What is Security Testing?
Overview
Security testing of software aims to find all vulnerabilities, threats, and attacks on the product that could result in the loss of confidential information. Security testing identifies loopholes and weaknesses a system possesses.
What is Security Testing?
Security testing is a type of software testing where testers find possible scenarios where there could be any information leak.
It ensures the application is secured and doesn't have any loopholes or vulnerabilities. Security testing is the utmost priority of every company, as loss of information could put the company into legal trouble.
Goal of Security Testing
- The primary goal of security testing is to identify vulnerabilities within a system or application.
- Security testing aims to assess the level of risk associated with identified vulnerabilities.
- It involves testing the effectiveness of security controls and measures implemented within a system.
- Security testing helps validate compliance with industry regulations, standards, and best practices.
- The goal is to evaluate the incident response capabilities of an organization.
- Security testing contributes to enhancing overall security awareness within the organization.
- Ultimately, the goal of security testing is to safeguard the organization's reputation and trust.
Principle of Security Testing
- Confidentiality: The data must remain secured and password encrypted.
- Integrity: The user's privacy of data and information must not be misused.
- Authentication: The secure authentication system where the user gets a safe gateway to the application.
- Authorization: Only the user with authorization for certain application sections should get it. For example, Admin must have access to all the information in the system except the user's password.
- Availability: The system must remain secured at all times.
- Non-repudiation: System must not refused the authorized user's access to the system.
Key Areas in Security Testing
- Network Security:Data transfer between UI and API is ensured to be encrypted and secured.
- System Software Security: The entire application, UI, server, and database must be secured.
- Client-side Application Security: The data sent by the user to server under HTTPS must be secured.
- Server-side Application Security: The interaction between the database and receiving data from the database and the client has to be secured.
Types of Security Testing
- Vulnerability Scanning involves using automated software to examine a system and identify known patterns of vulnerabilities.
- Security Scanning involves identifying weaknesses in network and system security, followed by proposing solutions to mitigate these risks.
- Security Auditing is an internal inspection of applications and operating systems to identify security flaws. It may involve a line-by-line examination of code.
- Penetration Testing mimics a malicious hacker's attack on a specific system to uncover potential vulnerabilities. It involves analyzing the system for vulnerabilities while attempting to breach it.
- Risk Assessment involves analyzing security risks within an organization and categorizing them as low, medium, or high. This testing helps establish controls and measures to minimize these risks.
- Network Security Testing focuses on identifying vulnerabilities within the network infrastructure, such as firewalls, routers, and other network devices.
- Ethical Hacking differs from malicious hacking as its purpose is to expose security flaws in an organization's system.
- Application Security Testing focuses on identifying vulnerabilities within the application itself, including its code, configuration, and dependencies.
- Social Engineering Testing simulates social engineering attacks, such as phishing or baiting, to identify vulnerabilities in the system's human element.
- Posture Assessment combines security scanning, ethical hacking, and risk assessments to provide an overall evaluation of the system's security posture.
- Tools like Nessus, OpenVAS, and Metasploit can automate and streamline the security testing process.
How to do Security Testing?
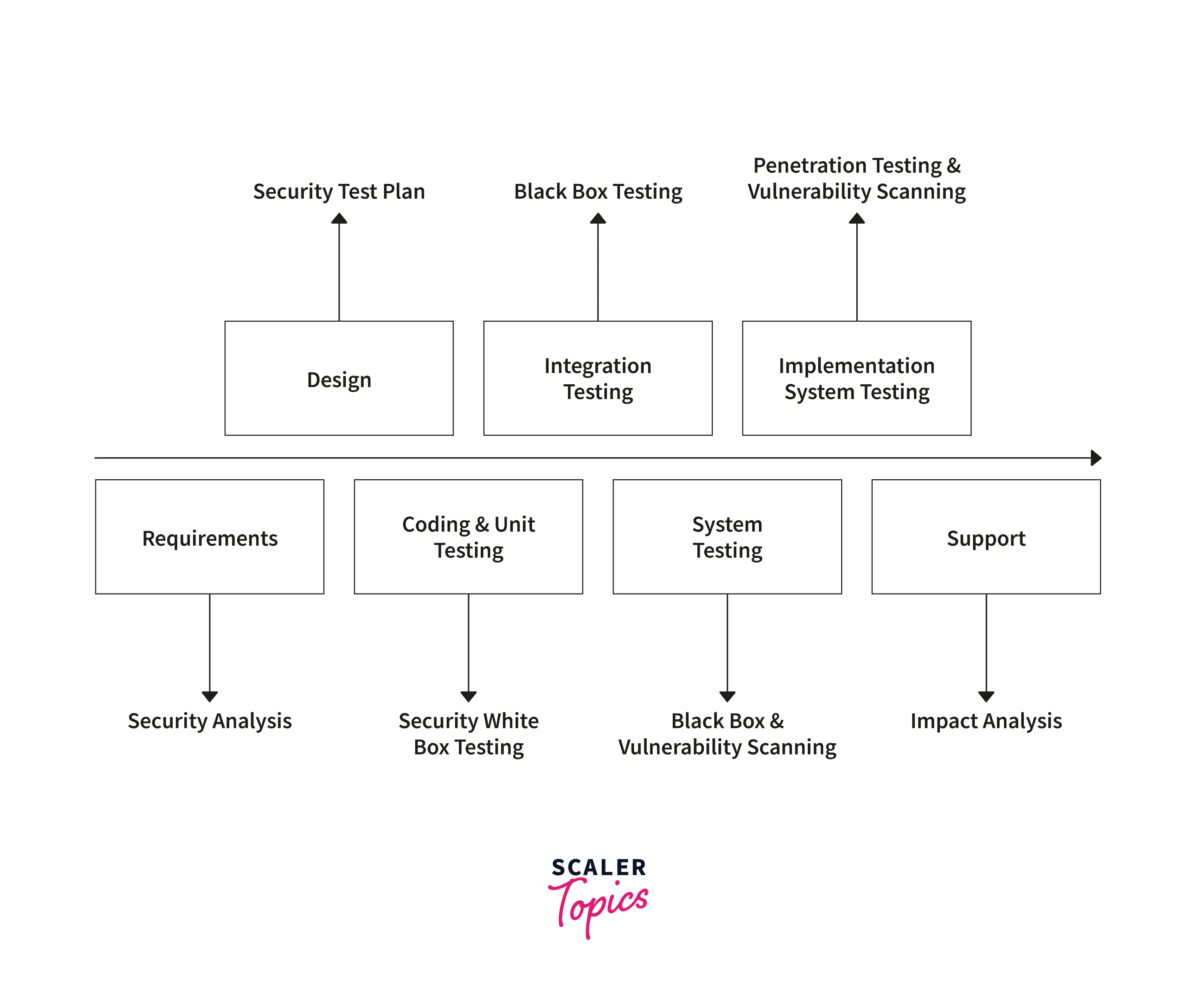
- Security Testing at Requirement Gathering phase: At this phase, the information about use cases and the list of functional and non-functional requirements are kept secured to not leaks to competitors.
- Security Testing at System Design Phase:At this phase, design the areas where security testing needs to be implemented. For instance, UI, API, Message pass, Database, and servers like EC2 are identified.
- Security Testing at Development Phase: The software performs unit and integration testing for vulnerabilities and attacks. System testing for any loopholes.
- Security Testing at Testing Phase: Every module performs a security checkup for any vulnerability.
- Security Testing at Maintenance Phase: Through bug bounty and third-party vendors, the system goes through continuous penetration and vulnerability testing.
Example Test Scenarios for Security Testing
- Password stored must be encrypted in the database.
- Penetration testing like SQL injection must be tested
- Data transfer from UI to API must also be encrypted.
- Sessions and Cookies must be tested for security.
Techniques for Security Testing
1. Tiger Box: Tiger Box Testing is done by a system with security testing tools to check vulnerabilities and defects in the system. 2. Black Box: Black box testing in security is done on the network topology. 3. Grey Box: Grey box is a combination of both tiger box and black box as tools are used here, and network topology is also tested.
Why Security Testing is Essential for Web Applications?
Security testing is vital for web applications due to several reasons.
- Web applications are often exposed to a wide range of potential threats and vulnerabilities. Hackers and malicious actors are constantly seeking opportunities to exploit weaknesses in web applications to gain unauthorized access, steal sensitive data, or disrupt services.
- Secondly, web applications often handle sensitive user information, such as personal data, financial details, or login credentials. If these applications are not adequately secured, they can become targets for data breaches, leading to severe consequences for both users and the organization responsible for the application.
- Web applications often interact with various components and external systems, such as databases, APIs, and third-party services. These interactions introduce additional security risks, as vulnerabilities in these components can be exploited to compromise the overall security of the web application.
- Security testing helps organizations comply with industry regulations and standards. Many sectors, such as finance, healthcare, and e-commerce, have specific security requirements that web applications must meet.
- Security testing helps improve the overall quality and reliability of web applications by identifying and fixing vulnerabilities, thus reducing the risk of service interruptions or downtime.
Myths and Facts of Security Testing
| Myths | Facts |
|---|---|
| Security testing is needed where payment gateway integration is there. | Security testing is needed for system and network security |
| Security testing should be done in the end | Security testing is needed at every stage of product development |
| After Security testing application is 100% secure | There is never 100% security. The product is improved daily. |
| Security testing is needed only in large scaled products | Security Testing is needed from small to big products |
Security Testing Tool
1) Acunetix:cunetix is a web-only vulnerability testing software for websites that is integrable with GIT, Gitlab, Azure, and Jira. 2) Intruder: Intruder is a penetration testing tool that is used in cloud resources and API integration with CI/CD resources. It tests the vulnerabilities of the system. 3) Owasp:The Open Web Application Security Project (OWASP) is a non-profit organization for security testing. The organization has multiple tools and documentation for various system security resources. 4) WireShark:WireShark is a network protocol analyzer that checks for errors at the network level. It checks for packets, protocols, three-pane packet browsers, and VoIP analysis. 5) W3af:W3af stands for web application attack and audit framework. This tool checks for SQL Injection in the code and vulnerabilities identified by plugins written in python, where one sends HTTP requests to find errors.
Advantages and Disadvantages
Advantages of Security Testing
- Security testing helps identify vulnerabilities before they are exploited.
- It also strengthens overall system protection by addressing weaknesses and implementing necessary controls.
- It ensures compliance with regulations, standards, and best practices.
- Security testing protects sensitive data from unauthorized access or breaches.
- This also fosters customer trust and preserves an organization's reputation by demonstrating commitment to data security.
Disadvantages of Security Testing
- Security testing may provide incomplete results, leading to a false sense of security.
- It requires significant investment of time, money, and skilled resources.
- Sometimes rigorous security testing can temporarily disrupt normal business operations.
- Security testing may overlook certain areas or components, leaving potential vulnerabilities undetected.
- Security testing may struggle to keep up with rapidly evolving and sophisticated cyber threats.
Conclusion
- Security Testing is used to find the vulnerabilities and defects in a system.
- All the products, no matter their size, must be tested for security.
- Security Testing is widely used in web-based applications and APIs.
- Many software testing tools are available in the market, like W3af, WireShark, Intruder, etc.
