A VLAN or Virtual Local Area Network is a customized network built from one or more local area networks. It allows a group of devices from different networks to be integrated into a single logical network. As a result, a virtual LAN is created that can be managed just like a physical LAN. Without VLANs, a broadcast from a host can easily reach all network devices. Every device will process broadcast received frames. It can raise CPU overhead on each device and degrade overall network security. The VLAN is used to solve this problem by creating multiple broadcast domains in a network.
What is VLAN?
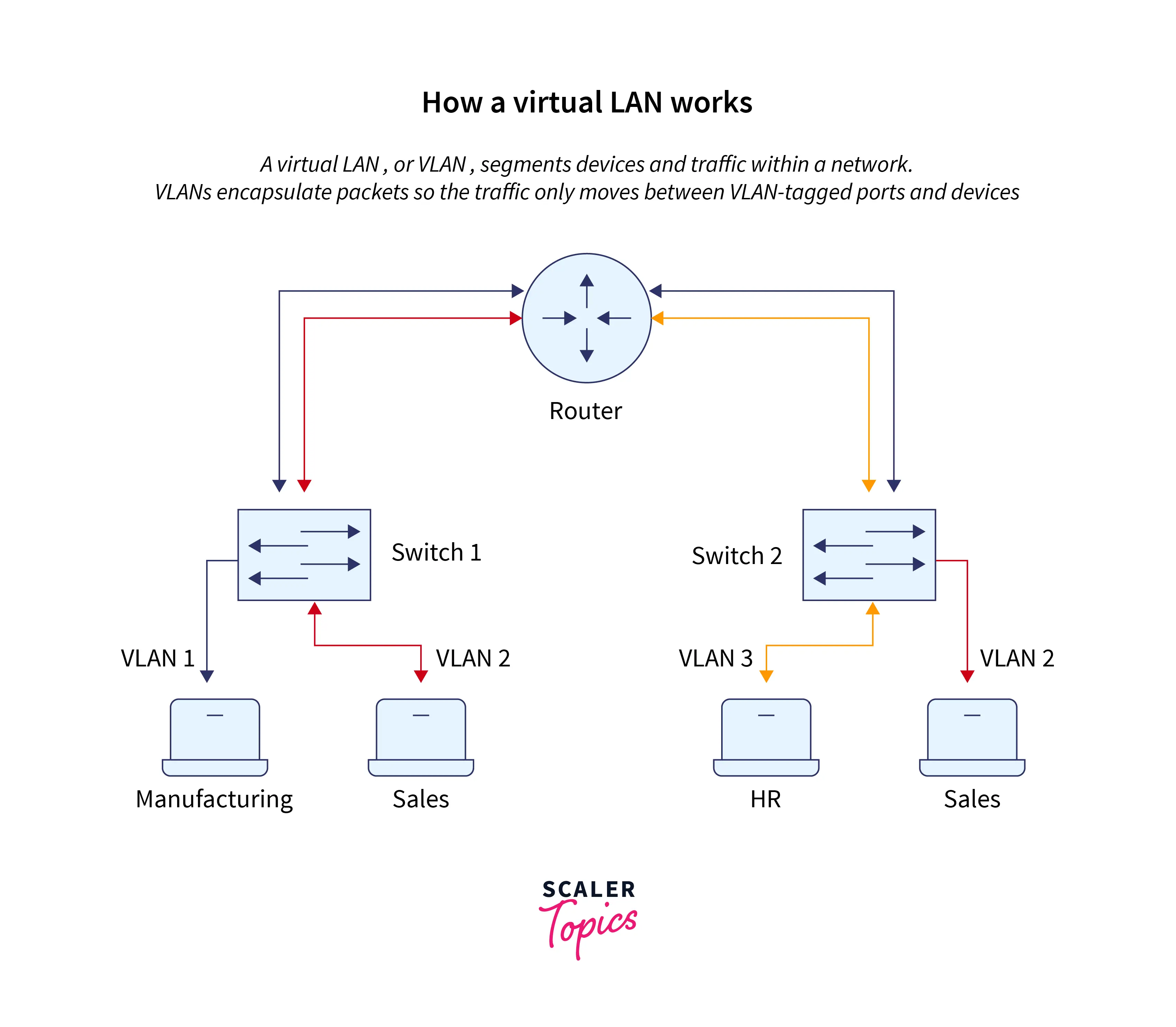
Virtual Local Area Networks, also known as Virtual LANs, are logical groups of computers that appear to be connected to the same local area network (LAN), irrespective of how the underlying physical network is set up. Network managers divide the networks into VLANs, with each VLAN consisting of a subset of ports on one or more switches or bridges, depending on the functional requirements of the VLANs. This enables devices and computers in a VLAN to communicate in the simulated environment as though it were a different LAN.
A VLAN can logically partition and isolate one or more physical LANs into numerous broadcast domains. Furthermore, each broadcast domain is treated as a separate VLAN. In general, only devices on the same VLAN can communicate.
In the LAN application topology shown below, host A will broadcast its ARP (address resolution protocol) request to all switches and hosts on the same local area network to communicate with host B. Without VLANs, a broadcast from a host can easily reach all network devices. Every device will process broadcast received frames. It can raise CPU overhead on each device and degrade overall network security.
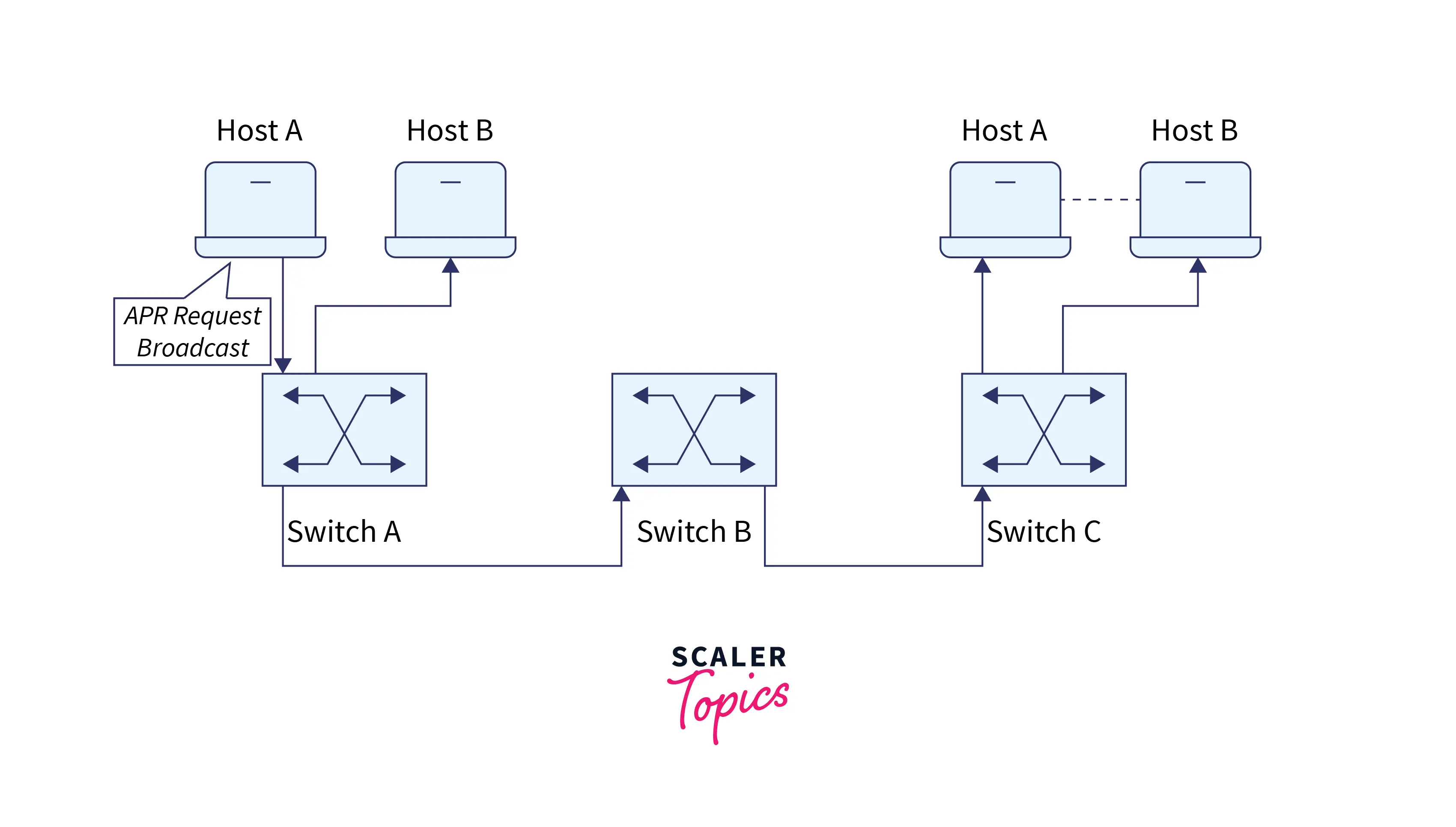
By creating VLANs, you can partition a network into different broadcast domains. Bridges or switches convey packets sent by workstations on a single network segment rather than forwarding conflicts to each network device. This eliminates most of the potential complications caused by Lans, such as increased network traffic and disputes. This saves network resources and bandwidth, boosting network flexibility and performance.
Features of VLANs
The features provided by the VLANs are as follows:
- Depending on their systems’ functional and security needs, network administrators can quickly divide a single switched network into different networks using VLANs.
- The network manager can divide LANs logically into various broadcast domains with the help of VLANs.
- Devices on separate physical LANs are grouped together by a VLAN to establish a sub-network.
- VLANs also improve security management, permitting device partitioning based on security requirements and ensuring a higher level of control over connected devices.
- One or more network bridges or switches may be used to create multiple, independent VLANs.
- VLANs operate at the OSI model’s layer 2, or Data Link Layer.
- VLANs reduce the need to install new cables or reconfigure physical connections in existing network infrastructure.
- VLANs are more adaptable than physical LANs since they are made up of logical connections. This allows for faster and less expensive device reconfiguration when the logical segmentation needs to be modified.
- VLANs enable large businesses to re-partition equipment to improve traffic management.
VLAN Ranges
| Range | Description |
|---|---|
| VLAN 0-4,095 | These are reserved VLANs, and they cannot be seen or used. |
| VLAN 1 | This is the switch’s default VLAN. This VLAN cannot be deleted or modified but can be used. |
| VLAN 2-1,001 | It is a standard VLAN range. It is possible to create, edit, and delete it. |
| VLAN 1,002-1,005 | These are the CISCO defaults for FDDI and token rings. These VLANs cannot be revoked. |
| VLAN 1,006-4,094 | This is Vlan’s extended range. |
Purposes of a VLAN
The network engineers can use the VLANs for the following purposes:
To Improve Performance
VLANs can improve device performance by limiting the amount of traffic that a given endpoint sees and processes. VLANs divide broadcast domains, decreasing the number of other hosts from which each given device receives broadcasts. For example, if all desktop voice-over IP phones are on one VLAN and all workstations are on another, phones will not receive any workstation-generated broadcast traffic and vice versa. Each can limit its network resources to relevant traffic exclusively. A separate set of traffic-handling rules can be established by engineers for each VLAN. For instance, to help or ensure the operation of telepresence devices, they can set rules to prioritize video traffic on a VLAN connecting conference room equipment.
To Ease Administration
Administrators can also organize devices for purely administrative, non-technical reasons using VLANs to group endpoints. For instance, they might group all computers used for accounting into one VLAN, all computers used for human resources into another, and so on.
To Tighten Security
By giving you more control over which devices can communicate with each other, virtual LAN partitioning can also improve security. For instance, Network teams may limit management access to specific VLANs for network hardware or IoT devices.
Types of Connection in VLANs
There are three ways to connect devices to a VLAN, and the type of connection depends on the connected devices, such as whether they are VLAN-aware (devices that comprehend VLAN formats and membership) or VLAN-unaware (devices that do not comprehend VLAN formats and membership).
True Link
All devices connected to a trunk link must be VLAN-aware. All frames on this page should have a specific header called tagged frames linked to them.
Access Link
It connects devices that are uninformed of VLANs to a bridge that is aware of VLANs. The access link requires that all frames be untagged.
Hybrid Link
It combines the Trunk link and the Access link. Here, devices that are both VLAN-unaware and VLAN-aware are connected, and frames can be both tagged and untagged.
Types of VLAN
The various types of VLANs are described below:
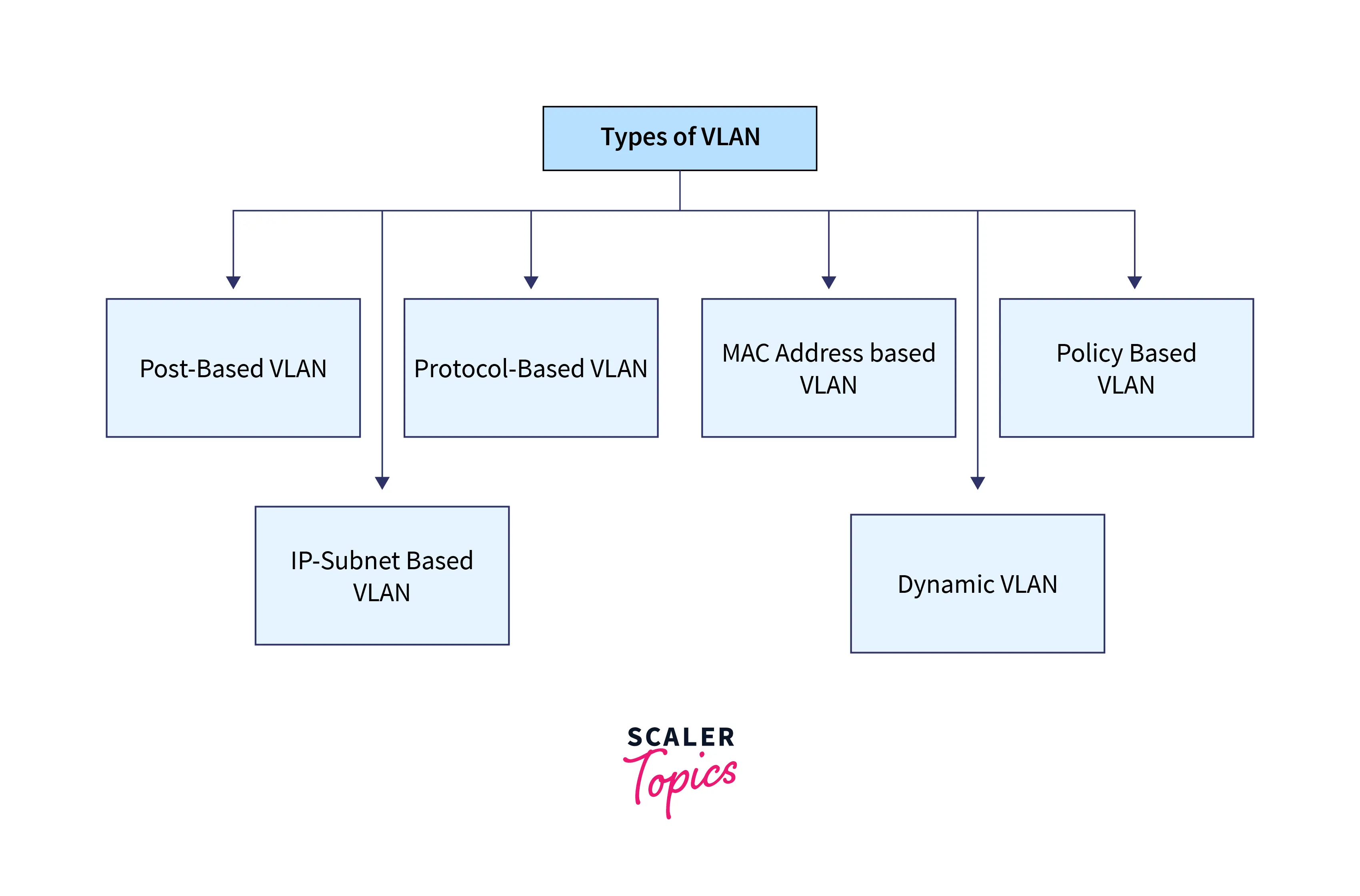
Port-Based VLAN
Port-based VLANs organize virtual local area networks by port. A switch port in this sort of virtual LAN can be manually assigned to a VLAN member. Because all other ports are configured with an identical VLAN number, devices connected to this port will be part of the same broadcast domain.
The difficulty with this network architecture is determining which ports are appropriate for each VLAN. It is impossible to determine the VLAN membership by simply glancing at a switch’s physical port. By looking at the configuration data, you can find out.
Protocol-Based VLAN
This kind of VLAN manages traffic in accordance with a protocol that can be used to provide filtering criteria for tags, which are untagged packets. This Virtual Local Area Network frame carries the layer-3 protocol to determine VLAN membership. Multi-protocol environments are supported by it. In a primarily IP-based network, this approach is impractical.
MAC Address-Based VLAN
With MAC Based VLAN, untagged incoming packets can be assigned to a virtual LAN and subsequently classified based on the packet source address. By configuring mapping from the MAC entry to the VLAN table, you can define a Mac address to VLAN mapping. This entry specifies the correct VLAN ID based on the originating Mac address. All device ports share table configurations.
IP Subnet-Based VLAN
IP subnet-based VLANs can assign VLANs based on the IP subnets of devices. It will be a good solution for a public network with a high need for mobility and simpler management but a low demand for security. Users can utilize this technology to automatically join a new VLAN ID if their IP address changes.
Policy-Based VLAN
A policy-based VLAN is a combination of the IP-based VLAN and MAC-based VLAN. It can assign VLANs based on policies such as MAC address and IP address combinations. Network security and flexibility will be substantially improved by combining policies to implement inter-VLAN access control.
Dynamic VLAN
Network engineers build use-based VLANs by dynamically assigning traffic to a VLAN based on the kind of traffic or the device generating the traffic. A port may be assigned to a VLAN based on the identity of the device attached (as evidenced by a security certificate) or the network protocols in use. A single port can be assigned to several dynamic VLANs. Changing the device connected to a port, or even how the present device is used, may cause the VLAN allocated to the port to change.
Working of VLAN
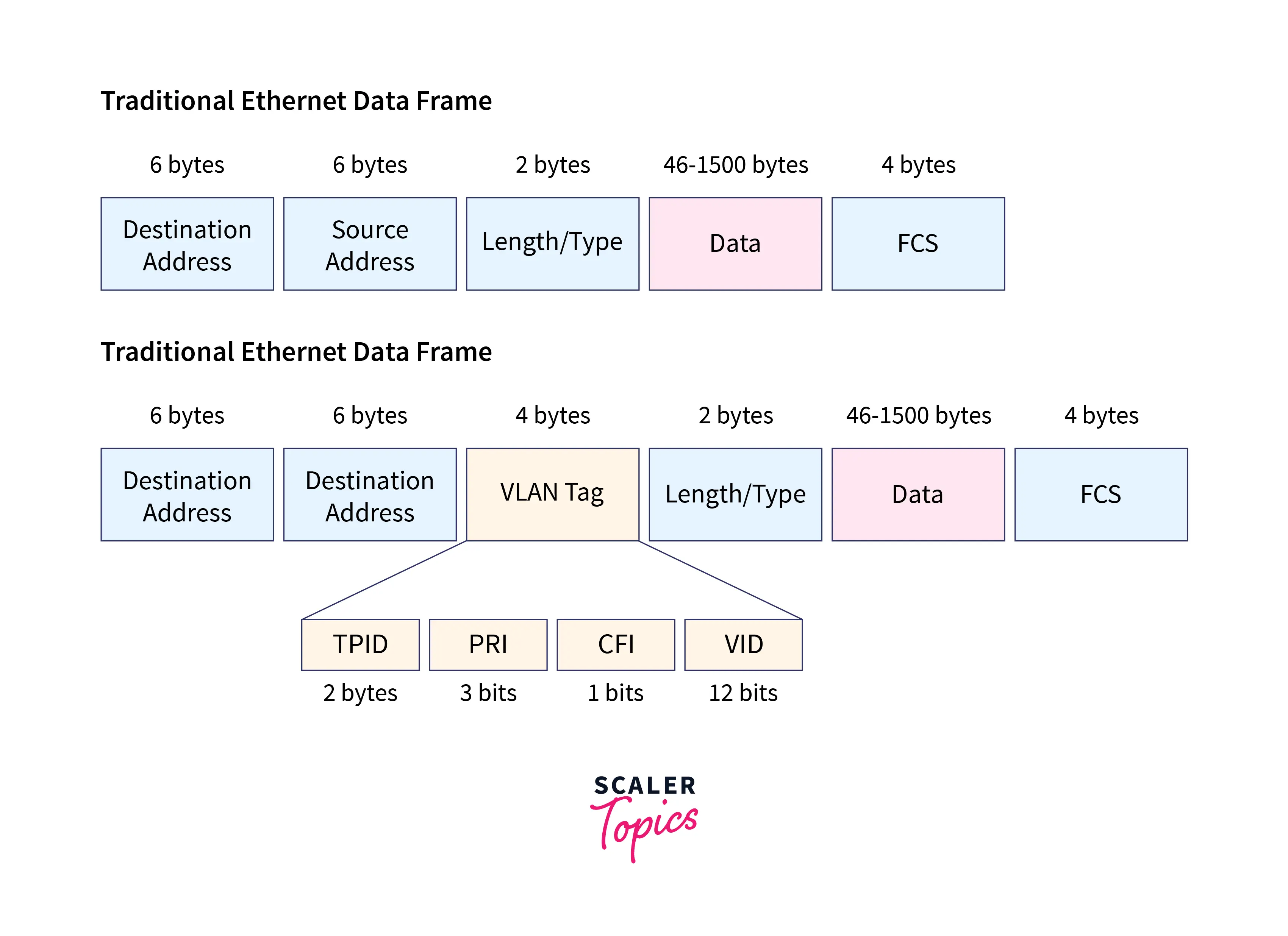
A VLAN ID is used on network switches to identify a VLAN. Each port on a network switch can have one or more than one VLAN IDs allocated to it, and if none are specified, it will land in the default VLAN. Each VLAN gives data-link access to all hosts connected to switch ports with the VLAN ID assigned to them. A VLAN (Virtual Local Area Network) ID is translated to a VLAN tag, a 12-bit field in the header data of every Ethernet packet delivered to that VLAN. Since, a tag is 12 bits long, up to 4,096 VLANs can be established per switching domain. IEEE’s 802.1Q standard defines VLAN tagging.
A VLAN tag is absent from Ethernet frames that are received from connected hosts. The VLAN tag is added to the ethernet frame by the switch. In a static VLAN, the switch inserts the tag corresponding with the VLAN ID of the ingress port. It adds the tag associated with that device’s ID or the type of traffic it creates into a dynamic VLAN. Only ports that are connected to the VLAN and have the destination media access control address are forwarded by switches. Broadcast, unknown unicast, and multicast traffic is routed to all VLAN ports. Trunk links between switches are aware of which VLANs span the switches, accepting and forwarding all traffic for any VLAN in use on both sides of the trunk. Before a frame is transferred to the destination device, the VLAN tag is removed when it reaches its destination switch port.
STP(Spanning Tree Protocol) is used to establish a loop-free topology among the switches in each Layer 2 domain. A per-VLAN STP instance can be used, allowing for various Layer 2 topologies. If the topology is the same across several VLANs, a multi-instance STP can be employed to reduce STP overhead.
Use Cases of VLAN
Some VLANs have straightforward and practical goals, such as restricting printer access. Administrators can configure them so that computers on any given VLAN can view printers on that VLAN but not those outside it.
Other VLANs are used for more complicated tasks. For example, computers in a corporate banking department cannot communicate with computers in trading departments. Network engineers can enforce such segregation by creating different VLANs for each department.
How to Manage and Configure VLAN?
A virtual LAN’s objective is to provide a valuable layer of intercommunication within LANs and connected devices. Switch ports are critical components of this network configuration because they allow many devices from different LANs to be grouped. Communication and data sharing among devices have become more managed and convenient.
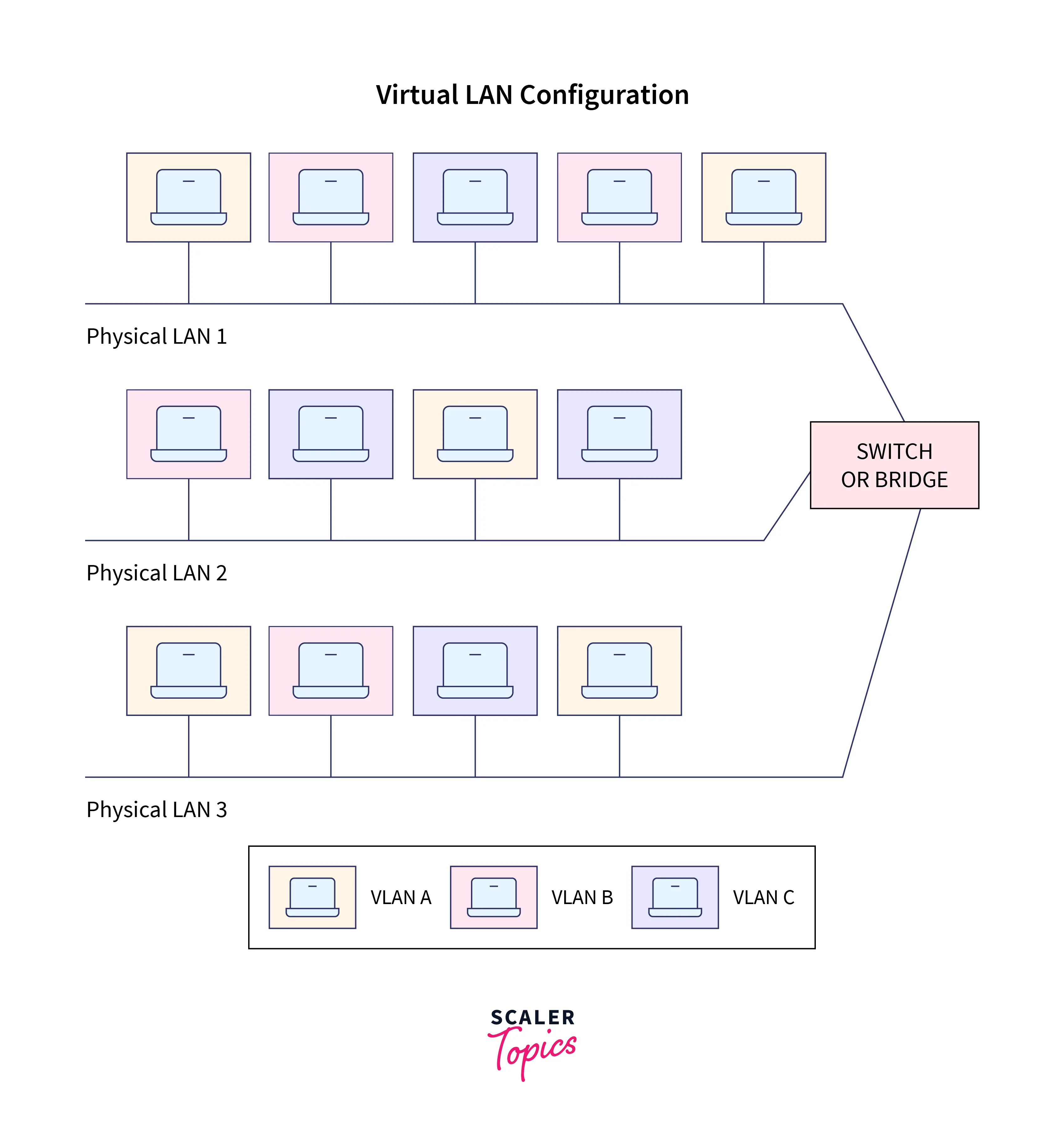
How to Configure a Virtual LAN?
The procedure of configuring virtual LANs is identical to that of configuring physical networks. Firstly, you must identify the network nodes that you will be managing. The next step is creating VLAN configuration files to keep track of detecting nodes. After configuring them, you can archive or edit them for troubleshooting diagnostics. Using VLAN configuration tools to exchange information and automate configuration file changes is one of the simplest ways to set up VLAN setups.
Why is VLAN Management Critical?
Manual VLAN management can be complex, especially in large networks with multiple LANs. Manual execution and configuration changes increase the possibility of mistakes and errors, which might result in downtime and latency concerns. It can also cause unneeded or ineffective conflicts with your security compliance reports. The best way to maintain security and compliance standards and detect any vulnerabilities in your virtual network is to retain an accurate and up-to-date configuration setup.
VLAN management software allows you to obtain real-time network updates and fast alerts regarding changes in network nodes. These tools can also aid in disaster recovery planning.
Difference between LAN and VLAN
| LAN | VLAN |
|---|---|
| LAN stands for Local Area Network | VLAN stands for Virtual Local Area Network |
| A local area network (LAN) is a collection of computer and peripheral devices linked in a specific geographic area. | A VLAN is a custom network that is built from one or more local area networks. |
| The network packet is advertised to each and every device in a LAN. | The network packet is only transmitted to a specific broadcast domain in a VLAN. |
| The LAN has a high latency. | VLAN has a lower latency. |
| It employs a ring and the FDDI (Fiber Distributed Data Interface) protocol. | It employs ISP and VTP as protocols. |
| Overall cost in LAN is generally high as compared to VLAN | Overall cost is less as compared to LAN |
Advantages of VLAN
Flexibility to create virtual groups
Every firm has different departments, such as sales, finance, and others, thus VLANs can be pretty helpful in organizing the devices logically by departments.
Performance
There is a lot of broadcast and multicast traffic on the network. VLAN eliminates the need to route such traffic to irrelevant destinations. For example, if the traffic is intended for two users, but ten devices are in the same broadcast domain, all would receive the data, resulting in bandwidth waste; but, if we create VLANs, the broadcast or multicast packet will only go to the intended users.
Security
Sensitive information may be broadcast over the same network and accessible by third parties, but by establishing a VLAN, we can regulate broadcast domains, install firewalls, and limit access. VLANs can also be used to alert the network administrator to an incursion. VLANs significantly improve network security as a result.
Minimize Cost
Broadcast domains can be built using VLANs, eliminating the requirement for expensive routers. By implementing Vlan, more compact broadcast domains can be created, which are simpler to manage than larger broadcast domains.
Flexibility
VLAN gives us the freedom to add and remove as many hosts as we like.
Disadvantages of VLANs
Apart from the various advantages VLANs provide to the network administrator, VLANs also have some disadvantages.
The limit of 4096 VLANs per switching domain
One downside of VLANs is the limitation of 4,096 VLANs per switching domain in a modern data center or cloud infrastructure. A single network segment can host tens of thousands of systems and hundreds or thousands of separate tenant organizations, each of which may require tens or hundreds of VLANs. Additional protocols such as Virtual Extensible LAN, Network Virtualization utilizing Generic Routing Encapsulation, and Generic Network Virtualization Encapsulation have been developed to overcome this restriction. They feature larger tags, allowing for additional VLANs to be formed and the ability to tunnel Layer 2 frames within Layer 3 packets.
VLAN identification with wall jacks and APs
Another issue with VLANs is that it can be challenging to identify which VLANs a given wall jack or AP has access to. This can make connecting new devices to the network more challenging for end users and field service support workers. Another problem that isn’t specific to VLANs but affects them is inadequate planning, which makes the overall VLAN design too complicated, brittle, and difficult to sustain when needs and underlying network equipment change.
Managing spanning tree structures
Another downside is that when VLANs are numerous and significant, the network may struggle to manage the spanning tree structures required to avoid traffic loops. The simplest solution is to reduce redundant network links. Unfortunately, this exposes the network to a single point of failure whenever a redundant link is severed.
VLAN ACL (VACL)
Virtual LAN is a concept in which the broadcast domain is conceptually divided into smaller broadcast domains at layer 2. When we build various VLANs, a host from one VLAN can communicate with all hosts in the same VLAN by default. If we want some hosts to be unable to communicate with other hosts on the same VLAN, we can utilize the VLAN Access list(VLAN ACL) or Private VLAN concepts. (An access list is a collection of different permit or deny conditions used for packet filtering.)
VLAN ACLs filter VLAN traffic (traffic within a VLAN i.e., traffic for destination host residing in the same VLAN). All packets entering the VLAN are compared against the VACL. In contrast to Router ACL, VACL is not defined in a direction, although it is feasible to filter traffic based on traffic direction by combining VACLs and Private VLAN capabilities.
Procedure
- Define the VACL’s standard or extended access list:- An access list should be developed to identify the type of network traffic and the hosts to which it is applied.
- Construct a VLAN access map:- A VLAN access map is constructed in which hosts’ IP addresses are matched (using the access list defined)
- Create an action clause in a VLAN access map sequence:- This will indicate whether to move forward or stop moving in the traffic (defined in the VLAN access map).
- Apply the VLAN access map to the VLANs you’ve chosen:- Creating a filter list indicating the VLAN to which the access map has been applied is the final stage in the configuration of VACL.
- Display information about VLAN access maps:- Using the command, we can confirm the information.
Types of Port
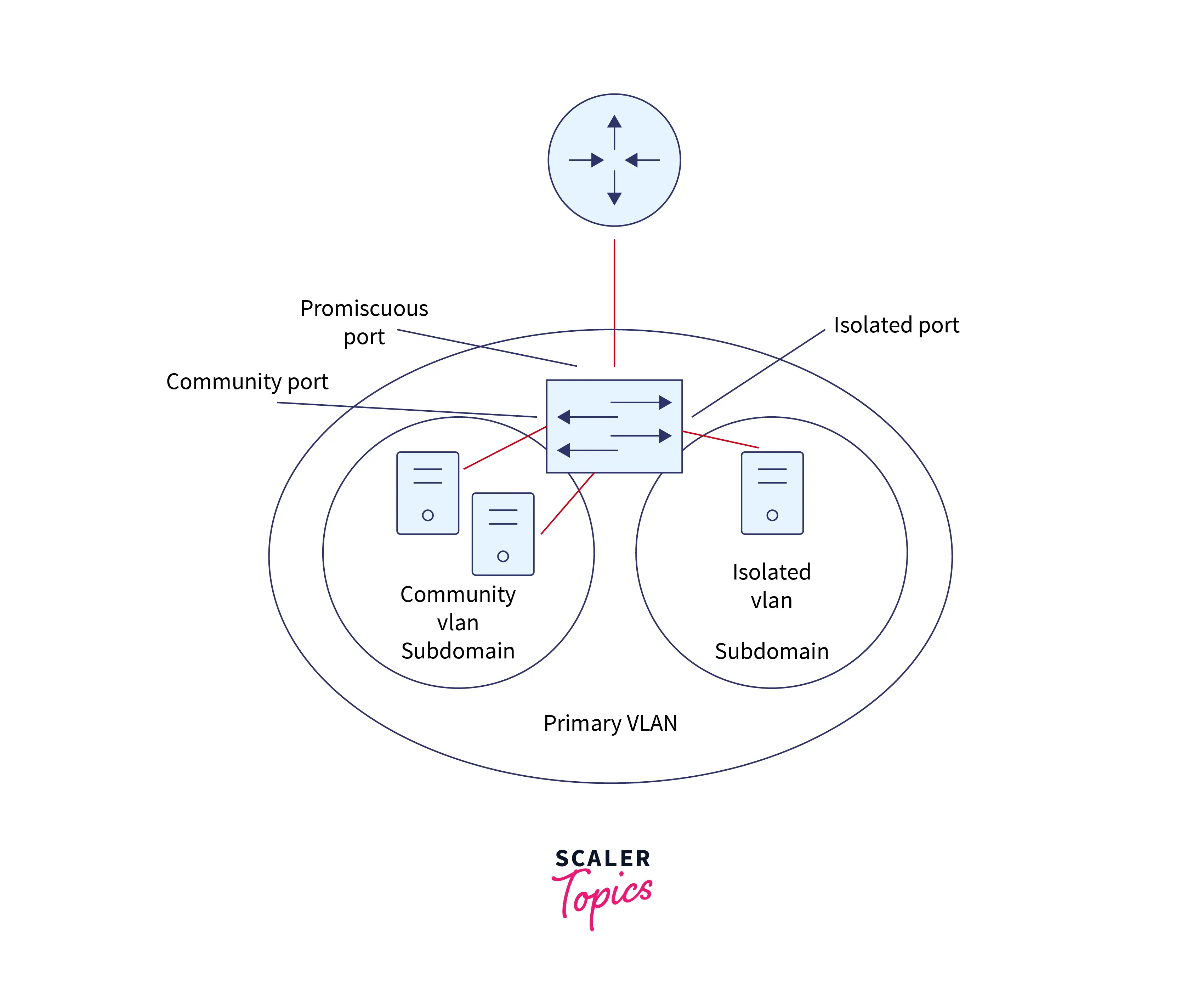
- Promiscuous port is part of the primary VLAN. These ports can communicate with all secondary VLAN interfaces associated with that promiscuous and primary VLAN port. It is generally used to link switches to routers, firewalls, and other devices.
- An isolated port is part of a secondary isolated VLAN. These are the host ports whose traffic is forwarded to the promiscuous port. A VALC enables only traffic to the isolated port that originates from its linked promiscuous port.
- Community port is a member of a secondary community VLAN. These host ports can connect with other ports in the same community VLAN as well as with the promiscuous port associated with them. These ports are totally isolated from the rest of the community VLAN and isolated ports.
Conclusion
- A VLAN or Virtual Local Area Network is a customized network built from one or more local area networks. It allows a group of devices from different networks to be integrated into a single logical network.
- By creating VLANs, you can partition a network into different broadcast domains. This eliminates most of the potential complications caused by Lans, such as increased network traffic and disputes. This saves network resources and bandwidth, boosting network flexibility and performance.
- The network engineers can use the VLANs for the following purposes:
- to improve performance
- to tighten security
- to ease administration
- There are three ways to connect devices to a VLAN:
- True Link
- Access Link
- Hybrid Link
- The five types of VLANs are mentioned below:
- Protocol VLAN
- Port-based VLAN
- Dynamic VLAN
- MAC Address-based VLAN
- IP subnet-based VLAN
- Policy-based VLAN
- VLAN ACLs filter VLAN traffic (traffic within a VLAN i.e., traffic for destination host residing in the same VLAN). All packets entering the
VLANare compared against the VACL.
