliance with encryption standards mandated by regulations like GDPR and HIPAA can result in legal consequences, making the use of secure ciphers imperative.
Solution:
- Cipher Selection: Always select strong encryption ciphers, such as AES (Advanced Encryption Standard), for data encryption. Avoid older and insecure ciphers like DES (Data Encryption Standard).
- Cipher Configuration: Ensure that the chosen ciphers are configured with secure settings, including appropriate key lengths and modes of operation.
- Regular Updates: Stay informed about cryptographic best practices and vulnerabilities. Periodically review and update your cipher configurations to meet current security standards.
Prohibit Unencrypted Sockets
Unencrypted sockets, also known as plaintext or cleartext communication, involve transmitting data over a network without encryption. This practice poses a significant security risk, as sensitive information can be intercepted and viewed by unauthorized parties during transmission. To protect the confidentiality and integrity of data exchanged over network connections, it is essential to prohibit unencrypted sockets in Scala applications.
Common Risks and Consequences:
Unencrypted sockets are vulnerable to data interception and tampering, putting sensitive information at risk during network transmission. Failure to implement encryption may also result in non-compliance with data protection regulations, potentially leading to legal consequences.
Solution:
- Use TLS/SSL: When transmitting data over networks, use Transport Layer Security (TLS) or its predecessor, Secure Sockets Layer (SSL), to encrypt the communication. These protocols provide encryption and authentication to secure data in transit.
- Enforce Encryption: Configure your network services and protocols to enforce encryption, ensuring that all data transmitted over the network is encrypted by default.
- Certificate Management: Properly manage SSL/TLS certificates, including certificate validation, renewal, and protection of private keys.
- Security Headers: For web applications, consider using security headers like HTTP Strict Transport Security (HSTS) to enforce secure connections over HTTPS.
Conclusion
- Preventing path traversal, avoiding insecure ciphers, and prohibiting unencrypted sockets are essential security measures that should be incorporated into every Scala application. These practices protect against common vulnerabilities and threats.
- Enforcing secure RSA usage with proper padding, avoiding the NullCipher, and choosing strong encryption ciphers are vital for protecting sensitive data and communications.
- Extending java.lang.Error for custom exception handling is discouraged. We should create well-structured custom exception classes to handle various error scenarios.
- We should adopt safe coding habits, such as validating input data, specifying start positions for index checks, and documenting code thoroughly.
