Token Bus (IEEE 802.4)
Overview
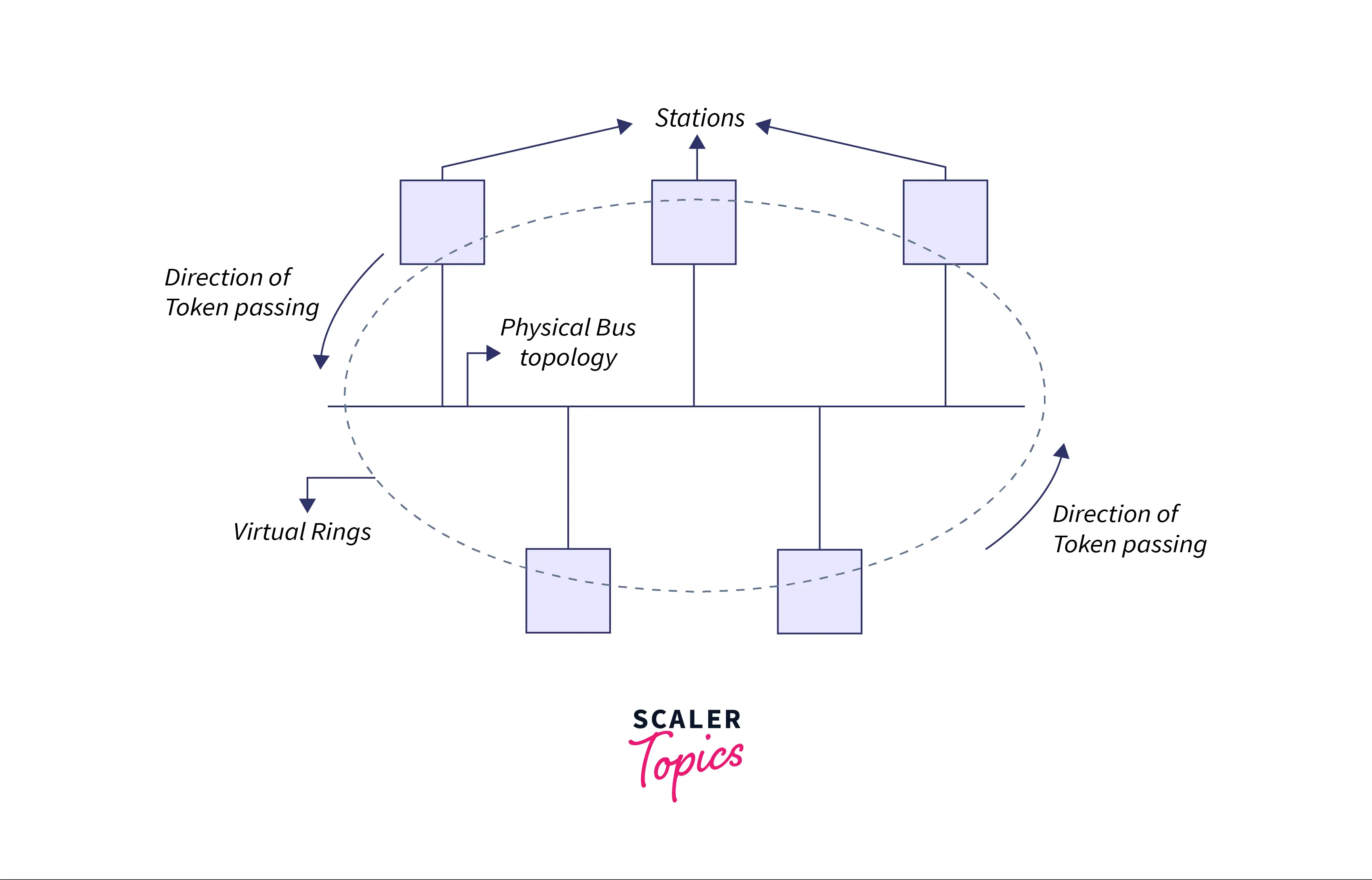
Token bus is a popular standard for token passing LANs. It was standardized by IEEE standard 802.4 and is mainly used for industrial applications. In a token bus LAN, stations are used to create a virtual ring, and tokens are then passed from one station to another using this virtual ring. Every station or node in the token bus network knows the address of its "left" and "right" station. A node or station can transmit the data only when it holds a token. The working of the Token Bus is similar to a token ring.
What is Token Bus (IEEE 802.4)?
Token Bus (IEEE 802.4) is a network for implementing token rings over the virtual ring in LANs. The physical media in a token bus uses coaxial cables and has a bus or tree topology. The nodes or stations are used to create a virtual ring, and the token is passed from one node to another node in a sequential manner along this virtual ring. The addresses of each node's preceding and succeeding stations are known to them.
The token is required for a station to transmit data. When a node on the virtual ring has nothing to send, the token is passed on to the next node. A token bus network is similar to the token ring network but works around the virtual ring instead of a physical ring.
Token Passing Mechanism in Token Bus
In a computer network, a token is a brief message that travels among the stations and provides them permission for transmission. When a station receives a token, if it has data to transmit, it transmits the data and then passes the token to the following node or station; otherwise, it just passes the token to the next station. The diagram below shows how this works.
Frame Format of Token Bus
The following are the fields in the frame format of the token bus:
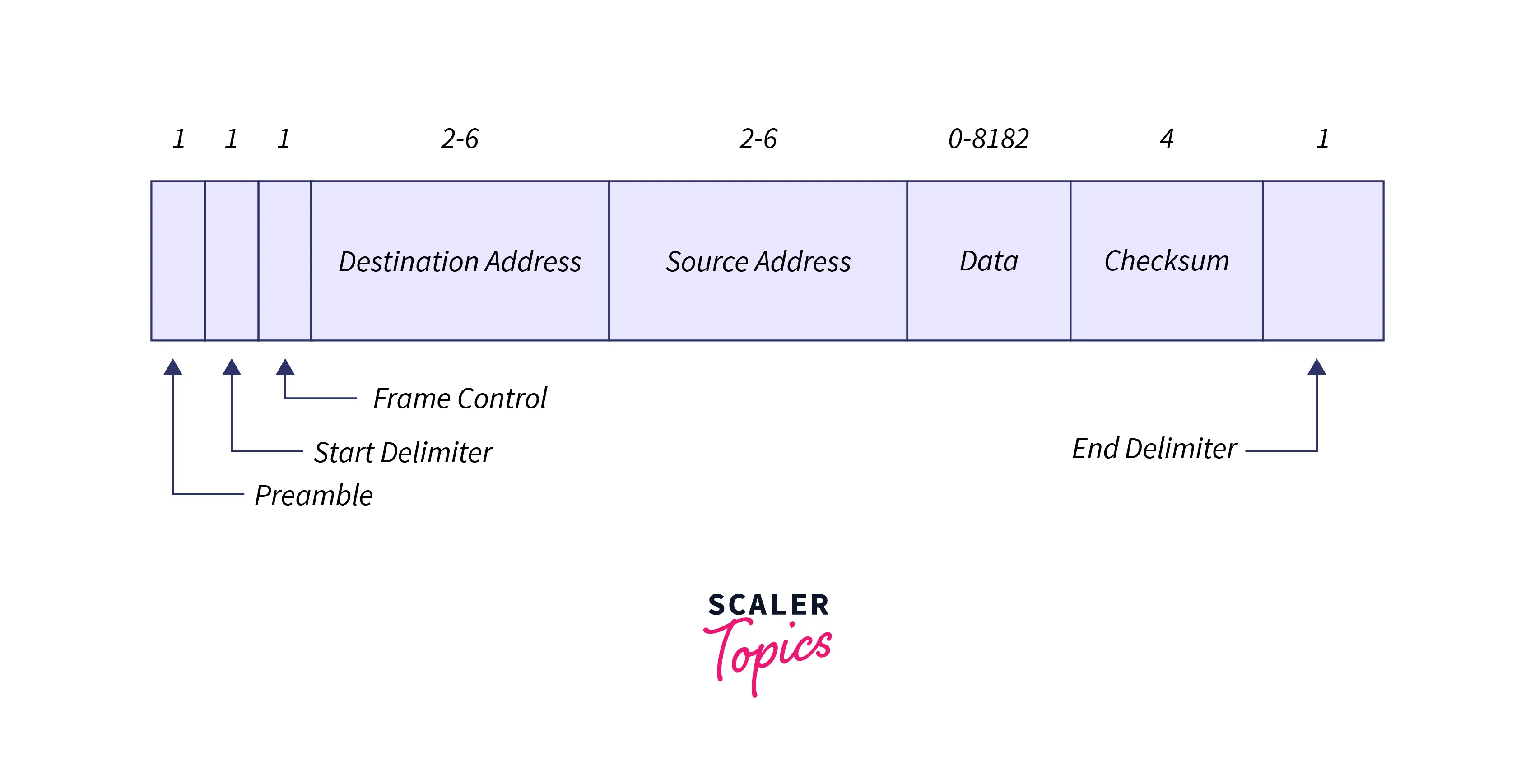
- Preamble: It is a 1-byte field and is used for bit synchronization.
- Start Delimiter: It is a 1-byte field that marks the beginning of the frame.
- Frame Control: It is a 1-byte field that specifies the frame type and distinguishes data frames from control frames.
- Destination Address: This is a 2 to 6 bytes field containing the address of the destination station.
- Source Address: This is a 2 to 6 bytes field containing the address of the source station.
- Data: This variable length field carries the data from the network layer. The field can be up to 8182 bytes when using 2-byte addresses and 8174 bytes when using 6-byte addresses.
- Checksum: It is a 4-byte field with checksum bits that detect errors in transmitted data.
- End Delimiter: It is a 1-byte field that marks the end of the frame.
The Token-passing Bus Protocol Functions
The token bus protocol offers the following functions:
- Ring initialization: Ring initialization is performed when a network is powered on for the first time and after a catastrophic error.
- Station addition: Station addition is selectively performed when a station holding a token allows the insertion of a new successor station (i.e., a brand-new station with an address) that lies between that station and its existing successor station.
- Station removal: Station removal can be performed by disconnecting it from the LAN or sending a new successor identifier to the station's predecessor. Recovery mechanisms establish the appropriate new logical ring configuration in the later scenario.
- Recovery and Management: Recovery from failures such as bus idle (lack of activity on the bus), token-passing failure (lack of valid frame transmission), the existence of duplicate token, and the detection of a station with a malfunctioning receiver are all included in management and recovery.
Physical Layer of the Token Bus
The physical layer of the token bus can be made of the conventional 75-ohm coaxial cable that is used for cable TV. Various modulation techniques are employed. The various modulation techniques used are multilevel dual binary amplitude-modulated phase shift keying, phase coherent frequency shift keying, and phase continuous frequency shift keying. It is possible to get signal speeds in the 1 Mbps, 5 Mbps, and 10 Mbps ranges. The token bus's physical layer is completely incompatible with the IEEE 802.3 (Ethernet) standard.
MAC Sublayer Function
- Stations are added to the ring in ascending order of station address when it is first initialized.
- Tokens are passed from high to low addresses.
- Once a station receives the token, it can transmit frames for a predefined timeframe.
- If a station doesn't have any data, it passes the token right away.
- The token bus divides traffic into four priority classes, with 0 being the lowest and 6 being the highest: 0, 2, 4, and 6.
- Each station has four internal substations, one for each priority level (0, 2, 4, and 6).
- Data are prioritized and routed to one of the four substations as input arrives at the MAC sublayer from above.
- As a result, each station keeps track of its own queue of frames to be transmitted.
- A token is passed internally to the priority six substation when it enters the station via the cable so that it can start transmitting its frames if it has any at that time.
- When it is finished, or its timeout ends, the token is passed to the priority four substations, which can transmit frames until its timeout expires. The token is then internally transferred to the priority two substations after that.
- This process continues until the priority 0 substation has sent all of its frames or its time has run out.
- The token is then passed to the next station in the ring.
Logical Ring Maintenance
Key components of ring maintenance include:
Adding new stations: How do we extend a logically closed ring by adding new stations?
- Each station knows its predecessor's and successor's physical addresses when the ring is established. Therefore, there is no doubt regarding the token passing order.
- The token holder periodically sends out the SOLICIT_SUCCESSOR{ownaddress, successor's address} message.
- A contention algorithm similar to the CSMA/CD is used to select one successor if two or more new stations contend with being the successor.
- For each token rotation, a single station can only be added.
Leaving the ring: When the station leaves the ring, it would be better to ensure that its neighbors form a new ring without using its address.
- Send the message to the predecessor: One station's successor now becomes the other station's successor and stops transmitting. For example: If station C leaves the ring (A → B → C → D →A), then the successor of C becomes the successor of B (i.e., A → B → D →A).
Initialization: What happens when the network is first turned on?
- Observe the ring for a while after joining the line.
- If there is no token activity, broadcast a CLAIM_TOKEN message to the bus and start an independent ring.
- A CSMA/CD-like protocol determines the winner if more than two stations deliver the CLAIM_TOKEN message.
- New stations are inserted within the ring.
Error Recovery: What happens if the token is lost due to transmission issues or if the token owner crashes accidentally?
- Monitor the channel after passing the token and realizing it has been destroyed.
- After that, send the WHO_FOLLOWS{MY_SUCCESSOR_ADDRESS} message to the successor.
- As soon as the down station successor reads the above message, it declares itself the new successor.
Difference between Token Bus (IEEE 802.4) and Token Ring (IEEE 802.5)
| Sr. No. | Token Bus | Token Ring |
|---|---|---|
| 1. | It is defined by IEEE 802.4 standard. | It is defined by IEEE 802.5 standard. |
| 2. | In the token bus, bus topology or tree topology is the underlying topology that connects the stations. | In the token ring, ring topology, or sometimes star topology, connects the stations together. |
| 3. | LAN-connected stations form a virtual ring around which the token is passed. | The stations and coaxial cable network form a physical ring around which the token is passed. |
| 4. | Token bus is less expensive than Token Ring. | Token ring is more expensive than Token Bus. |
| 5. | Calculation of the time for token transfer is not feasible. | The amount of time it will take a token to reach a station can be calculated. |
Conclusion
- Token Bus (IEEE 802.4) is a network for implementing token rings over the virtual ring in LANs.
- In a token bus LAN, stations are used to create a virtual ring, and tokens are then passed from one station to another using this virtual ring.
- In a computer network, a token is a brief message that travels among the stations and provides them permission for transmission.
- The physical layer of the token bus can be made of the conventional 75-ohm coaxial cable that is used for cable TV.
- In a token ring, the maximum time for a token to reach a station can be calculated, but not in the case of a token bus.
- A token bus network is similar to the token ring network but works around the virtual ring instead of a physical ring.
