What Is Threat Modeling?

Overview
Threat modeling is a systematic approach to optimizing an application, system, or business process security by identifying potential threats and vulnerabilities. Threats can be internal as well as external, identifying them helps us allocate proper attention and resources to reduce future risks. Various methodologies and open-source tools are available to identify the threats.
What is Threat Modeling?
A cyber threat is an existing vulnerability that can be used by someone with a harmful intent to cause harm, steal data, or disrupt a computing system. Commonly known cyber security threats are Denial of Service, Injection Attacks, Man in the Middle Attacks, Malware, etc.
Threat Modeling, a core element in the security development lifecycle is an engineering technique to identify threats, countermeasures, vulnerabilities, and attacks. Threat modeling can be used to reduce risk, shape the application's design, and meet security requirements.
With technological advancements, it is very easy for hackers and externals to get access to sensitive details, and attack innocents. Growing use of Internet of Things(IoT) devices, mobile phones, cloud-based services, etc. threat modeling is becoming more and more necessary.
Threat modeling is a process of defining and structurally representing all the information and security of an application. It can be applied to a wide range of things such as software, applications, networks, Operating systems, distributed systems, IoT devices, and business processes.
Threat modeling must be included at the beginning of the development cycle of the software. It involves deconstructing the elements of a system or software to identify the important assets to be protected and the existing threats to be mitigated. A threat modeling procedure is a way to break down a complex process into mini tasks and spot weaknesses in it.
Why is Threat Modeling Necessary?
Any application software or system must be capable of withstanding attacks. Threats are not only external, sometimes they come from within knowingly or unknowingly.
Threats are present everywhere, whether it is a small enterprise or a large enterprise. Smaller enterprises are more prone to vulnerabilities as they don't take enough cybersecurity measures in place.
Attackers act and think differently than developers. A simple development process is not enough for identifying and resolving threats. A separate section should be added to reduce threats.
The project team must understand and identify the security controls required, set effective countermeasures, and resolve problems at the development and maintenance stages. Common omissions such as failing to validate input or weak error handling can be omitted.
Benefits of Threat Modeling
Let us discuss some of the benefits of threat modeling in this section:
- The steps involved in threat modeling provide a better understanding of network security and architecture to the team.
- Here, the security input is required from multiple stakeholders. They participate in making cybersecurity a core competency for the team or participants.
- Based on the threat data and vulnerabilities found, businesses gain the power to prioritize and decide which actions to take to address security risks. They can also allocate people and resources in the correct direction.
How does Threat Modeling Work?
Threat modeling works in 5 steps:
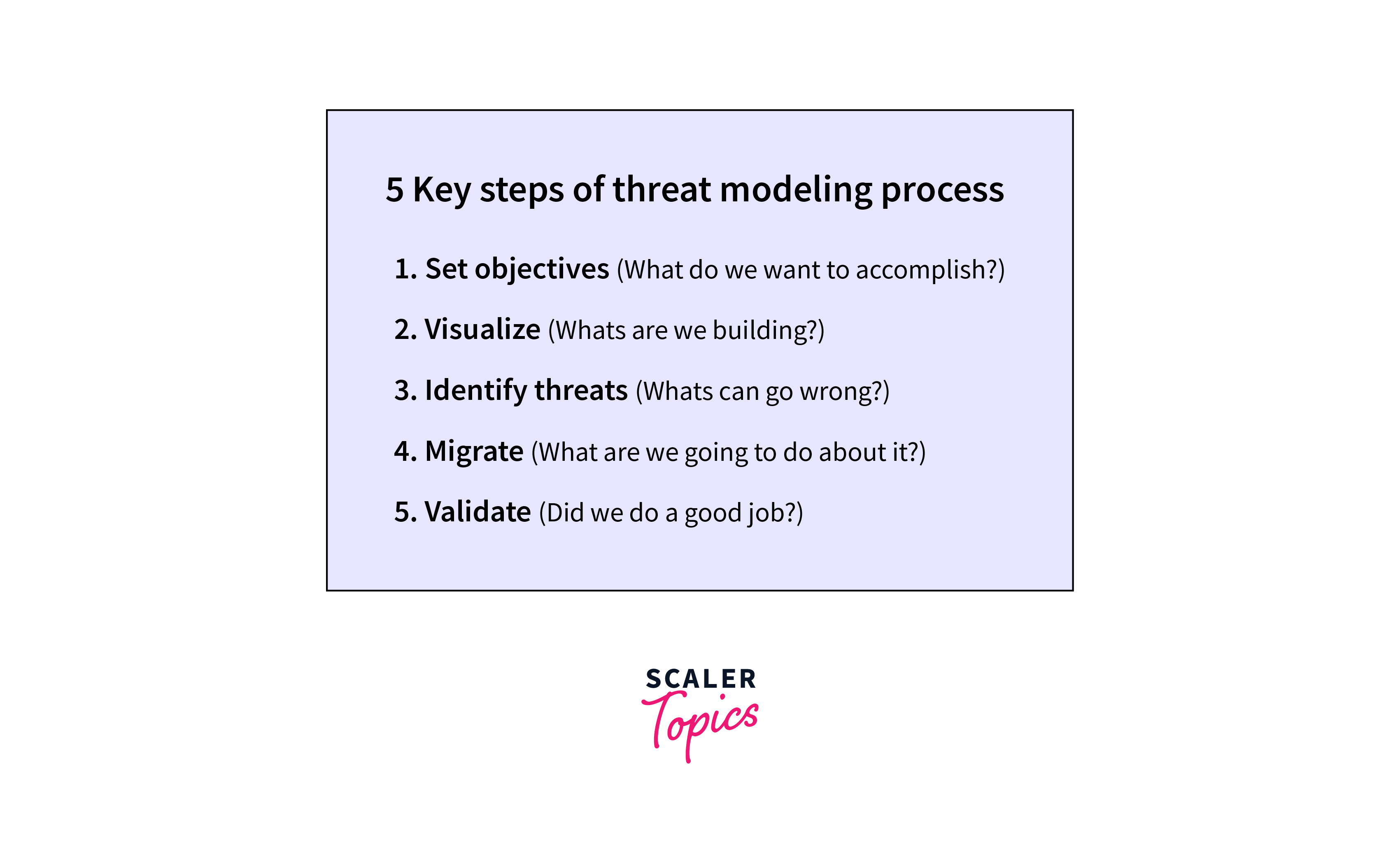
- Defining Security Requirements - It is very important to have a clear understanding of our security requirements. Our application must follow CIA Triad i.e. Confidentiality, Integrity, and Availability.
- Creating an Application Diagram - Based on our definition, we must create a Data Flow Diagram that provides a high-level, asset-centric view of systems and data flow attacks. An attack tree can also help trace the attack path easily.
- Identifying Threats - By analyzing process flows and using threat modeling methodologies, we can identify specific threat types, identify potential threats, map data flows, and quantify risks.
- Mitigating Threats - Mitigating threats means continuous investigation of each vulnerability that can cause threats so that effective measures can be taken. Many tools produce threat scores for risk calculation but stakeholder input is a must.
- Validating That Threats have been Mitigated - Once we identify the areas and assets that are threat-prone, the next steps are apparent. These could be changing encryption, firewall, multifactor authentication, etc.
Misconceptions of Threat Modeling
There are various misconceptions associated with threat modeling.
-
"Code reviews and penetration testing can substitute for threat modeling." Code reviews and penetration testing help in finding bugs in code. However, threat modeling is better at determining design flaws.
-
"Threat modeling shouldn't be done after deployment." While it is beneficial to start early in the design phase, continuing threat modeling post-deployment helps adapt to evolving risks, implement additional safeguards, and maintain a resilient security posture.
-
Threat modeling is complicated. Threat modeling sounds very daunting to most people at first glance, but it isn't that complicated. We break up the steps into workable tasks at different stages of development, and then
Other misconceptions include, "It is only for large organizations", "it is only a one-time process", "Only external threats should be considered", "it slows down the process", "threat modeling guarantees perfect security", etc.
Best practices of Threat Modeling
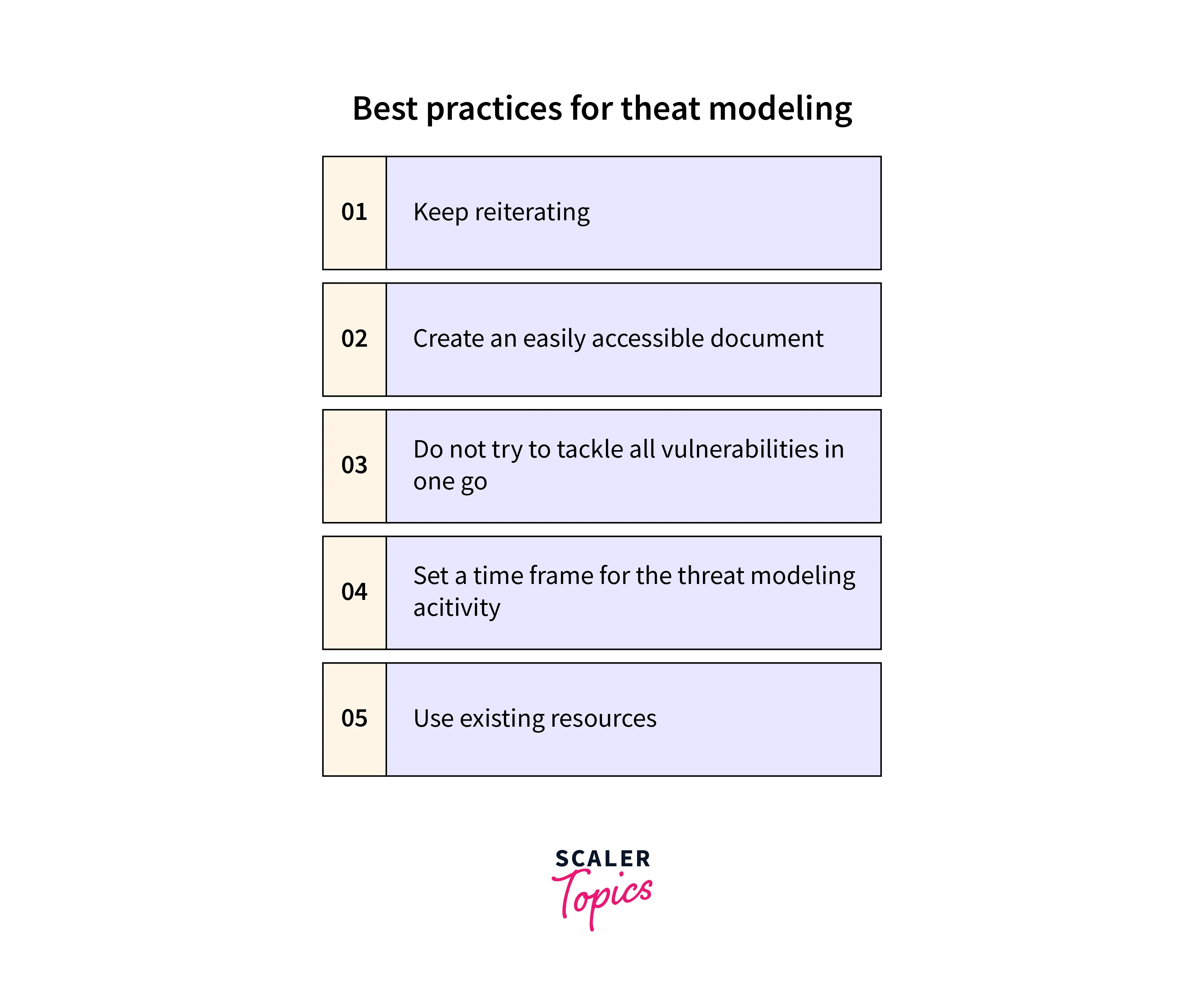
For an effective threat modeling approach several steps can be taken:
- Start Early - Threat modeling can be performed during any stage but performing it early saves costs and also ensures that our design is secure.
- Get an IOT of Input - Instilling input from various stakeholders helps us identify a wide range of potential adversaries, threats, motives, and vulnerabilities.
- Use a Variety of Tools - Many kinds of tools are available, each with its way of discovering threats. Using multiple tools gives us more than one perspective. For example, the University of Washington's Security Cards is a brainstorming tool that is capable of discovering novel attacks and their solutions.
- Understand Risk Tolerance - Risk tolerance must be defined prior by the business owners to take proper measures and approaches to threat mitigation.
- Educate Everyone - Threat modeling is an iterative approach, it cannot be done in one go. Training everyone will ensure maximum input at all stages of development and different aspects.
Other best practices are mentioned below:
Measure Effectiveness of Threat Modeling
Two ways to measure the effectiveness of threat modeling are:
- Common Vulnerability Scoring System (CVSS) - CVSS produces standardized scores for application vulnerabilities, IoT devices, It systems and elements, etc. These scores can be calculated with the help of free tools available online. For additional information, these scores can be compared with the existing score databases from similar enterprises.
- Penetration Testing - Penetration testing also known as "ethical hacking" is the process of simulating real-world cyberattacks to identify and exploit vulnerabilities in a system. These tests require a good amount of time and data analysis. Also, these tests must not be high-risk to justify the cost.
Threat Modeling Methodologies and Frameworks
Early modeling methodologies visualize data flow in an application or system using data flow diagrams. However, for modern applications deployed in highly interconnected environments, modern methodologies are required.
Process flow diagrams that show the data flow and interactions in a system or application from the perspective of the user are used nowadays. Other commonly used methods include attack trees to visualize attacks. The root indicates the target of an attack, leaves represent the starting point of an attack.
These methodologies provide structured frameworks and tools for identifying, prioritizing, and mitigating security threats during different stages of the software development lifecycle. Choosing the most suitable methodology often depends on the organization.
After the awareness, many frameworks and methodologies are developed. There are two types of methodologies, attack-centric which focuses on types of possible attacks, and assect-centric which focuses on asset-centric which focuses on the assets to be protected. Let us explore some of these:
-
Microsoft STRIDE:
- It is commonly used in the software development lifecycle to systematically identify and address potential security issues, providing a structured approach to threat modeling.
-
OWASP Threat Dragon:
- This web-based tool is suitable for both standalone use and integration into the development process. It facilitates the identification and analysis of threats, promoting effective mitigation strategies.
-
DREAD (Damage, Reproducibility, Exploitability, Affected Users, Discoverability):
- DREAD helps in prioritizing and addressing threats by assigning scores to each criterion, enabling organizations to focus on the most critical security issues.
-
IriusRisk:
- This platform supports various threat modeling methodologies and offers a collaborative environment for security teams. It assists organizations in systematically addressing potential security risks throughout the software development process.
Threat modeling tools
-
Microsoft Threat Modeling Tool (MTMT):
- Developed by Microsoft, MTMT aids in the identification and prioritization of potential security threats during system design.
- Integrating seamlessly with Visual Studio, facilitates a structured approach to threat modeling for enhanced cybersecurity.
-
OWASP Threat Dragon:
- As an open-source tool, OWASP Threat Dragon offers a visual representation of system architectures, allowing users to create and analyze threat models.
- This web-based application is designed for both standalone use and integration into the development process, promoting effective threat mitigation.
-
Safeguard by AECOM:
- Safeguard, a comprehensive threat modeling tool, provides a collaborative environment for security teams to create, visualize, and manage threat models.
- Supporting multiple methodologies, it empowers organizations to systematically address potential security risks.
-
PyTM (Python Threat Modeling):
- PyTM is an extensible open-source framework that allows users to create threat models using Python scripts.
- Its customizable nature enables organizations to tailor threat modeling processes to meet specific security requirements.
-
IriusRisk:
- IriusRisk is a threat modeling platform that seamlessly integrates with the development lifecycle.
- Utilizing a data-driven approach, it offers risk assessment and mitigation recommendations, supporting various threat modeling methodologies for robust security implementation.
-
Stride and DREAD:
- Stride and DREAD, though not traditional tools, serve as threat modeling frameworks.
-
Diagrams.net (formerly draw.io):
- Diagrams.net, a versatile diagramming tool, is often used to create visual representations of system architectures and threat models.
- Supporting various diagram types, complements other tools by aiding in the creation of detailed and informative threat model diagrams.
FAQ
Q. Does threat modeling require special software?
A. Threat modeling can be conducted using specialized software tools that provide a structured framework but manual methods, like drawing diagrams on paper or using generic diagramming tools, are also viable, depending on the complexity of the system.
Q. How do I measure the effectiveness of threat modeling?
A. The effectiveness of threat modeling can be measured through various metrics, including the CVSS and penetration testing. Regular reviews, stakeholder feedback, and the integration of threat modeling into the development lifecycle contribute to evaluating its impact.
Q. Is threat modeling available as a service?
A. Yes, threat modeling is available as a service through platforms like IriusRisk, which offers a cloud-based solution for organizations that often provide features that make threat modeling accessible and efficient for diverse teams.
Conclusion
- Threat modeling is used in cyber security to identify vulnerabilities in systems or software. Threats can be internal or external. Attackers and developers have different perspectives and thus, the project team must identify security controls and take effective measures.
- Threat modeling works in five stages defining requirements, application diagram, identifying and mitigating threats, and validating the process.
- There are various misconceptions involved that should be avoided and best practices must be considered such as starting early, using various tools, educate everyone.
- Various methodologies and frameworks are available and open-source tools also help identify and mitigate risks that should be used.
