Cryptography and Its Types in Cybersecurity
Overview
Modern networking and exchanging data between various devices often require security postures to transmit and store them safely. Data security is essential so that adversaries cannot alter or read them. Passwords are the most well-known example that goes from our client systems to servers and gets verified before giving us access to systems. Those passwords go in an unreadable format. Thus cryptography plays a significant role in securing data at rest and in transit. This article will give a quick walkthrough of cryptography in cybersecurity.
Introduction
We all have heard about encryption-decryption and end-to-end encryption concepts. Even these terms got popular in the news through WhatsApp and other social media apps. Nowadays, all digital activities involve the internet, apps, electronic services, and data. Whether you buy things online or send money to someone's account, data is one crucial thing that needs robust security. Thus, cybersecurity has a significant branch to distort normal data to some other form. That domain of cybersecurity that encrypts or decrypts the data at rest and in transit through different algorithms is cryptography. Without further ado, let's jump into the details of cryptography in cybersecurity and its types.
What Is Cryptography?
Cryptography (kryptós means secret and graphein means to write) is the science and art of concealing data and information in an unreadable format so that only the intended person can read or use it. In other words, it is the study of secure communication that allows only the intended recipient and, of course, the message sender to view the message contents. Cryptography in cybersecurity entails the use of encryption and decryption algorithms. Converting the plain text (readable text) to cipher text (unreadable text) is called encryption, and reversing the process (cipher text to plain text) is called decryption. The effectiveness of cryptography depends on the robustness of the cryptographic algorithm & the size of the key.
We can find the roots of cryptography in Egypt around 4000 years ago. The Egyptians used hieroglyphics - the oldest cryptography technique, for communicating with one another. Then, by 500 BC, the approach got modified by substituting the characters with alphabets through some secret rule. Digital signatures and end-to-end encryption in social networking apps are examples of cryptography. Security professionals and enterprises apply cryptography to deliver confidentiality, integrity, non-repudiation, and authentication.
Advantages And Disadvantages Of Cryptography
Cryptography in cyber security plays a significant role. Since we have gathered insight into what is cryptography, let us explore the various advantages and disadvantages of implementing cryptography in cybersecurity. Advantages:
- It helps to conceal the messages and files at rest or in transit.
- Through cryptography, we can preserve the integrity of the message.
- Digital signatures leverage cryptographic techniques to provide non-repudiation against disputes that emerge in situations when a sender denies that they have created the message.
- Through robust cryptographic algorithms, enterprises can safely keep passwords and other authentication details.
Disadvantages:
- Any glitch in the app (websites) or technologies (database systems) can make the entire approach of using cryptography in cybersecurity null and void.
- Weak cryptographic keys can be a danger to all the data stored within the system.
- The whole cryptographic concept relies heavily on the complexity of mathematical algorithms or systems. Thus, any bug in the algorithm can also nullify the entire concept of using cryptographic techniques.
Cryptographic Algorithms
Cryptographic algorithms are specific sets of codes that determine how the encryption and decryption of a file or message will work through one or more keys. There are two parts to an algorithm. The encryption determines the conversion of human-readable data (plain text) to something unreadable (cipher text) using a key. The other part of the algorithm, i.e., the decryption, converts the unreadable data (cipher text) back to readable form (plain text). Broadly, cryptographic algorithms get classified into two main categories – symmetric and asymmetric. We will discuss these in the types of cryptography section.
Techniques Used For Cryptography
There are numerous techniques used to conceal the data and files through cryptography. These are:
Hashing:
In this technique, a string of data gets converted into a unique string. Irrespective of the form or type of data, hashing will change that data into a unique form & is irreversible. It means you cannot reverse the encryption process through the decryption technique in hashing. Hashing is used in password validation, checking file integrity, message integrity, blockchain technology, and other decentralized digital cryptocurrency systems.
Steganography:
It is another old cryptographic technique to conceal messages or data behind a non-secret text, data, image, or other files. In this technique, the secret message gets blended with the file, hence becoming incredibly challenging to detect. A few decades ago, steganography was not as sophisticated as it has become now. Decades back, kings and queens used slight variations in writing, invisible ink, and other techniques to conceal their messages. With the advent of digitization, security professionals and terrorists hide long texts or other content behind images, video files, etc.
Salting:
It is another cryptographic technique used in hashing to enhance them & become unreadable. The way we add salt improves the taste of the food - the salting technique strengthens the hashing process. We can place the random salt string on either side of the password to change the password's hash string. Such unique hash created by combining the salted passwords defends against various attack vectors such as brute force, dictionary, and hash table attacks.
Features Of Cryptography
Cryptography in cybersecurity plays a significant role in various disciplines. In today's digital-centric world, cryptography is most frequently used in authentication, data communication, information storage, etc. Let us understand the various techniques for cryptography.
- Data confidentiality: This cryptographic feature helps encrypt user data so that unintended users cannot understand what is there in the content.
- Non-repudiation: It is a technique that leverages cryptography to determine that the sender or the receiver cannot deny the fact of the creation or transmission of the information.
- Integrity: This cryptographic feature determines that no one can alter or change the information in transit between the sender and the intended receiver without putting additional data or changing the signature.
- Authentication: It is a feature that helps to authenticate the sender & receivers' digital identities. It also determines the destination and origin of the data so that the data can securely communicate between in the network communication.
Types of Attacks in Cryptography
We can categorize cryptographic attacks into two different types. These are:
Passive Attack:
In this type of cryptographic attack, the attacker can see or reveal the private data in transit or at rest but cannot modify it. Security professionals consider passive attacks more dangerous because the adversary only sees the message and does not perform any action. That makes it difficult for security professionals to identify a breach or attack. Snooping is an example of a passive cryptographic attack where the attacker will reveal the secret message and leak the message content. In this non-aggressive attack, the attacker reads the message and might reveal it to the public. It destroys the confidentiality of the message.
Active Attack:
In this type of cryptographic attack, the attacker can see or reveal the private data in transit or at rest & also modify it. In this attack technique, security professionals can identify an attack if they see a change in the hash value or the data. Cryptography in cyber security plays a significant role in securing from such active attacks. Masquerading as a middleman by using the Man-in-the-Middle (MiTM) attack, brute force, or performing a dictionary attack are well-known cryptographic attack techniques that come under active attack.
- In the MiTM attack, the intruder will sit in the middle between the sender and the receiver. They will alter the information or value right before going to the receiver's end from the sender.
- The brute force attack is like trying all possible combinations (like a permutation-combination technique). It occurs when attackers use computing power to systematically perform feedback loops over each letter of a large password. It is like a trial-and-error method that attempts all possible password combinations.
- Dictionary attacks generate thousands and lacs of phrases, words, and possible pre-matched plaintext as passwords to form a dictionary. Then an algorithm or program will fetch each of these phrases or words from the dictionary file and try to log into the system or user account.
Types Of Cryptography
Now that we have gathered a clear idea of the two different types of attacks in cryptography, let us explore the cryptographic types. In one of the earlier sections, we discussed cryptographic algorithms. Any cryptographic algorithm we encounter comes under any one of the following categories depending on the number of keys or the type of encryption/decryption that is taking place.
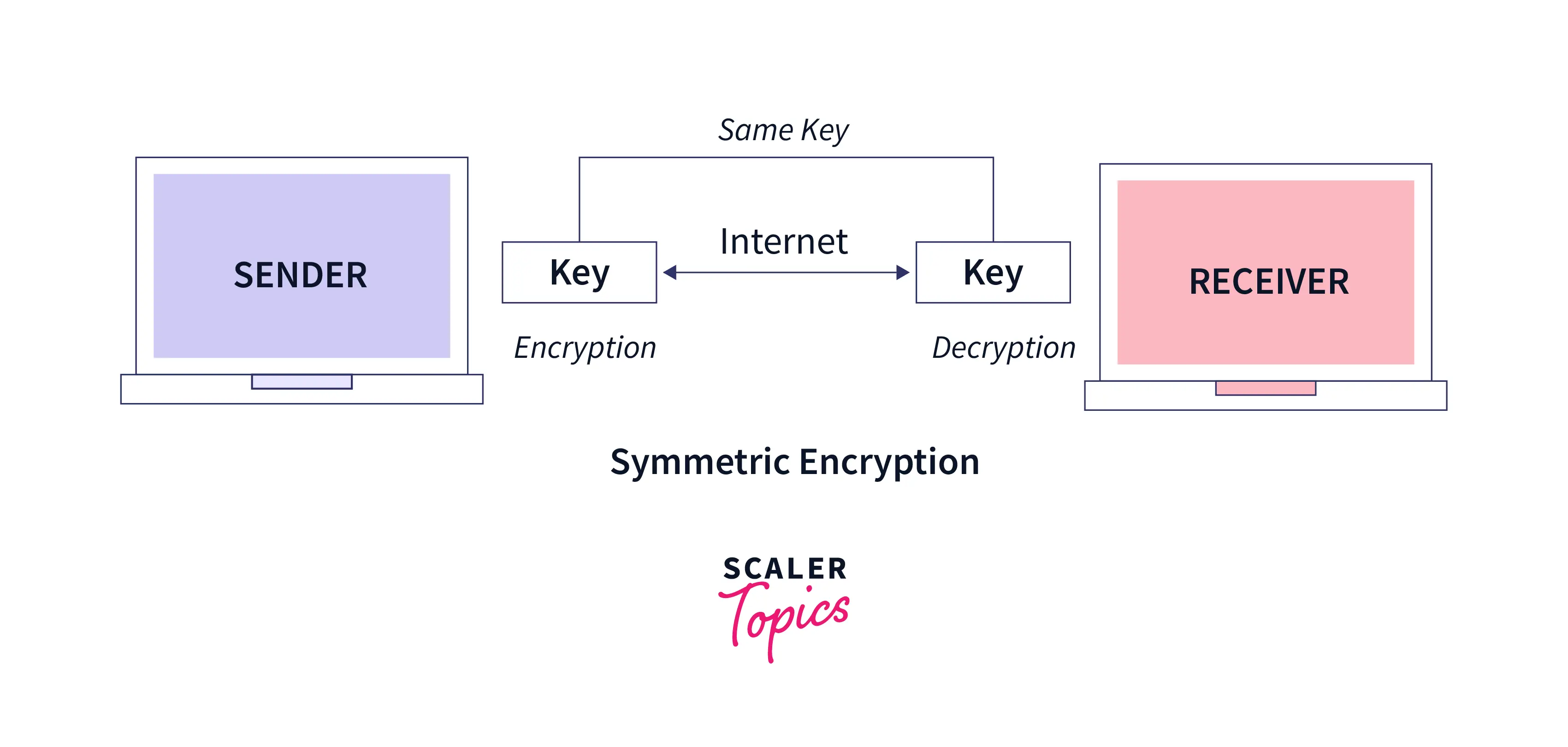
1. Symmetric Encryption:
It is a cryptographic type that utilizes a single key for both encryption and decryption. This cryptographic technique is also known as secret key cryptography. The sender uses the secret or the private key to encrypt the message during encryption (plain text to cipher text). The same secret key is necessary at the receiver's end while decrypting (cipher text to plain text) the message. Since this cryptographic technique uses one encryption key, the sender must share the secret key with the receiver for decryption. AWS, DES, 3DES, Blowfish, etc., are examples of symmetric key cryptography.
2. Hash Function:
Hash functions are mathematical functions used in cryptography to convert numerical input data into another compressed numerical value. The input given to the hash function could vary and be of arbitrary length, while the output will not vary in size (fixed length). A cryptographic hash function will incorporate the message-passing techniques of the hash functions for strengthening security. The hashing function yields variable levels of complexity and difficulty. Security professionals and researchers use hash functions in password security and data/message protection. Bitcoin, which is the largest cryptocurrency, uses a hash function. It is the Secure Hash Algorithm (SHA)-256 cryptographic (256 bits and hence the name) hash function in its algorithm. Again, IOTA is an Internet of Things platform that leverages its cryptographic hash function known as Curl.
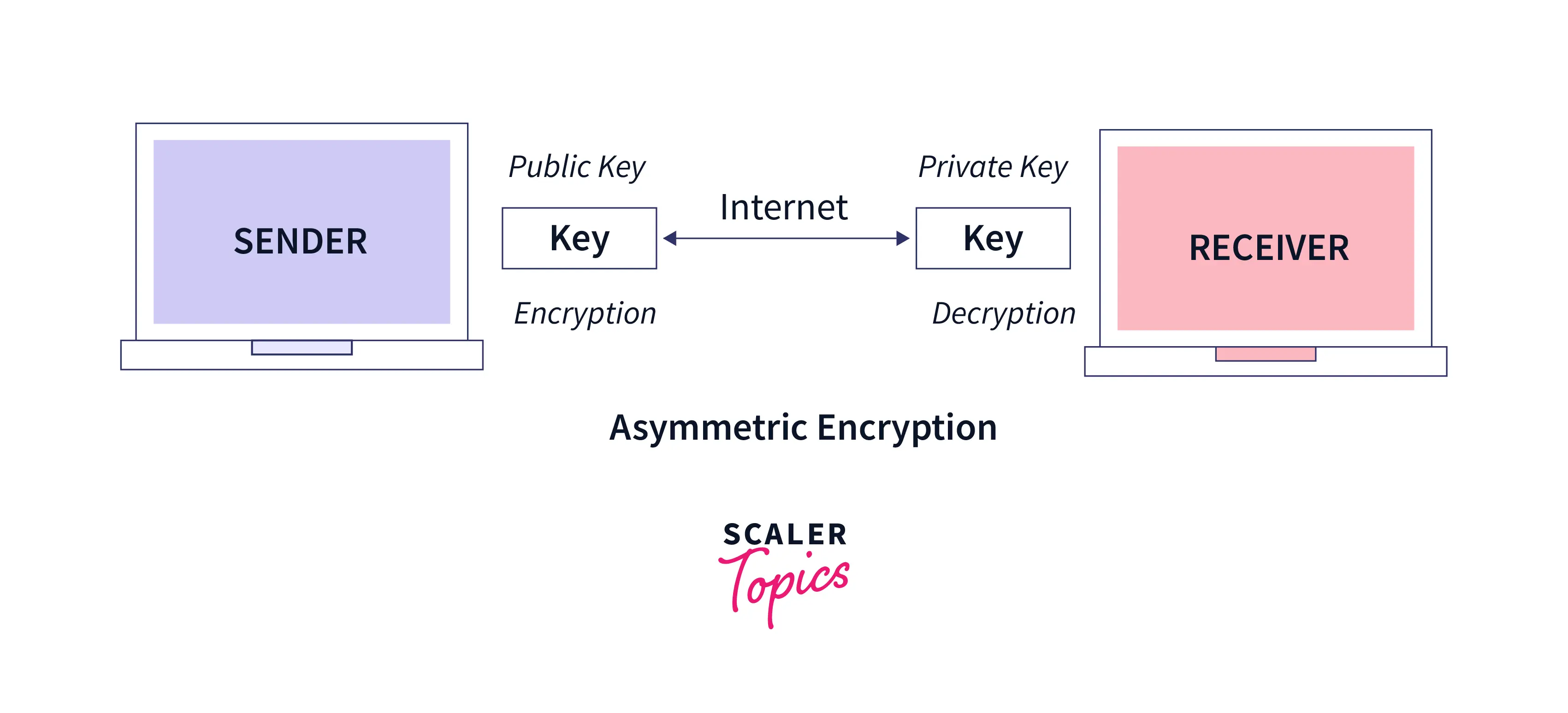
3. Asymmetric Encryption:
It is another popular cryptographic type that employs two different keys (a public key and a private key) to encrypt and decrypt the data. It is also known as public key cryptography. The working procedure is different compared to private/secret key cryptography. In this cryptographic technique, the sender uses a public key to encrypt the message. The public key is distributable, and anyone with the public key can send the message to the receiver's end. The receiver with the private key is the authorized party to decrypt the message. The public key is available to everyone, but the private key does not get disclosed. Some well-known examples of cryptographic algorithms that use asymmetric-key encryption techniques are Rivest Shamir Adleman (RSA) encryption, Elliptical Curve Cryptography (ECC), SSL/TLS protocol, Diffie-Hellman exchange method, Digital Signature Standard (DSS), etc.
Applications of Cryptography –
Let us explore the various applications of cryptography in cybersecurity.
-
Computer passwords: Security professionals, most operating systems, and apps have been using passwords for computer and information security since the earliest days of computing. Passwords are an inevitable part of cybersecurity. Even today, numerous apps, web applications, and security techniques use passwords as an authentication mechanism. For securing these passwords at rest or in transit, cybersecurity professionals & security apps use cryptographic techniques like hashing and encryption techniques.
-
Cryptocurrencies: Cryptocurrencies are another significant domain that extensively uses cryptography. Cryptocurrencies use cryptography for three primary objectives:
- For securing transactions
- To control the creation of more cryptocurrencies, and
- For verifying the transfer of assets Cryptocurrencies mostly rely on public-key cryptographic techniques and algorithms. But most cryptocurrency wallet owners face the problem of losing the private key. There are also chances that the private key gets stolen and the owner loses all the cryptocurrencies that were there in the wallet.
-
Secure web browsing: Encrypting web content is nothing new. Over the past few decades, browser-developing companies implemented cryptography to release data from the client end securely. Even networking protocols that transfer hypertext data, files, web content/pages, and emails use encryption. The popular HTTPS (Hyper-Text Transfer Protocol Secure) & SMTPS (Simple Mail Transfer Protocol Secure) leverages TLS/SSL protocol for encrypting the data. Numerous web browsers come with virtual private networks to prevent data tracking from prying companies and ISPs. These VPN techniques also enforce encryption techniques for concealing the users' activities.
-
Electronic Signatures: An electronic signature or e-sign entitles a person to give approval or consent about the contents of a document. These signatures can legally bind for many uses. E-signatures can be of several forms: an uploaded image of a person's signature, a curved signature with a unique number, the individual's name typed out, or a signature drawn on a tablet/smartphone screen. All the e-signatures leverage cryptography to enforce non-repudiation. Thus the person giving the e-signature cannot deny that the creation of the signature is not his/hers.
-
Authentication: Whether we talk about password-based authentication, passwordless authentication like biometrics, multi-factor authentication, token-based authentication, or authentication through magic links, cryptography plays a significant role in encrypting the data in transit. Even the generating & storing of temporary passcodes (in the form of OTPs, tokens, or magic links) use cryptographic algorithms.
-
Digital currencies: The electronic version of currencies is dominating in almost every country. Various digital wallets and online payment apps popped up to send and receive money over the internet. All these secure transmissions of digital currencies through e-wallets and apps leverage cryptographic algorithms.
-
End-to-end encryption: End-to-end encryption is a method of secure communication. It affirms that only the sender and the intended recipient can read the data. It prevents third parties from accessing the data & acts as a gold standard for protecting communication. It assures that when data travels to the destination, no one (internet service provider (ISP), cybercriminal, application service provider, or any other service) can read or tamper with the data. End-to-end renders data confidentiality, integrity, and non-repudiation of data through cryptographic techniques.
Conclusion
- In this article, we have gathered a crisp understanding of what is cryptography & the use of cryptography in cyber security.
- Then we understood the advantages and disadvantages of cryptography.
- We also encountered what cryptographic algorithms are & the various techniques used by cryptography in cyber security.
- Next, we have come across the features of cryptography in cyber security and cryptographic types.
- We have also comprehended the two major categories of cryptographic attacks.
- Lastly, we have seen the various applications of cryptography in different areas of IT.
