Difference between Hashing and Encryption
Overview
This article will discuss what is the difference between encryption and hashing. These are two different ways of protecting information and understanding their distinctions is important for cybersecurity and data privacy. We will also elaborate on hashing vs. encryption here.
What is Hashing?
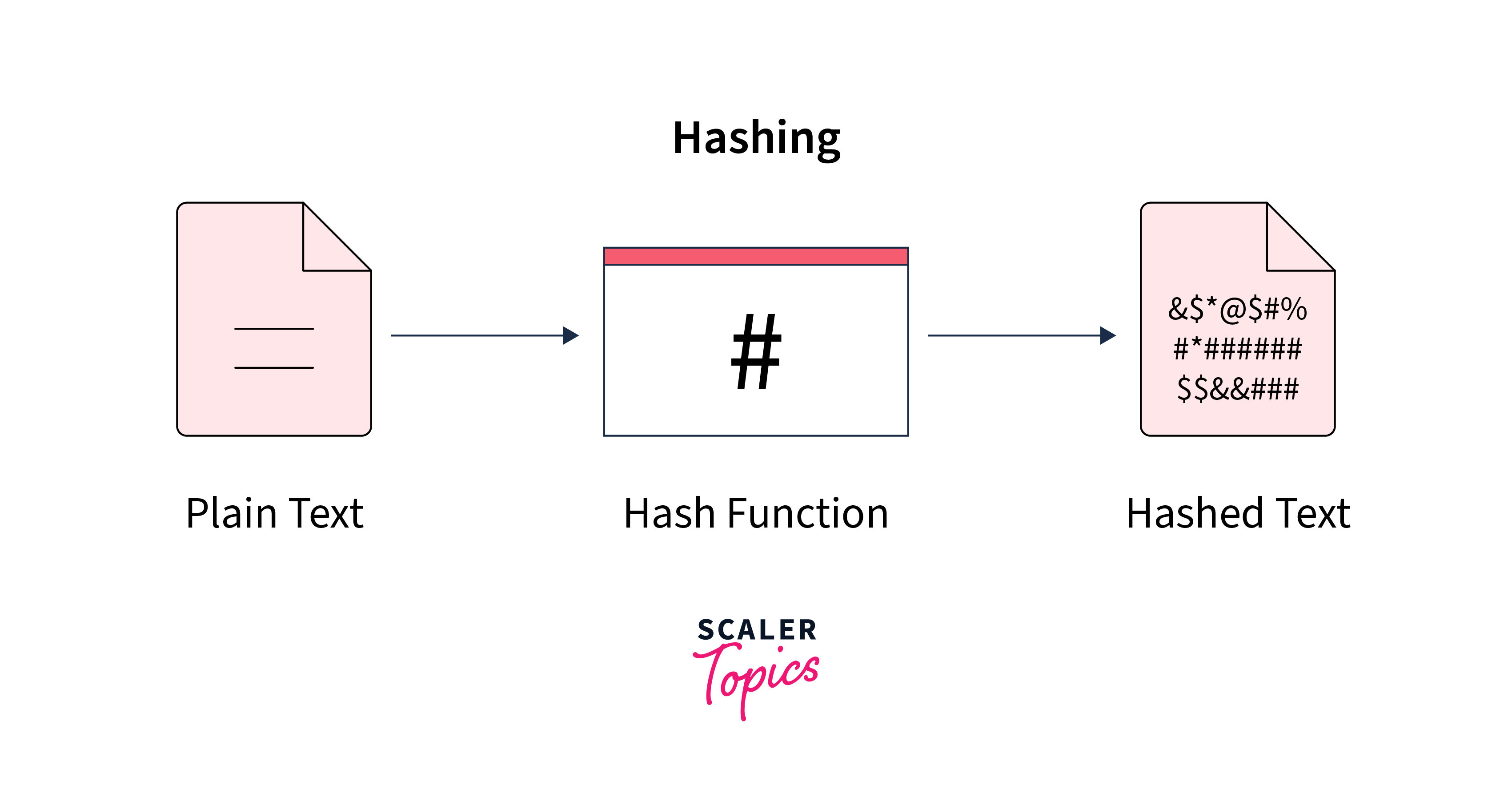
Hashing is like a magic trick for data. It takes any kind of information, whether it's a password, a message, or a file, and turns it into a fixed-size string of characters, usually in a jumbled-up way. This output is called a hash value or simply a hash. The cool thing about hashing is that even a tiny change in the input will completely change the hash. So, you can think of it as a fingerprint for data. It's used to verify if data has been tampered with, but you can't turn the hash back into the original data.
What is Encryption?
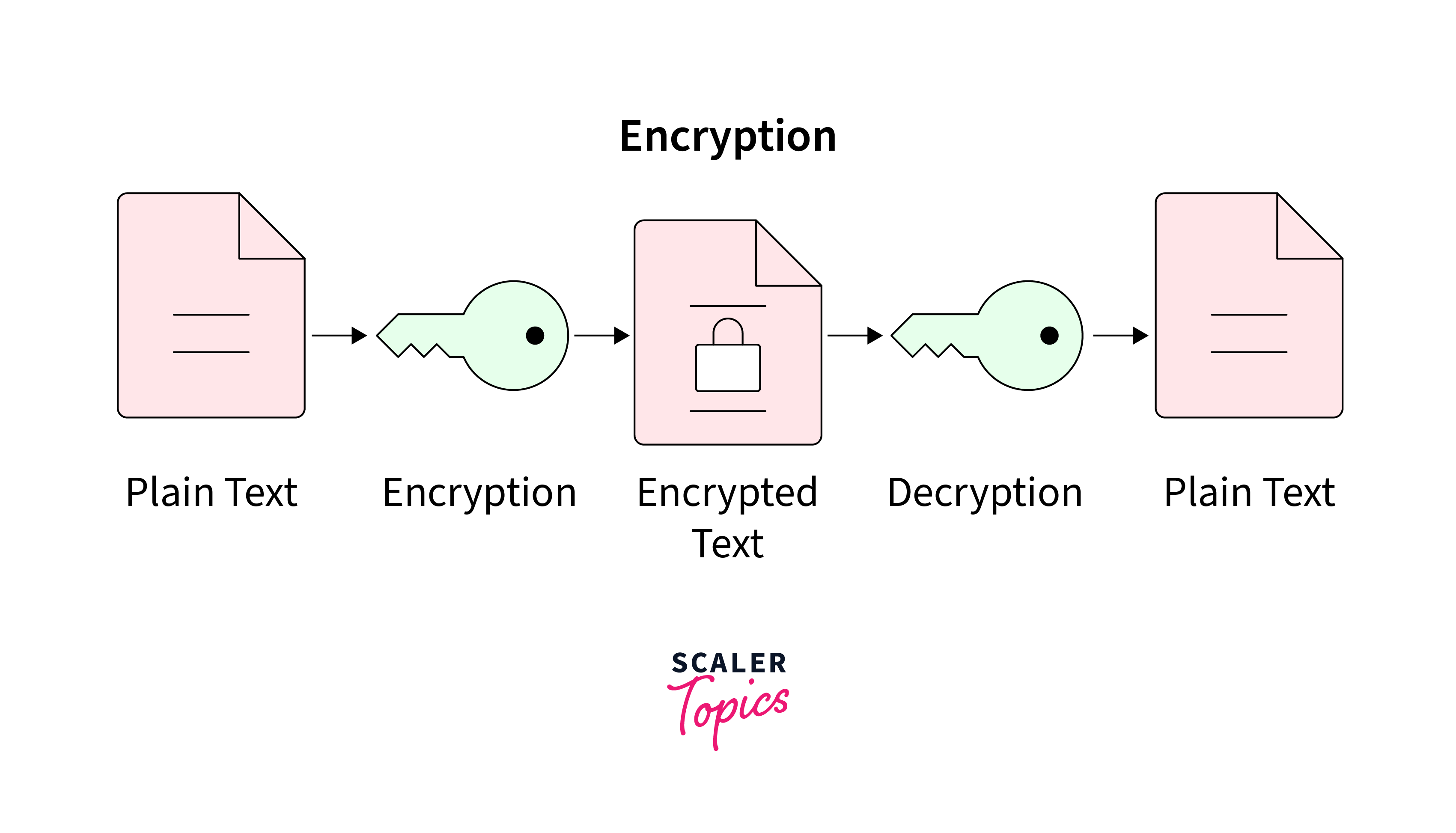
Encryption is like putting your data in a secret code. It takes your information and scrambles it using an encryption key, turning it into unreadable gibberish. To read it again, you need the right key to unscramble it. Encryption is often used to protect sensitive data during transmission (like when you send a password over the internet) or when it's stored on a device (like your smartphone).
Till now you have understood hashing vs. encryption. From here on you will understand what is the difference between encryption and hashing, so let's find out.
Common Encryption and Hashing Algorithms
There are three types of algorithms.
Symmetric Encryption Algorithms
-
Advanced Encryption Standard (AES):
It is a widely adopted and highly secure symmetric encryption algorithm used to protect sensitive data. -
Blowfish:
It is a symmetric key block cipher known for its efficiency and security in encrypting data, especially in older applications. -
Twofish:
It is a symmetric key block cipher that offers strong security and versatility in data encryption, making it suitable for various applications. -
Rivest Cipher (RC4):
It is a widely-used stream cipher known for its simplicity and speed, although it has been largely replaced by more secure encryption methods due to vulnerabilities. -
Data Encryption Standard (DES):
It is an early symmetric key encryption algorithm that was widely used for secure data transmission but is now considered insecure due to its vulnerability to modern attacks, and it has been largely replaced by more advanced encryption standards like AES.
Asymmetric Encryption Algorithms
-
Elliptic Curve Digital Signature Algorithm (ECDSA):
It is a widely used asymmetric cryptography technique that provides secure digital signatures, making it valuable for authentication and data integrity verification in various applications, including digital certificates and cryptocurrencies. -
Rivest-Shamir-Adleman (RSA):
It is a widely-used asymmetric encryption algorithm that enables secure communication and data encryption by utilizing a pair of keys; an encryption for a private key and an encryption for a public key. -
Diffie-Hellman:
It is a key exchange algorithm that allows two parties to securely establish a shared secret key over an insecure communication channel, facilitating secure communication and encryption between them. -
Pretty Good Privacy (PGP):
It is a data encryption and decryption program that provides cryptographic privacy and authentication for secure communication. It is commonly used for encrypting emails, files, and other forms of digital communication to ensure confidentiality and data integrity.
Hashing Algorithms
-
Message Digest Algorithm (MD5):
It is a widely used cryptographic hash function that generates a fixed-size 128-bit hash value from input data. While it was once commonly used for data integrity and password hashing, it is now considered weak and insecure due to vulnerabilities, and it is generally not recommended for security-sensitive applications. -
Secure Hashing Algorithm (SHA-1, SHA-2, SHA-3):
It is a family which includes various versions (SHA-1, SHA-2, and SHA-3) used to generate fixed-size hash values, with SHA-2 and SHA-3 being the current secure choices for cryptographic applications. -
WHIRLPOOL:
It is a strong cryptographic hash function that generates a fixed-size hash value used for data integrity verification and digital signatures. -
TIGER:
It is a cryptographic hash function designed for data integrity and checksum purposes. -
Cyclical Reduction Check (CRC32):
It is a simple and fast checksum algorithm often used for error-checking and data integrity verification in networking and data storage applications.
Hashing and Encryption Use Cases
These use cases will help you understand hashing vs. encryption practically.
| Use Case | Hashing | Encryption |
|---|---|---|
| Data Integrity Verification | Yes | No |
| Password Storage | Yes (with salting) | No |
| Secure Communication | No | Yes |
| Data Privacy | No | Yes |
| File Integrity Check | Yes | Yes |
Conclusion
- This article discusses what is the difference between encryption and hashing.
- We have talked about hashing vs encryption as well.
- Hashing turns data into a fixed-size string (hash), mainly for verification.
- Encryption uses a key to scramble data for security during transmission or storage.
- With symmetric encryption, both encrypting and decrypting are done with the same key.
- Asymmetric encryption uses a pair of keys: public for encryption and private for decryption.
- Different algorithms offer varying levels of security.
- Hashing is used for data integrity, while encryption is for privacy and security.
