Why is a VPC Created?
Overview
Have you ever thought about why a VPC was created? AWS Virtual Private Cloud (VPC) was established to create a dedicated and isolated network environment within Amazon Web Services. It ensures enhanced security by allowing users to define their own networking configuration, control inbound and outbound traffic through security groups and network ACLs, and connect to on-premises resources via VPN or Direct Connect. This customizable infrastructure enables seamless deployment of AWS services while safeguarding data and applications from external threats. VPCs are pivotal for building scalable, resilient, and private cloud architectures that align with specific business requirements within the AWS ecosystem. This article will cover features and, the creation of AWS VPC.
What is Amazon VPC?
The answer to the question "What is VPC in Cloud Computing in AWS?" is Amazon Virtual Private Cloud (Amazon VPC) is a fundamental service within Amazon Web Services (AWS) that allows users to create and manage isolated networks within the AWS cloud environment. It enables users to have complete control over their network architecture, including the selection of IP addresses, subnets, routing tables, and network gateways. This level of customization allows businesses to create secure and private environments, enhancing security and control over their cloud resources.
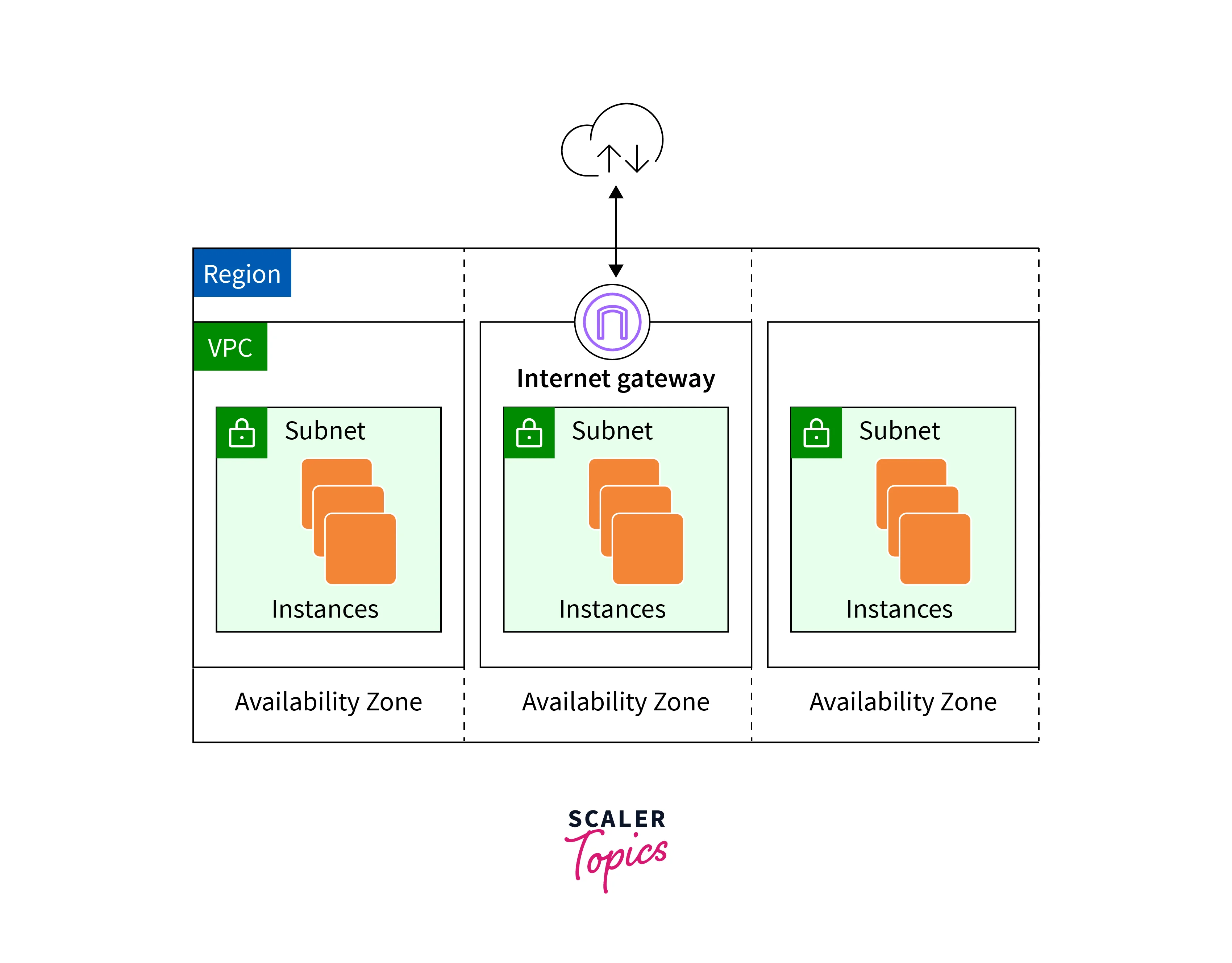
Components of Amazon VPC
Virtual Private Cloud (VPC):
A VPC is a logically isolated section of the AWS cloud where users can launch resources like Amazon EC2 instances, databases, and more. It allows users to define their IP address range (CIDR block), subnets, route tables, and network gateways.
CIDR Block (Classless Inter-Domain Routing):
The CIDR block is a notation used to specify a range of IP addresses. It's defined in the form of an IP address followed by a slash and a number (e.g., 10.0.0.0/16), indicating the number of significant bits in the network prefix.
Subnet:
Subnets are segments of a VPC's IP address range. They are created within an Availability Zone (AZ) and can be public or private. Public subnets have direct internet access, while private subnets do not. Subnets enable the isolation of resources and the implementation of network security policies.
Route Table:
A route table is a set of rules that determine where network traffic is directed within a VPC. It specifies the routes for traffic between subnets, the internet, and other resources. Route tables are associated with subnets and control how traffic flows between them.
Internet Gateway:
An internet gateway allows resources within a VPC's public subnet to access the internet and be accessed by internet users. It acts as a gateway between the VPC and the internet, facilitating communication.
NAT Gateway (Network Address Translation):
A NAT gateway enables instances in private subnets to access the internet while preventing direct inbound traffic from reaching them. It provides a controlled point of access for outgoing traffic, enhancing security for private resources.
DNS Hostname:
VPCs come with a default Domain Name System (DNS) hostname resolution enabled. This means that instances within the VPC can have DNS hostnames automatically assigned, allowing for easier resource identification and communication.
Security Groups:
Security groups act as virtual firewalls at the instance level. They control inbound and outbound traffic by specifying rules that determine what traffic is allowed or denied. Security groups enhance network security and isolate instances from unauthorized access.
Network Access Control Lists (NACLs):
NACLs operate at the subnet level and control inbound and outbound traffic based on rules defined by the user. They add a layer of security to the VPC by allowing fine-grained control over network traffic.
VPC Peering:
VPC peering enables direct communication between VPCs, allowing resources in different VPCs to communicate privately using internal IP addresses. This is useful for scenarios where different application components reside in separate VPCs.
VPN Connections:
Amazon VPC supports Virtual Private Network (VPN) connections, allowing users to establish secure encrypted connections between their on-premises networks and their VPCs. This ensures a secure and private connection to resources in the cloud.
VPC Endpoints:
VPC endpoints enable private connectivity to AWS services without using public IPs, enhancing security and reducing exposure to the public internet.
You can learn more about Amazon VPC by Clicking Here.
Features
Here's a detailed exploration of the key features of Amazon VPC:
Isolation and Segmentation:
- Amazon VPC enables the creation of isolated networks, providing a secure and isolated environment for resources to operate.
- Users can segment their VPC into multiple subnets, dividing their network into smaller segments to better organize and control resources.
IP Address Control:
- Users have granular control over IP address assignment within their VPC.
- VPCs are defined by IP address ranges, allowing users to define private IP address spaces.
- Elastic IP addresses enable static public IP addresses to be associated with instances, ensuring consistent addressing even during instance restarts.
Internet and Private Connectivity:
- Amazon VPC offers the flexibility to configure both internet-facing and private subnets within a VPC.
- Internet Gateway acts as a connection point for instances in the VPC to access the internet, while keeping them protected from unsolicited inbound traffic.
- Network Address Translation (NAT) Gateway/Instance allows private instances to access the internet for software updates or patches while maintaining a layer of security.
Security:
- Security Groups serve as virtual firewalls, for instance, controlling both inbound and outbound traffic.
- Network Access Control Lists (NACLs) provide an additional layer of security by controlling traffic at the subnet level, allowing more granular control over traffic flow.
- VPC Peering allows secure communication between VPCs using private IP addresses without the need for internet gateways or VPN connections.
VPN and Direct Connect:
- Amazon VPC supports encrypted VPN connections, allowing secure communication between on-premises networks and VPCs.
- AWS Direct Connect provides dedicated network connections from on-premises to VPCs, offering increased data transfer speeds and enhanced security.
Elastic Load Balancing:
- VPC seamlessly integrates with Elastic Load Balancing (ELB), distributing incoming traffic across multiple instances to ensure high availability and fault tolerance.
Network Flow Logging:
- Amazon VPC Flow Logs capture information about IP traffic going to and from network interfaces within the VPC.
- Flow logs assist in monitoring and troubleshooting network issues, aiding in compliance and security analysis.
VPC Endpoints:
- VPC Endpoints enable secure connections between VPCs and AWS services without traversing the public internet.
- This feature enhances security by reducing exposure to public networks while ensuring efficient communication with AWS services.
Peering and Transit Gateway:
- Transit Gateway simplifies network architecture by allowing centralized management of connectivity between VPCs and on-premises networks.
- VPC Peering enables direct communication between VPCs, creating a mesh of interconnected networks for various application scenarios.
Hybrid Cloud Capabilities:
- Amazon VPC facilitates hybrid cloud setups, enabling seamless integration between on-premises infrastructure and cloud resources.
- Users can extend their existing data centers to the cloud while maintaining control over network traffic.
Resource Placement Control:
- Users can control the placement of instances within specific subnets or availability zones, ensuring high availability and fault tolerance for critical workloads.
Custom Route Tables:
- Route tables enable users to define custom routing rules for their VPC traffic, allowing for efficient control over how traffic flows within the network.
Global Accelerator Integration:
- Amazon VPC integrates with AWS Global Accelerator, a service that improves the availability and performance of applications by routing traffic over AWS's global network infrastructure.
Steps to Create and Verify Your VPC
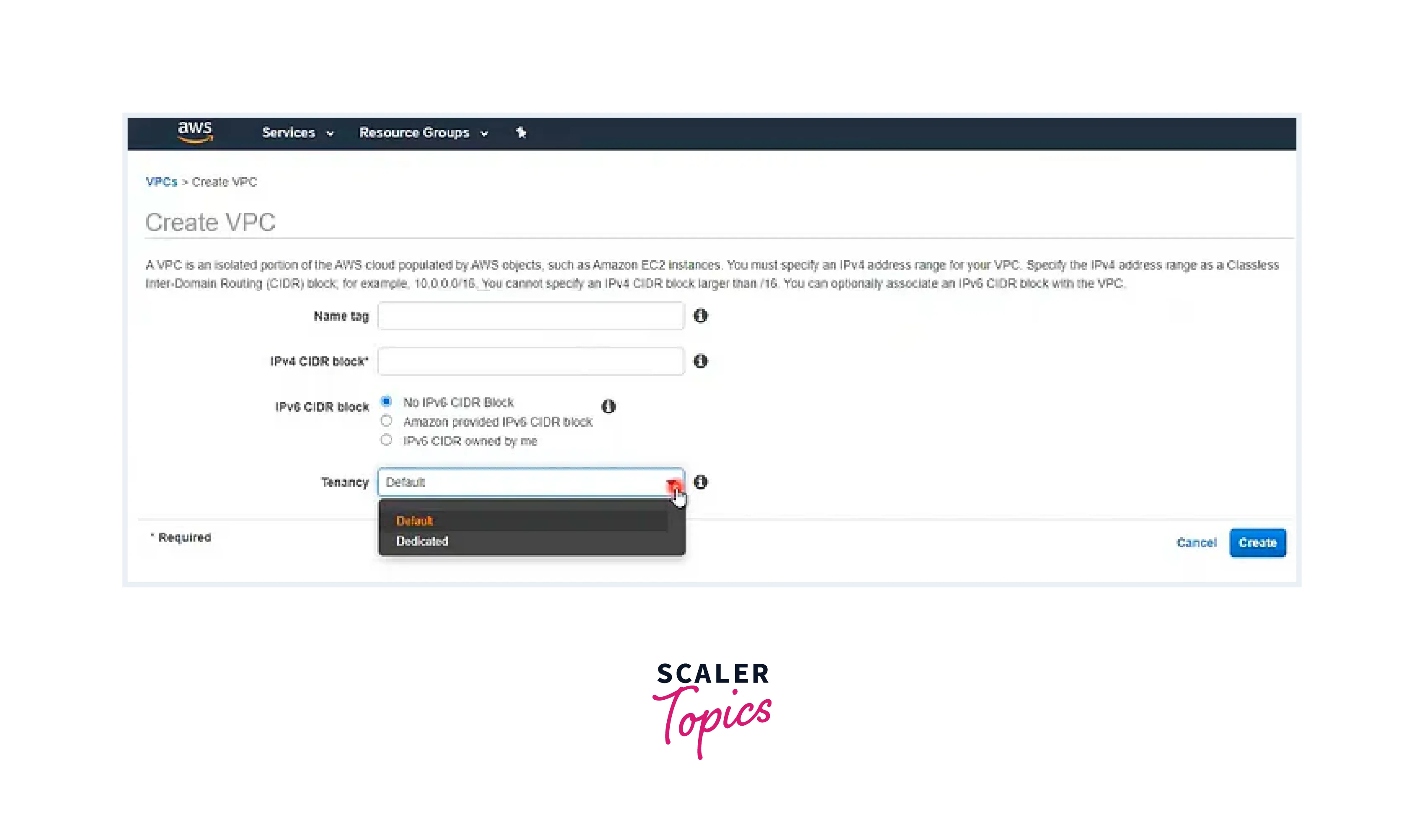
Step - 1: VPC Creation
- Begin by accessing the AWS Console and logging in to your account.
- Generate a new Virtual Private Cloud (VPC) with a valid Classless Inter-Domain Routing (CIDR) range and assign a meaningful name to it.
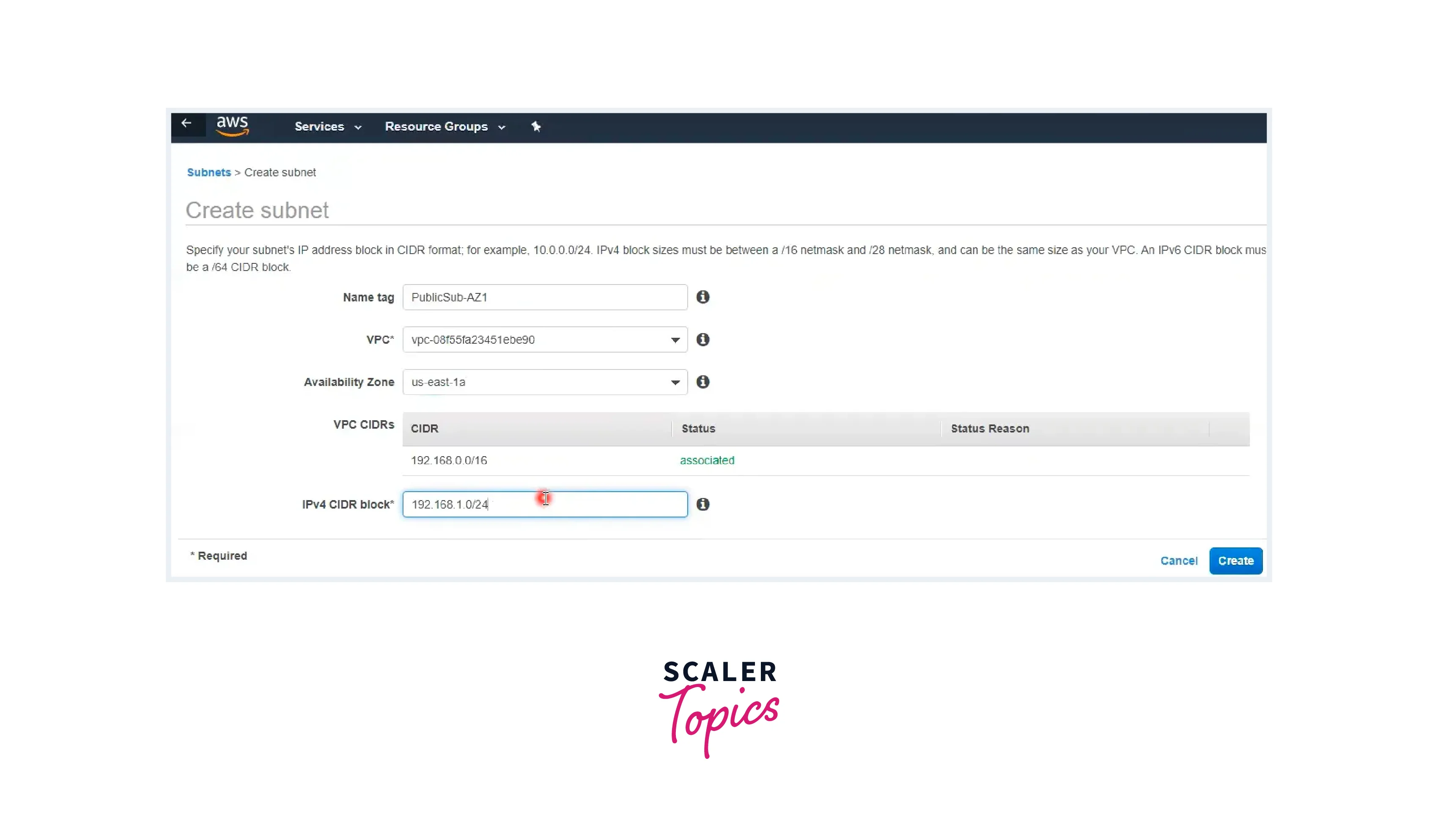
Step - 2: Formation of Public and Private Subnets
- Navigate to the Subnet section and select the option to create a new subnet.
- For Public Subnet 1 and Public Subnet 2, provide relevant names and associate them with the previously created VPC.
- Specify a suitable IPv4 CIDR block as the subnet range.
- Repeat the above steps for Private Subnet 1 and Private Subnet 2.
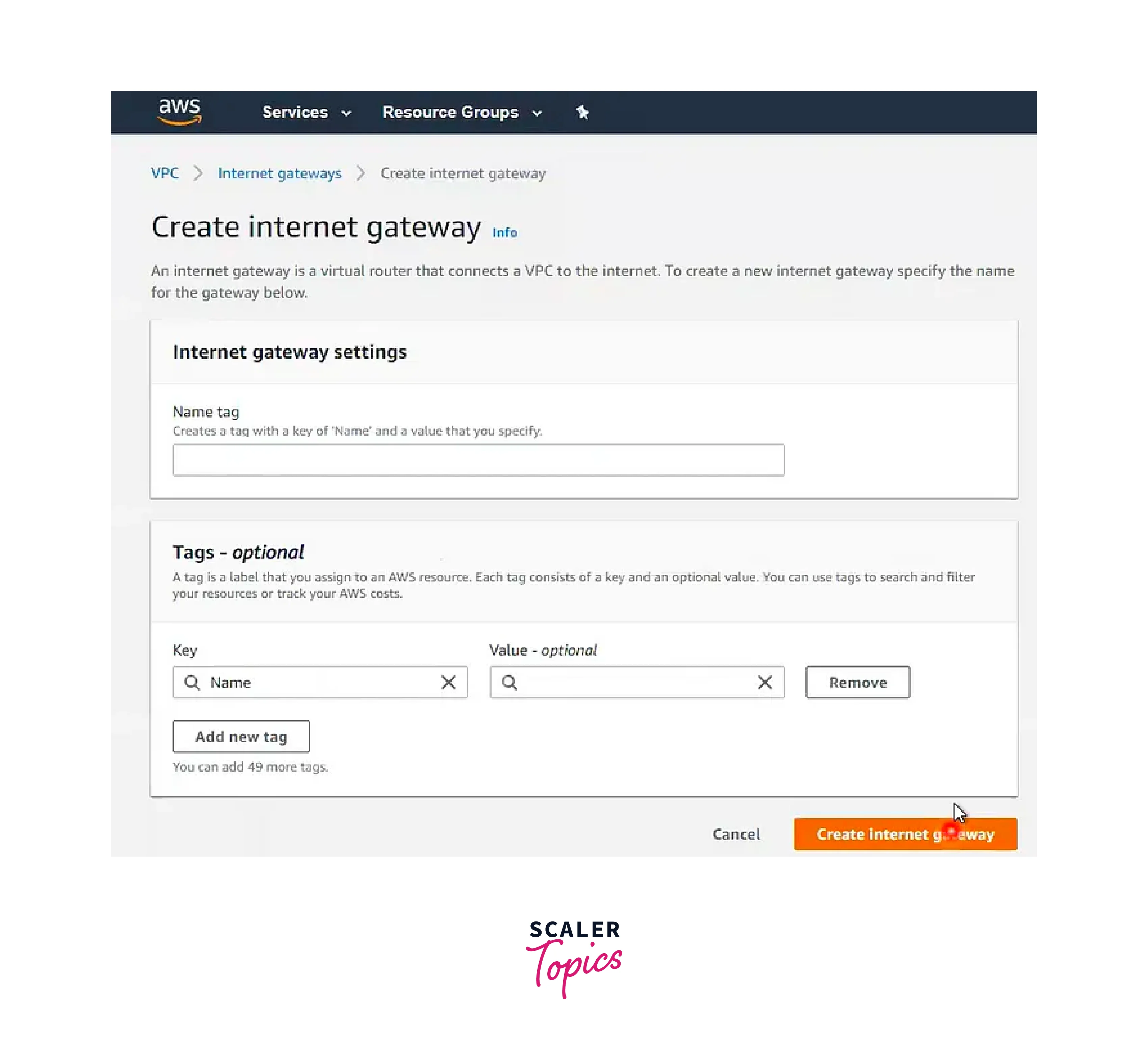
Step - 3: Establishment of an Internet Gateway (IGW) and its Attachment to the VPC
- Create an Internet Gateway (IGW) and wait for its completion.
- Attach the IGW to the VPC to enable internet connectivity.
Step - 4: Crafting Public and Private Route Tables
Understanding Route Table Concepts:
- Main Route Table:
This is automatically associated with your VPC and governs routing for subnets not explicitly connected to other route tables. - Custom Route Table:
Users can create their route table for VPC-specific routing needs. - Edge Association:
This type of route table is employed for directing inbound VPC traffic to an appliance. It's linked with an internet gateway or virtual private gateway, with the appliance's network interface specified as the traffic target. - Route Table Association:
This involves associating a route table with a subnet, internet gateway, or virtual private gateway. - Subnet Route Table:
This route table is linked to a specific subnet. - Gateway Route Table:
This route table is associated with an internet gateway or virtual private gateway. - Local Gateway Route Table:
This type is connected to an Outposts local gateway. - Destination:
The designated range of IP addresses where traffic should be directed (destination CIDR). - Target:
The gateway, network interface, or connection through which the destination traffic will be directed. - Local Route:
This is the default route for communication within the VPC.
Generate a new route table within the same VPC. Ensuring the accurate VPC selection and tagging.
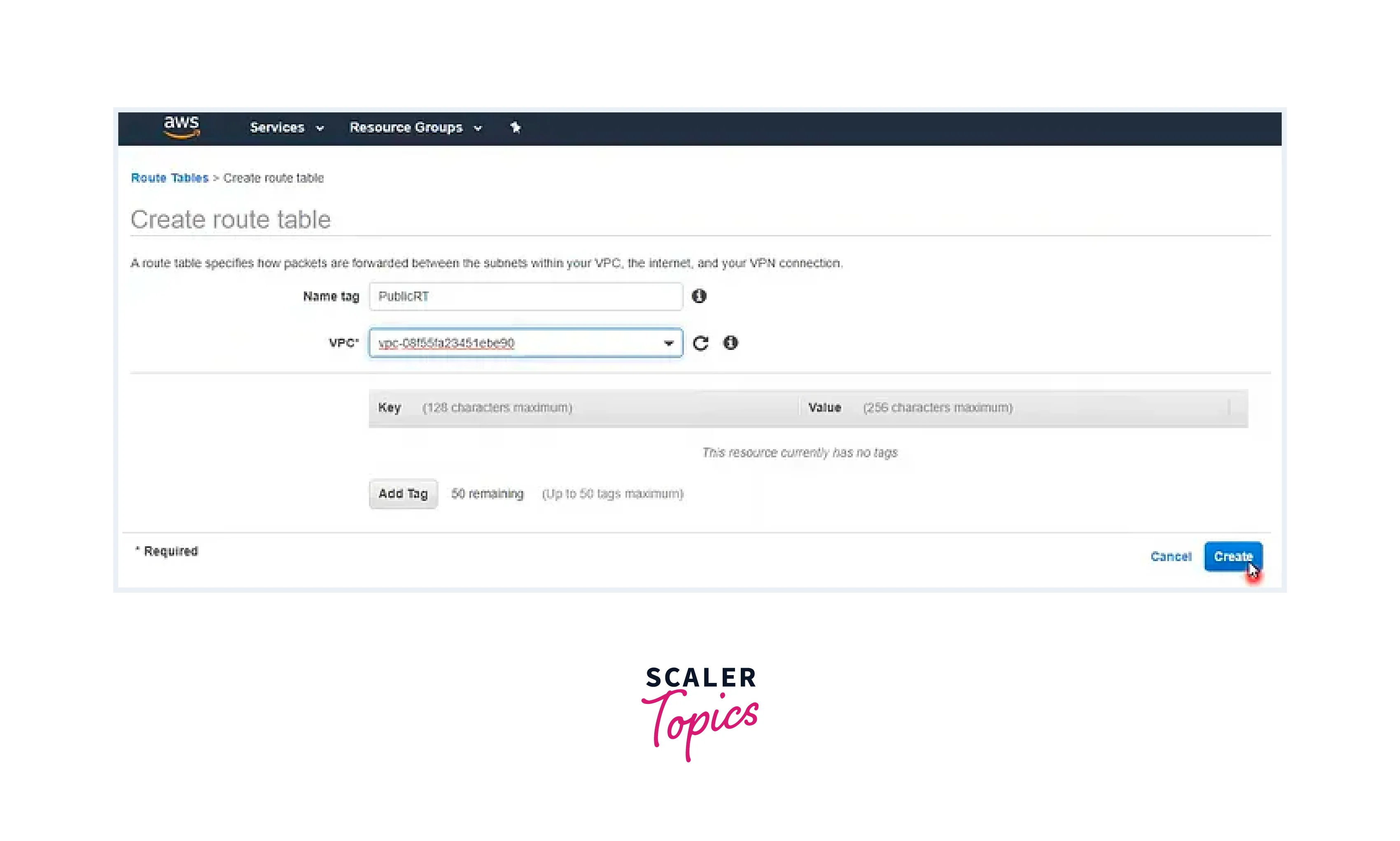
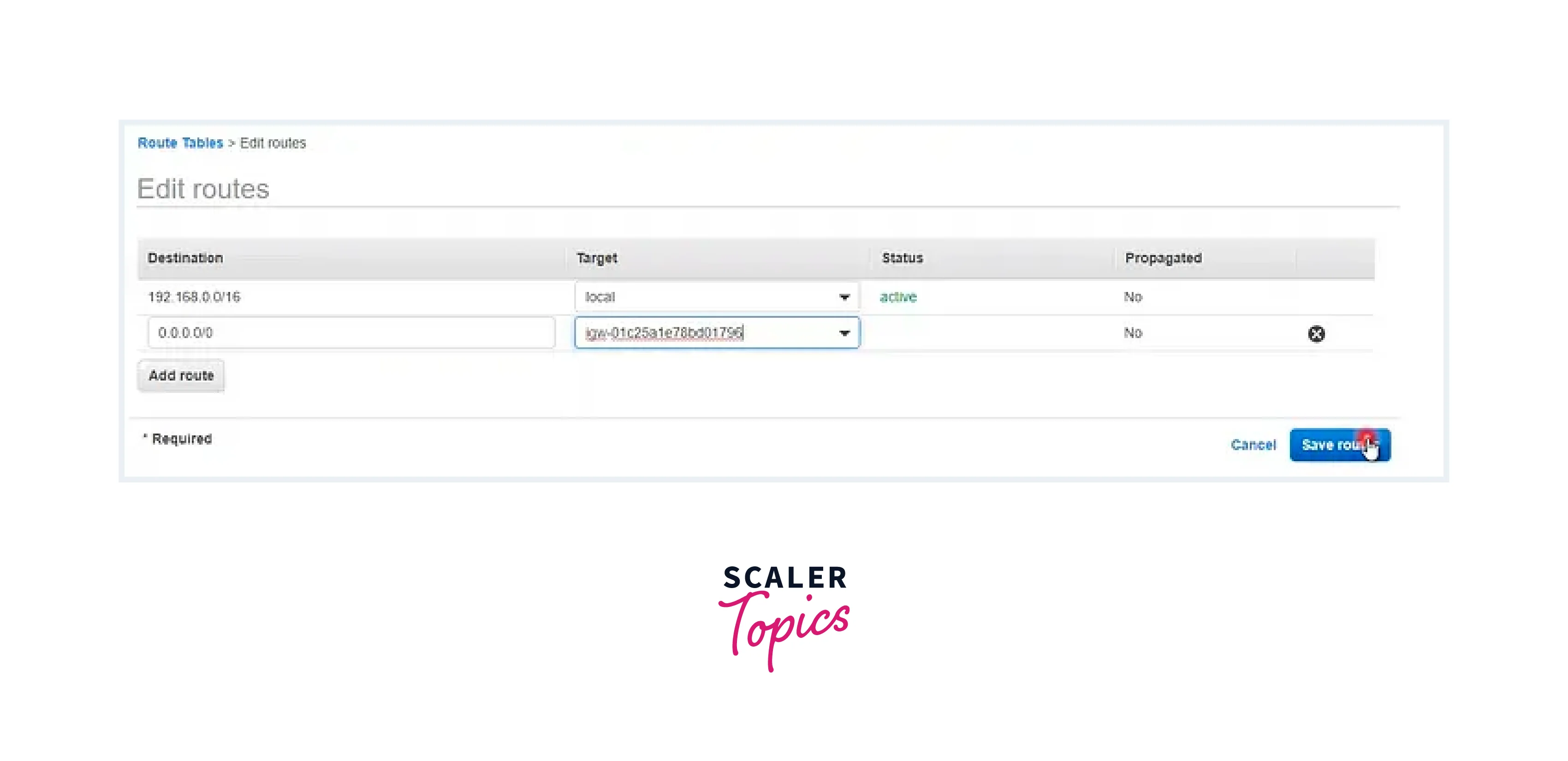
Step - 5: Integrating IGW into the Public Route Table (0.0.0.0/0)
- Access the Public route table and select the edit option.
- Append a route for 0.0.0.0/0.
- Choose the Internet Gateway from the Target dropdown.
- Save the altered route settings.
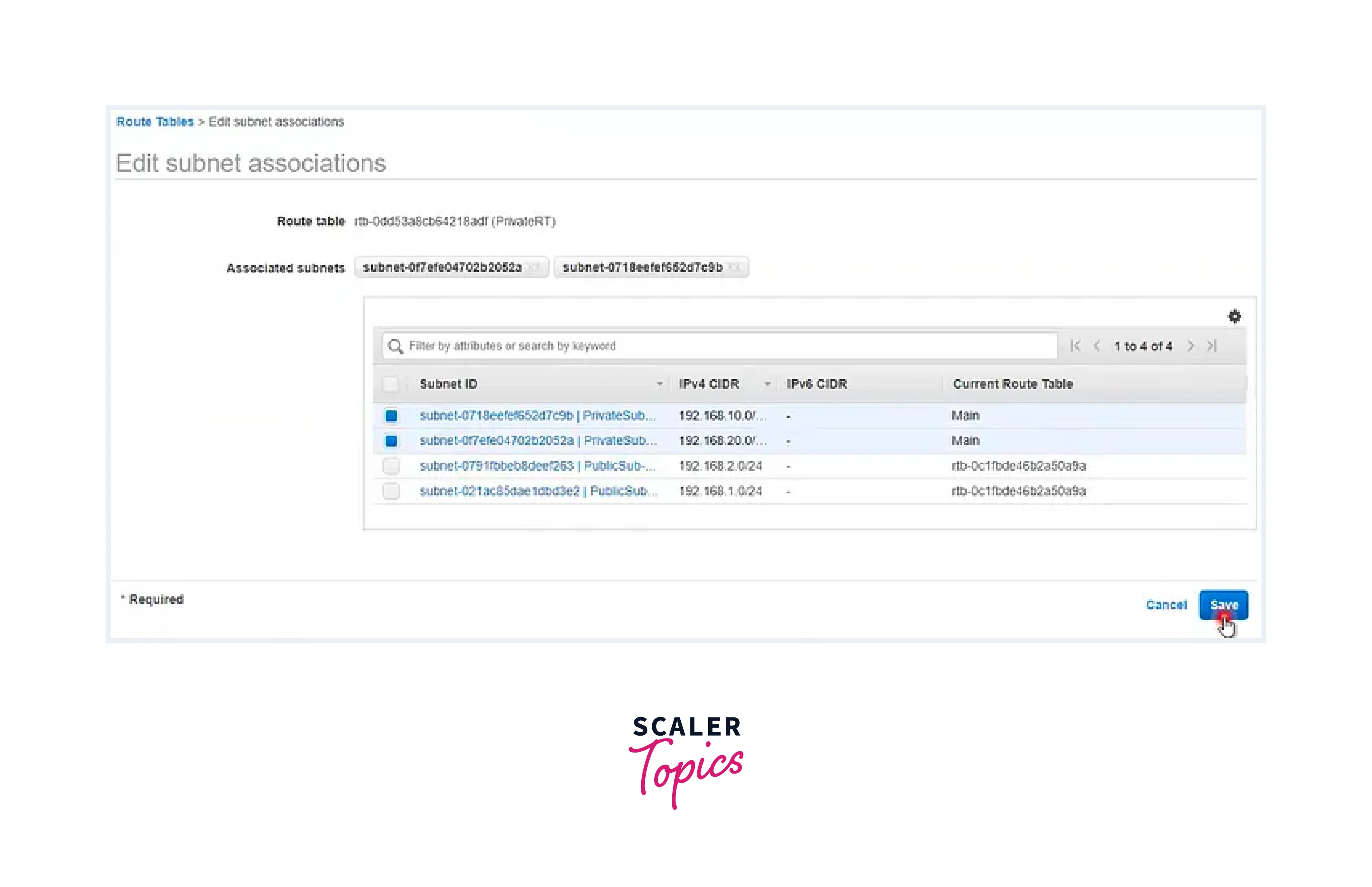
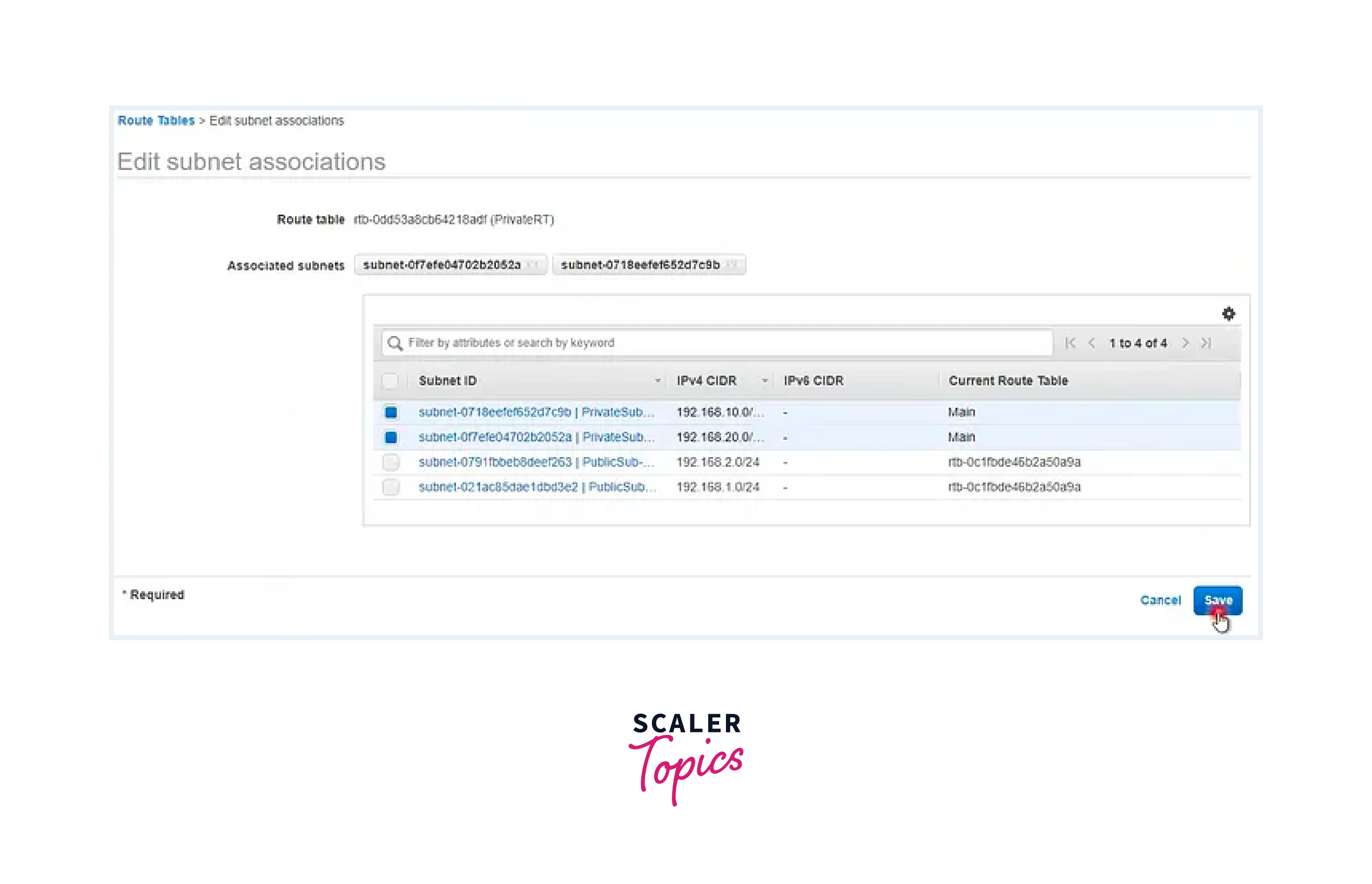
Step - 6: Inclusion of Public Subnets (1a & 1b) into the Route Table
- Edit the Subnet Association.
- Tick the box associated with the Public Subnet.
- Save the changes to the association.
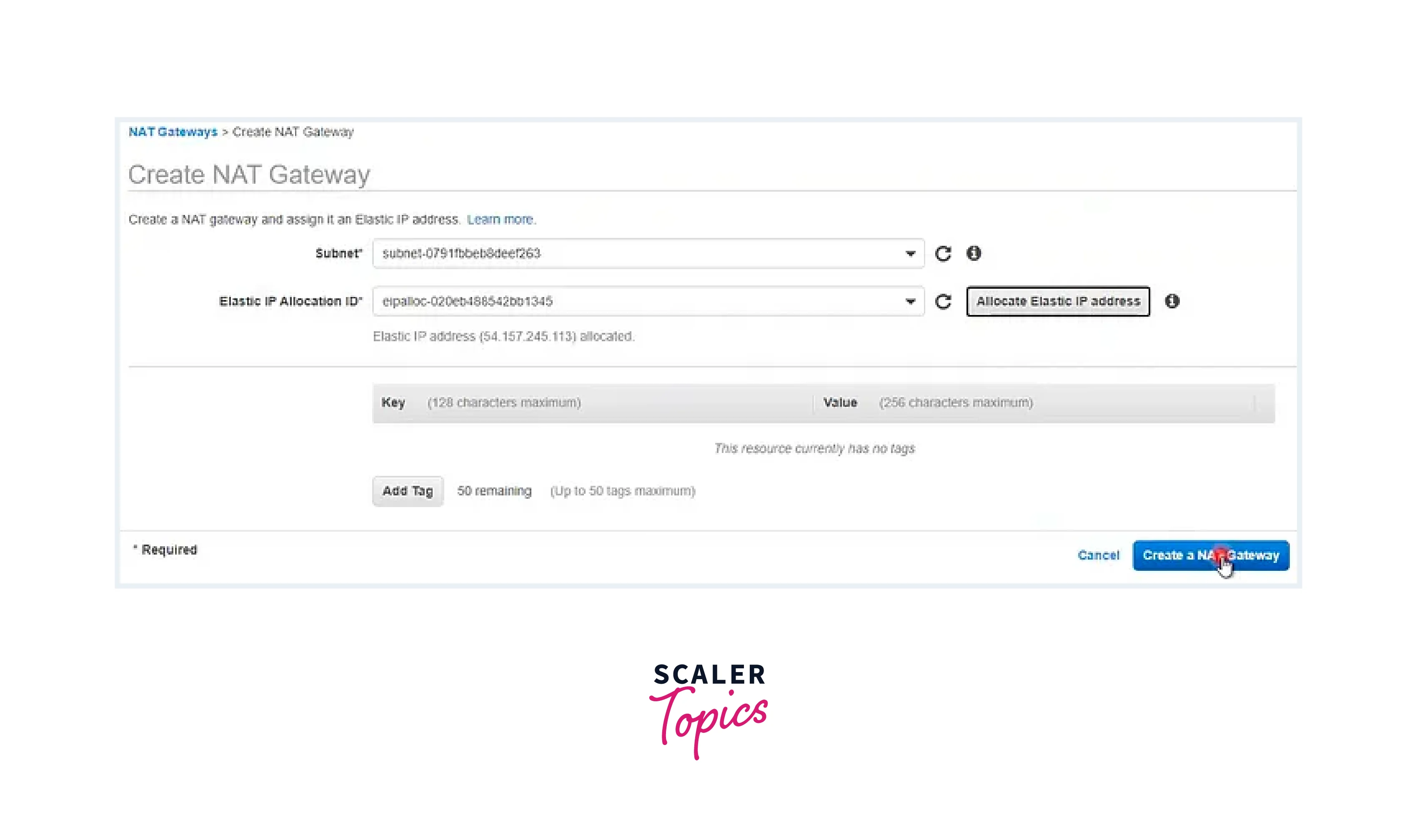
Step - 7: Creation of a NAT Gateway in the Public Subnet
- Choose a Public Subnet for the NAT Gateway.
- Generate a new Elastic IP address and link it with the NAT Gateway.
- Initiate the creation of the NAT Gateway.
Step - 8: Addition of NAT Gateway to the Private Route Table
- Access the Private route table and choose the edit option.
- Append a route for 0.0.0.0/0.
- Select the NAT Gateway from the Target dropdown.
- Save the updated route configuration.
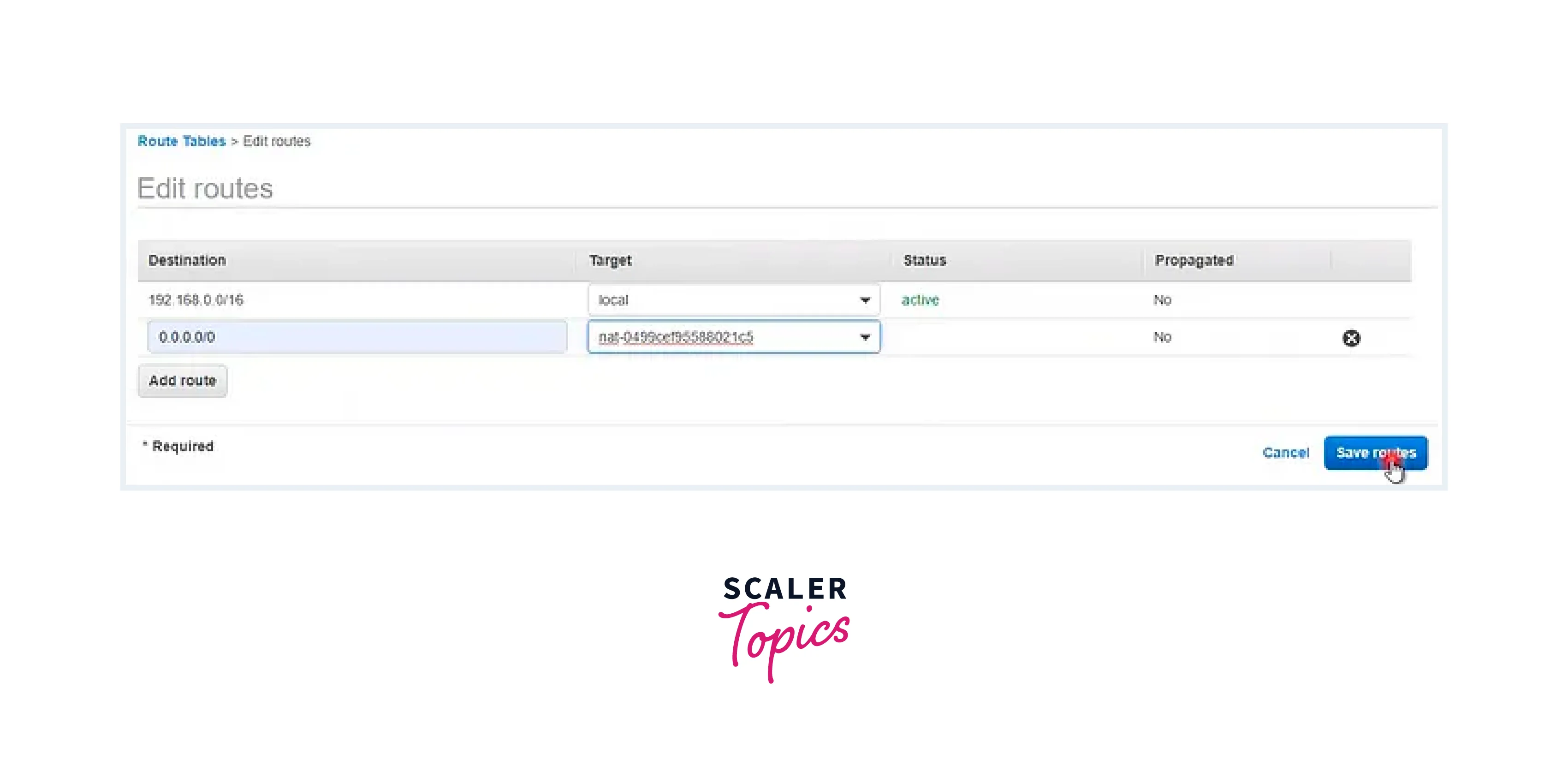
Step - 9: Integration of Private Subnet into the Private Route Table
- Edit the Subnet Association.
- Mark the checkbox linked to the Private Subnet.
- Save the changes to the association.
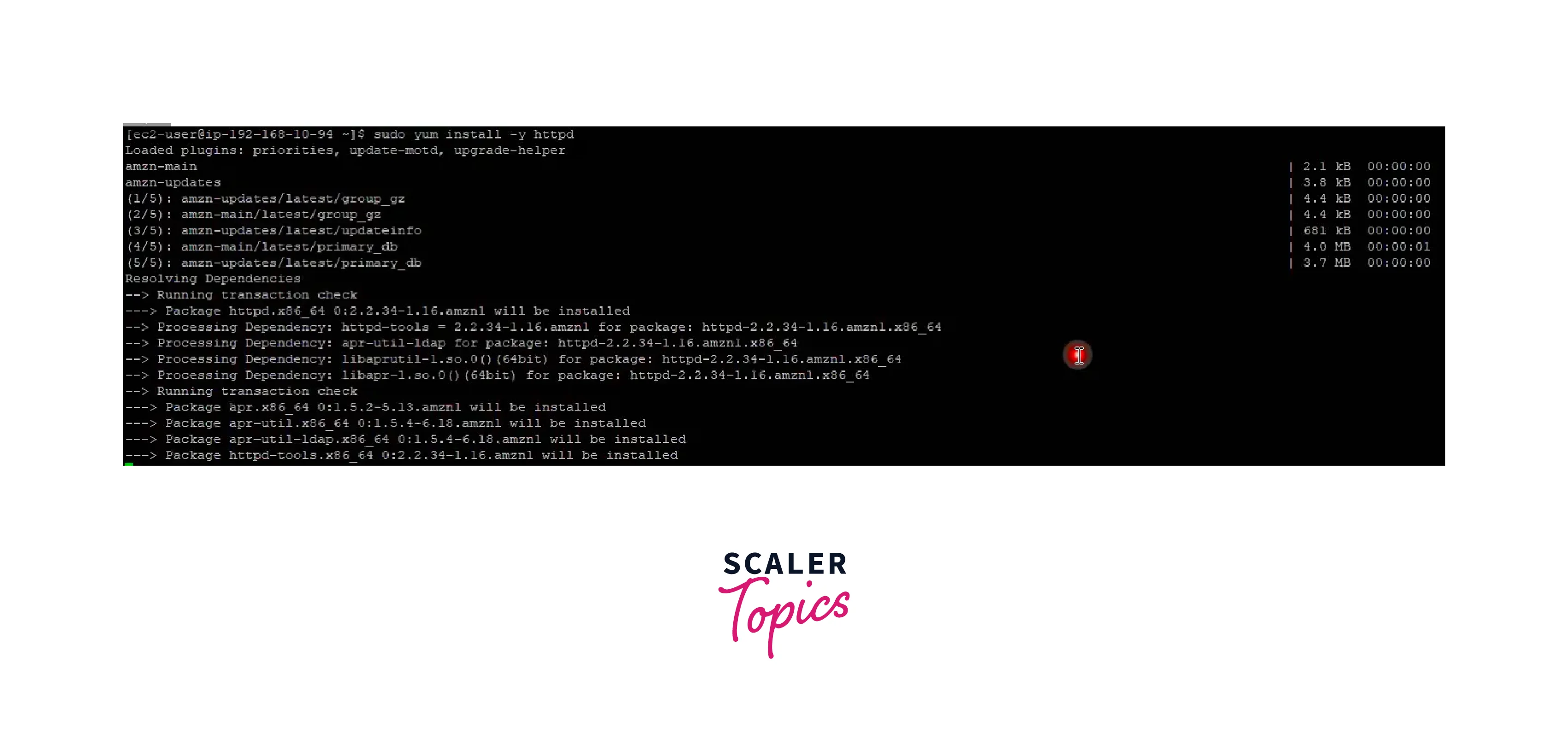
Step - 10: Launching an EC2 Instance in the VPC and Verifying Connectivity
- Download and install the Putty and Puttygen software on your Windows server.
- Convert your PEM file to the PPK extension for use in Putty.
- Establish a connection using Putty or via the provided command for MAC or Linux Machines.
- Once connected to the public instance, transfer your PEM file and access the private instance using the provided commands.
- Attempt internet connectivity from the private instance using the command "yum update -y".
Successful connectivity to the private instance and successful instance updates confirm the successful creation of the VPC, along with the proper configuration of the Public and Private subnets, IGW/NGW, and Route Tables.
If you encounter errors, ensure that the VPC CIDR Range is added to your Security Group settings. Open port 22 for your Home IP address and the VPC CIDR range to enable access to the Public instance.
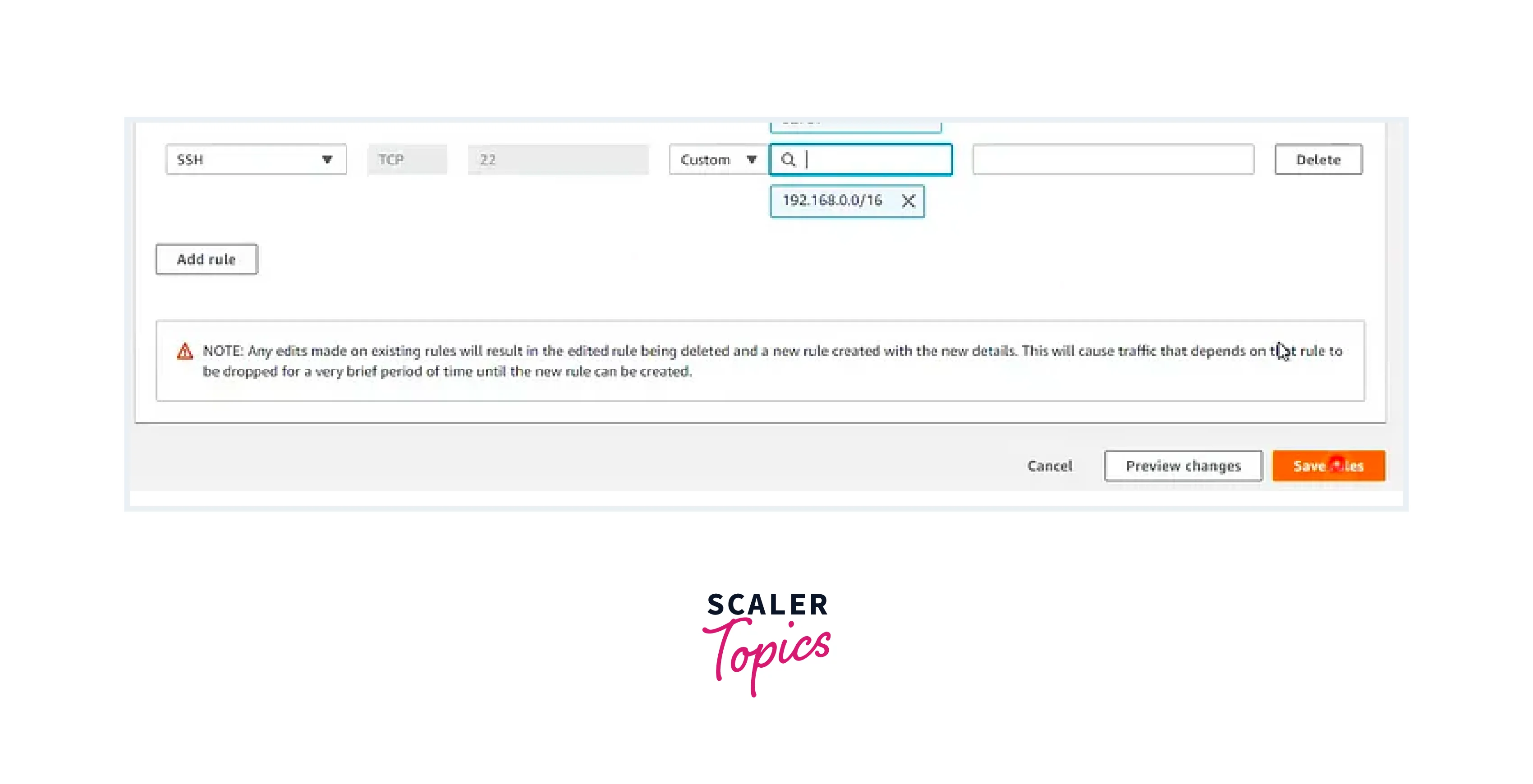
Now, you can access your private instance from your public instances.
Conclusion
- Amazon Virtual Private Cloud (VPC) is a cloud networking service by AWS that lets you create isolated network environments for your resources, providing security and control.
- Amazon VPC consists of subnets, route tables, security groups, network ACLs, internet and VPN gateways, and peering connections. These components enable custom network configurations within AWS cloud.
- Amazon VPC offers features like private networking, subnet isolation, security controls, VPN connections, Direct Connect, VPC peering, NAT gateways, and VPC flow logs for secure and customizable cloud network environments.
- Amazon VPC provides enhanced security, isolation, and control for AWS resources, supports custom network layouts, facilitates hybrid cloud setups, and offers scalability, flexibility, and low-latency connectivity options.
